Hello,
We have an LDAP server (Active Directory) configured on our JSS.
We will move to Azure AD.
For this, we have configured "Cloud Identity Providers" to integrate with our Azure AD.
Everything seems ok with tests. We can query for groups, users and get "true" for membership
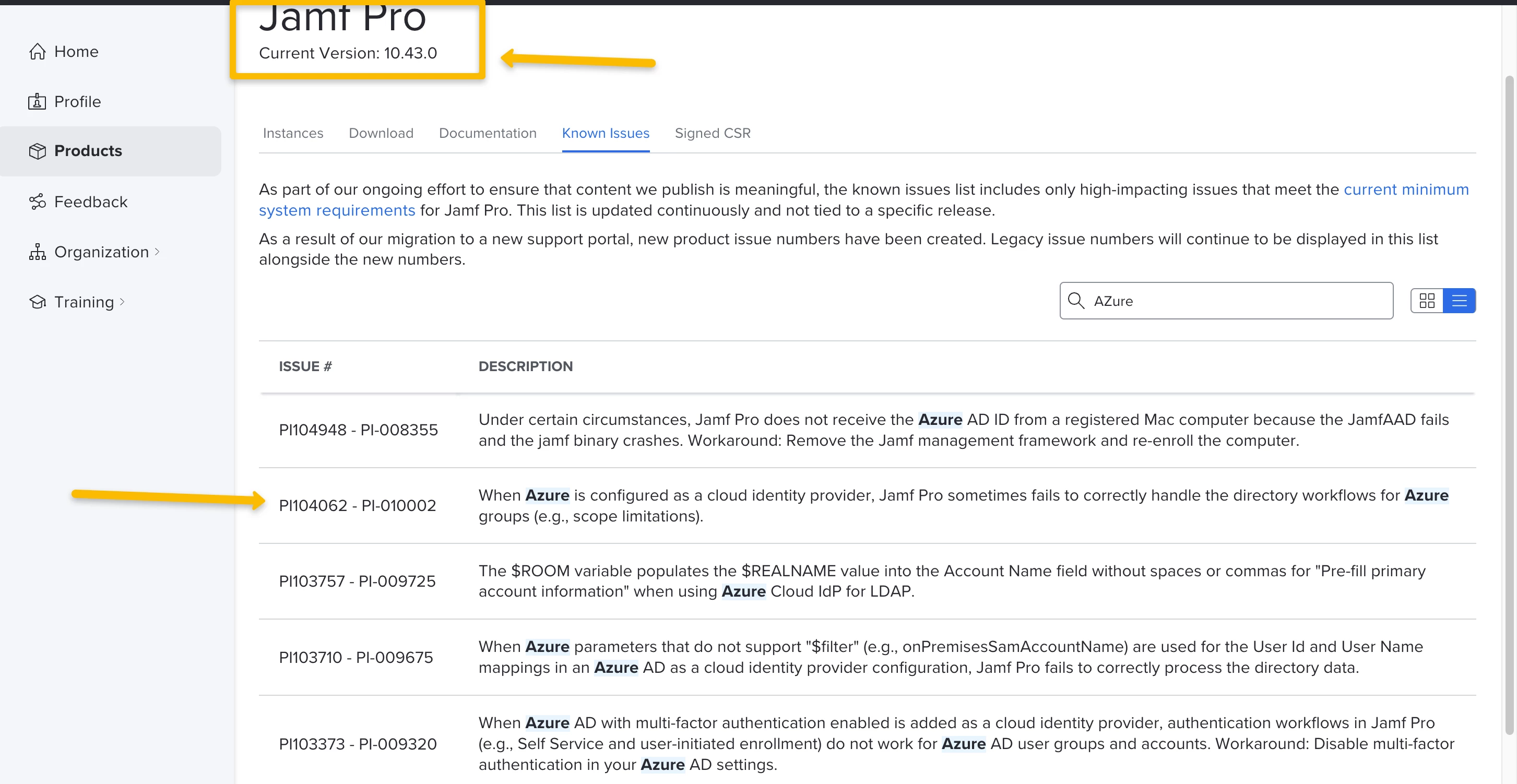
We are trying to scope and limit policies (Self Service) to group memberships from AzureAD (via Cloud Identity Provider). I can search for the group and add it to the Limitations section of the policies.
But when I try to test the policies on computers, the policies are not available when users connect to Self Service using the Azure AD accounts in the target groups.
When we try with Active Directory groups, that works well but not with Azure AD groups.
Do you know if this is normal? Can't scopes with Azure AD groups?
We have Jamf Cloud 10.33.
Thank you for your help