- Jamf Nation Community
- Products
- Jamf Pro
- Jamf 10.33 / AzureAD - Can't use Azure AD groups f...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-10-2021 09:15 AM
Hello,
We have an LDAP server (Active Directory) configured on our JSS.
We will move to Azure AD.
For this, we have configured "Cloud Identity Providers" to integrate with our Azure AD.
Everything seems ok with tests. We can query for groups, users and get "true" for membership
We are trying to scope and limit policies (Self Service) to group memberships from AzureAD (via Cloud Identity Provider). I can search for the group and add it to the Limitations section of the policies.
But when I try to test the policies on computers, the policies are not available when users connect to Self Service using the Azure AD accounts in the target groups.
When we try with Active Directory groups, that works well but not with Azure AD groups.
Do you know if this is normal? Can't scopes with Azure AD groups?
We have Jamf Cloud 10.33.
Thank you for your help
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-10-2021 02:13 PM
Oh i found a PI, maybe you have that problem...
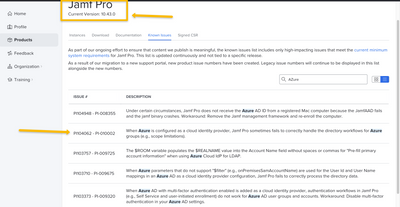
https://account.jamf.com/products/jamf-pro/known-issues
PI-010002
When Azure is configured as a cloud identity provider, Jamf Pro sometimes fails to correctly handle the directory workflows for Azure groups (e.g., scope limitations).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-10-2021 12:55 PM - edited 12-10-2021 12:55 PM
It works for us but there was a Bug < 10.34 where you can only use < 15 Groups. The Pi was now fixed with 10.34
[PI-009318] Fixed an issue that incorrectly restricted the maximum number of Azure cloud IdP groups configured as limitations or exclusions in scope of an object (e.g., a configuration profile).
PI-009318 - “Azure AD - Scoping can’t have more than 15 group limitations / exclusions”
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-10-2021 01:41 PM
Hi @colorenz
Thank you for your answer.
We only use between 1 and 5 groups in scopes per object.
Do you have an LDAP server also configured in addition to an Azure cloud IdP?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-10-2021 01:44 PM
Hey we have swichted from LDAP to Azure cloud IdP only.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-25-2022 03:58 AM
@glpi-ios , Check you single sign on --> User Mapping section --> Jamf Pro User Mapping
select username instead of email.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-21-2022 07:24 AM
Hi @Himanshu_panwar
Thank you for your help.
In fact, we don't use SSO at the moment.
But indeed, with the SSO activated, it works better.
The goal is to make it work without SSO at first (we will activate it later).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-10-2021 01:48 PM
ok, maybe the problem is there then.
We have both configured. We don't dare to remove the link with Active Directory because we don't know the exact consequences with the access to self service, Jamf Remote and Jamf admin.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-10-2021 01:51 PM - edited 12-10-2021 01:51 PM
We use the Azure login for the self service with MFA. We do not have Jamf remote and Jamf Admin in use.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-10-2021 01:55 PM
OK. Thank you for your help.
We will continue the tests by trying to remove the link with our Active Directory.
On the other hand, if I understood correctly, for access to JSS with Azure AD groups, it will be necessary to create standard groups and users in JSS with the same name as the groups and users in Azure AD?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-10-2021 02:01 PM
On the other hand, if I understood correctly, for access to JSS with Azure AD groups, it will be necessary to create standard groups and users in JSS with the same name as the groups and users in Azure AD?
-> Yes 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-10-2021 02:03 PM
Thank you very much for your help.
We will test all of this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-10-2021 02:05 PM
Maybe update to 10.34 first. They PI affected a lot components... SSO Login / Scoping / The Computer Management Tab...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-10-2021 02:08 PM
Thanks for the advice
We updated our dev instance. We will do this on our production.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-10-2021 02:13 PM
Oh i found a PI, maybe you have that problem...
https://account.jamf.com/products/jamf-pro/known-issues
PI-010002
When Azure is configured as a cloud identity provider, Jamf Pro sometimes fails to correctly handle the directory workflows for Azure groups (e.g., scope limitations).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-10-2021 02:21 PM
indeed it appears to be exactly the same symptom.
Well, we just have to hope that Jamf fixes this problem in the next releases.
Thank you for taking the time to research, it's super nice
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-16-2021 08:59 AM - edited 12-16-2021 09:00 AM
Hello,
I have another question.
Is it mandatory to activate SSO to access JSS with an Azure AD account?
Because with SSO, I do it well (by creating the standard groups/users corresponding to the Azure AD groups/users).
But without SSO, this is no longer possible.
It's normal.
Thank you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-16-2021 11:25 AM
Unfortunately, I can't tell you that. We do it that way so that we can also use MFA.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-26-2023 07:32 AM
A year and 10+ Cloud instance upgrades later and the problem hasn't gone away. Can't use Azure AD groups for limitations. And the hassle of re-creating all Azure AD groups in JAMF is not feasible.
Yes mapping is setup correctly
Yes Testing a user/group shows up correctly
Yes we are only using Cloud Azure AD no on-Prem Connection.
Yes we are targeting all computer specific user (Limitation Azure AD Group) no exclusions and the software does not show up in Self-Service.
Has anyone else had any luck? we only use JAMF for macOS not for Iphone/Ipad (Intune only for those)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-06-2023 03:45 AM
Hey.
Yes, this is still an issue. I contacted Jamf Support last month and they replied:
"I have checked the PI104479 and it is still opened. Issue was investigated in depth and it would likely require a significant change across the board in how scoping works and is designed. Our developers team is working on finding the best solution for the situation. Unfortunately, we do not have ETR for the issue yet."
We're now on Jamf Pro 10.44.1 and yet this issue is still there.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-25-2023 01:38 PM
And yet we are now Jamf Pro 11.0, and the issue still has not been addressed..
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-25-2023 02:04 PM
This is working now after having Jamf Cloud Ops turn on a tool. Submit a support ticket to have "the Knob" turned on for your cloud instance. This tool allows for Azure AD group limitations to function for user lookup. It is off by default.
The scenario we tested for:
Users are given licenses for adobe product in Azure
The install application is configured in JAMF PRO for all users limited to the Azure AD group {xxxxxx}
Application installs, and Uninstall break fix only shows for the limiting group set in scope.
Requirements:
Self-service SSO must not be forced {Login Method: Allow users to login | Cannot be set to required}
Additionally, the user must be assigned to the computer in the inventory record as this is what Jamf Pro uses to determine the membership for the scoping.