- Jamf Nation Community
- Products
- Jamf Pro
- Re: Jamf.app is damaged and cannot be opened
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
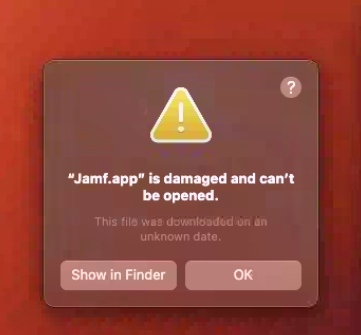
Jamf.app is damaged and cannot be opened
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-03-2023 07:49 AM
Noticed this message on one of my pilot machines today. I had to reinstall the framework via the API. Anyone seen this on version 10.44.1 or 10.45.0 of Jamf Cloud? User is running macOS Ventura 13.2.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-14-2023 05:01 AM
Errr, not yet but thanks for the scare.
Any idea how it happened?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2023 05:43 PM - edited 04-25-2023 05:47 PM
I just got this error after upgrading a Mac from 12.6.4 to 13.3.1.
JAMF Cloud Version: 10.45.0-t1678116779
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-25-2023 05:46 PM
10.45.0-t1678116779
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-26-2023 07:30 AM
@Daniel_Mork , I'm noticing this happening on my clients as they update to 13.3.1 as well. Seems like Ventura's security framework is a bit overzealous.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-26-2023 12:17 PM
Found this on reddit. I wonder if this has anything to do with it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-26-2023 12:29 PM
Something else to help:
How macOS Ventura App Management works and doesn't work (lapcatsoftware.com)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-26-2023 04:23 PM
Thanks for the extra info. A simple un-enrollment and re-enrol back into JAMF has fixed it, but hoping when I start upgrading customers this doesn't happen regularly. Thankfully this was a test machine.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-27-2023 04:09 AM
@Daniel_Mork I would advise opening a ticket with jamf support. Others in the Macadmins Slack are seeing it too. Imagine re-enrolling your fleet on a large scale.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-27-2023 04:09 AM
You can just redeploy the framework via API by the way.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-28-2023 07:37 AM
Did anything new come of this? Seeing some systems just going through enrollment with the issue.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-28-2023 08:54 AM - edited 04-28-2023 09:46 AM
@erickj , this is basically how Apple intends for gatekeeper to behave now. They gave some warning that changes were being made, but they were never transparent about what admins and vendors can and cannot do. From what I've seen in the past, Apple will never change gatekeeper back to the way it was. Admins and vendors just have to adjust the changes that they've made; even though we don't know what they are exactly. (sucks)
I've opened a ticket with Jamf to warn them. This may affect their business.
https://eclecticlight.co/2022/06/17/app-security-changes-coming-in-ventura/
https://www.kolide.com/blog/the-security-and-it-admin-s-guide-to-macos-ventura
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-24-2023 09:35 AM
@bwoods did Jamf ever get back to you about a fix for this? Or is un-enrolling and reenrolling the way to go? I'm now seeing it with an end user in our environment.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-25-2023 12:15 PM - edited 03-11-2024 01:02 PM
@mredell , nothing much came from my ticket. I created an API script that my techs can run from Self Service to redeploy the frame work when they run into the issue. Running "sudo jamf update -forceUpdate" also fixes a majority of these issues. The script below is for instances in which the binary is completely broken. The issue predominantly happens after a binary update.
#!/bin/sh
# Name: redeployJamfFramework.sh
# Author: Brandon Woods
# Date 05/18/2023
# This will allow technicians to redeploy a machine's framework from Self Service without needing to reference the API username or password.
# The script also encodes the API credentials to prevent bad actors from stealing our information.
# Server connection information
url="https://yourinstance.jamfcloud.com"
username="$4"
password="$5"
# local variables
currentUser=$( scutil <<< "show State:/Users/ConsoleUser" | awk '/Name :/ && ! /loginwindow/ { print $3 }' )
currentUID=`id -u "$currentUser"`
# functions
Serial(){
# Prompts the user for serial number that the jamf framework should be redeployed to.
/bin/launchctl asuser "$currentUID" sudo -iu "$currentUser" /usr/bin/osascript <<APPLESCRIPT
set validatedPass to false
repeat while (validatedPass = false)
-- Prompt the user to enter their filevault password
display dialog "Please enter the serial number." with icon file "System:Library:CoreServices:CoreTypes.bundle:Contents:Resources:com.apple.macbookpro-16-space-gray.icns" default answer "" buttons {"Continue"} default button "Continue"
set fvPass to (text returned of result)
display dialog "Please re-enter the serial number." with icon file "System:Library:CoreServices:CoreTypes.bundle:Contents:Resources:com.apple.macbookpro-16-space-gray.icns" default answer "" buttons {"Continue"} default button "Continue"
if text returned of result is equal to fvPass then
set validatedPass to true
fvPass
else
display dialog "The serial numbers you have entered do not match. Please enter matching serial numbers." with title "Serial Number Validation Failed" buttons {"Re-Enter Serial Number"} default button "Re-Enter Serial Number" with icon file "System:Library:CoreServices:CoreTypes.bundle:Contents:Resources:com.apple.macbookpro-16-space-gray.icns"
end if
end repeat
APPLESCRIPT
}
initilizeFrameworkRedeployment(){
# create base64-encoded credentials
encodedCredentials=$( printf "${username}:${password}" | /usr/bin/iconv -t ISO-8859-1 | /usr/bin/base64 -i - )
# request auth token
authToken=$( curl -X POST "${url}/api/v1/auth/token" -H "accept: application/json" -H "Authorization: Basic ${encodedCredentials}" )
# parse authToken for bearertoken, omit expiration
token=$(/usr/bin/awk -F \" 'NR==2{print $4}' <<< "$authToken" | /usr/bin/xargs)
serialNumber=$(Serial)
# Determine Jamf Pro device id
deviceID=$(curl -s -H "Accept: text/xml" -H "Authorization: Bearer ${token}" ${url}/JSSResource/computers/serialnumber/"{$serialNumber}" | xmllint --xpath '/computer/general/id/text()' -)
echo $deviceID
# Redeploye Jamf Framework
curl -X POST "https://${url}/api/v1/jamf-management-framework/redeploy/$deviceID" -H "accept: application/json" -H "Authorization: Bearer $token"
# Invalidate existing token and generate new token
curl -X POST "${url}/api/v1/auth/keep-alive" -H "accept: application/json" -H "Authorization: Bearer ${token}"
}
# Script Execution
initilizeFrameworkRedeployment