- Jamf Nation Community
- Products
- Jamf Pro
- Re: Jamf - Intune - Azure - Device Compliance Cert...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on
07-18-2023
01:24 PM
- last edited on
03-04-2025
06:26 AM
by
![]() kh-richa_mig
kh-richa_mig
We are using Jamf Device Compliance with InTune.
Following this tech paper we have it working fairly well. Technical Paper: Integrating with Microsoft Intune to Enforce Compliance on Mac Computers Managed by...
When the end user goes through computer registration and JamfAAD opens they are prompted to "Always Allow" "Microsoft Workplace Join Key". This is expected and documented here. (Although it would be great to have a smoother workflow)
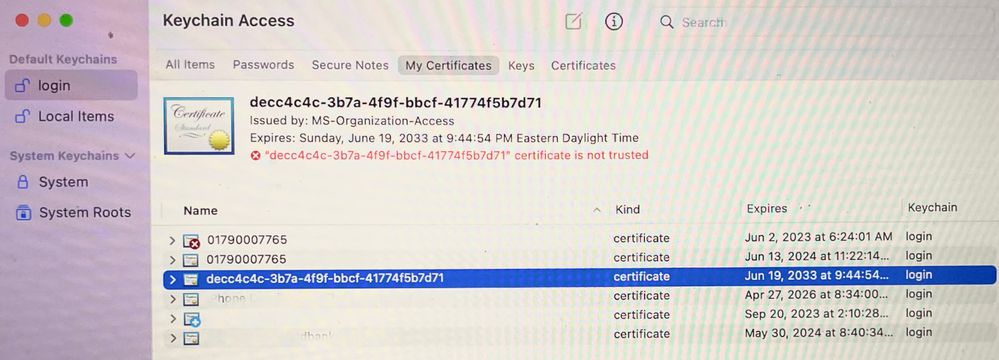
Our issue is the certificate in the login keychain for Device Compliance is not trusted for some reason. (See attached image)
The cert seems to be issued by "MS-Organization-Access" I don't have that CA and our Azure folks don't seem to know about it either.
Thoughts?
Eric
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-18-2023 07:12 PM
@ericbenfer You can ignore the lack of trust for that certificate. While your Mac may not trust it, the Device Compliance integration with Azure AD/Intune does.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-18-2023 07:12 PM
@ericbenfer You can ignore the lack of trust for that certificate. While your Mac may not trust it, the Device Compliance integration with Azure AD/Intune does.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-19-2023 05:07 AM
That is what Microsoft also told us. Although that does not give me a warm and fuzzy feeling.
Every PKI bone in my body wants to fix this. I guess I will have to go against my instincts.
Thanks for confirming @sdagley
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-19-2023 06:51 PM
Hello,
May I ask a question Jamf Pro and having these devices appear within Microsoft Entra?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-07-2023 12:51 AM
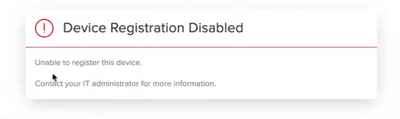
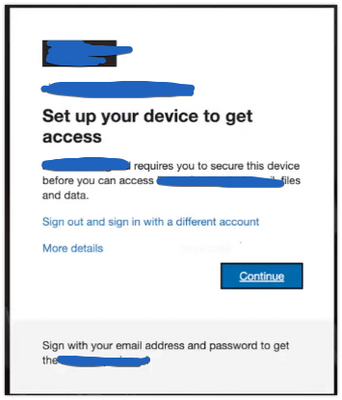
We have registered our Mac fleet in Azure AD and they show up as "Compliant" .. when turn on the compliance policy from Intune and people try to access our company resources they get error messages like this one :
if they use incongnito mode in Chrome for example they get a window to select certificate then they have to enter their login password and hit "always allow" to be able to login successfully to their email for example.
is that the normal behaviour? i'm definitely missing something here so any tips?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-07-2023 04:48 AM
@MacJunior When you say "We have registered our Mac fleet in Azure AD..." does that mean you used a Jamf Pro policy with the Microsoft Device Compliance payload to trigger the enrollment process via the Company Portal app? During that enrollment your users should have gone through the process of always allowing access to the certificate installed during enrollment.
Jamf revised their technical paper of the Device Compliance integration yesterday, and it does clarify some areas that weren't clear in older docs, so it might be helpful to review: https://learn.jamf.com/bundle/technical-paper-microsoft-intune-current/page/Device_Compliance_with_M...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-08-2023 07:26 AM
yeah that explains why a small amount of users are getting blocked while the majority are working fine with 0 issues .. thanks for highlighting this point
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-14-2023 10:26 AM
I have now the second device that becomes "Not compliant" out of no where ! but it's still a member of the compliance criteria smart group that I created, the interesting part is that under the MDM part it says "none" anyone experience such a weird behaviour?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-29-2023 02:05 AM
Yes I am having the same issue.
Raised with JAMF do you have a fix yet?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-01-2023 11:08 PM
Not yet, last thing they adviced is to re-do the integration between Jamf & Entra.
will keep you posted
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-02-2023 05:43 AM - edited 10-02-2023 05:47 AM
For anyone running into the problem with Device Compliance enrollment breaking after the JSS 10.50 update PI113193 is the Product Issue ID that's been assigned for it. You should probably contact your Customer Success rep if you've been impacted.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-21-2023 05:08 PM
Did you ever get a resolution to this issue? I just had lot devices have the same falling out.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-30-2023 07:29 AM
11.01 upgrade should fix