- Jamf Nation Community
- Products
- Jamf Pro
- Re: Jamf - Intune integration on Macbooks with Int...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-13-2022 08:39 AM
Hello,
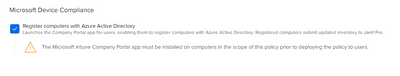
Has anyone been able to run Microsoft Intune Integration on Macbooks with Intel chips and Ventura OS?
We tried to run the policy on Macbooks with Intel chips and Ventura OS but the integration doesn't work and the device will never get registered in AAD.
We also tried with M1 chips, but there is no issue, on macbook with Monterey OS and Intel chip, the integration will work.
The integration will stop at this step on intel devices with Ventura:
We already tried with different browsers, deleting the profiles, using webview and reenrolling the device and everything else that could be found on the internet.
Has anyone been able to make this integration between Jamf and Intune with this scenario?
Thanks,
Traian
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-04-2023 10:53 AM
It seems that the problem is related to an SSO configuration profile. Disabling it and retrying the enrollment on a fresh machine worked. I can't find the correlation between these 2.
If you have a SSO configuration profile in place, try to remove it from the target device and retry. Also delete the record of the device from AAD first.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-13-2022 10:47 AM
Just tested this on an Intel device and seeing the same.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-13-2022 11:56 AM
You may want to double check with JAMF Support, but for me, Conditional Access is working for macOS and it looks like Device Compliance is for iOS. That would explain why Apple Silicon Macs would enroll over Intel.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-13-2022 11:59 AM
We have raised a support ticket to Jamf and Microsoft as well, so far we don't have a fix. The only workaround we have is to downgrade the OS system to Monterey, but it's painful and time consuming.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-16-2022 08:56 AM
Just following up as I haven't had any response from support. Have you?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-17-2022 03:53 AM
We didn't receive any updates, but we spoke with Apple and they confirmed that this is something wrong from Jamf side. We have an escalated ticket to Microsoft Azure team as well.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-04-2023 10:53 AM
It seems that the problem is related to an SSO configuration profile. Disabling it and retrying the enrollment on a fresh machine worked. I can't find the correlation between these 2.
If you have a SSO configuration profile in place, try to remove it from the target device and retry. Also delete the record of the device from AAD first.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-04-2023 11:14 AM
Yeap, worked on this yesterday and I came to the same conclusion. I've provided all the info to our support ticket.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-02-2023 10:14 AM
Thanks for that! I just spent two days looking for a solution for this and finally found this thread. I feel like this should be addressed in the documentation. We use conditional access to block unregistered computers and this was a massive roadblock in rolling out Jamf. That was crazy frustrating.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-13-2022 01:57 PM - edited 12-13-2022 01:59 PM
How is your connector setup? Did you use the cloud connector to connect macOS and Intune Integration under Conditional Access? And did you set up the partner connector in End Point Manager or was it done for you? Just asking as we are not seeing issues registering Ventura laptops.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-13-2022 02:00 PM
Yes, we are using cloud connector, after completing the user enrollment, we are running the integration script from Self Service and the device should receive an Azure AD and check for compliance status.
We also tried with to turn off the conditional access policy for the specific user, but didn't work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-13-2022 02:08 PM
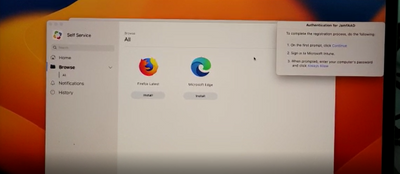
I also built the SS policy. I leave Company Portal logged into and then click on the SS policy. I am presented with the CP app, click log in, then I see the prompt you see with Continue but then I get a certificate prompt. Once trusted our clients are good to go. We do not have any additional CAP policies set on Intune registration. We do use a basic compliance policy that needs to be met.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-13-2022 02:12 PM
Does this applies to Macbooks with intel chips and Ventura OS?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-13-2022 02:17 PM
Sorry did not reply to you directly. I am a little under the weather. this one might sound silly but you're also not trying to register already registered devices?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-13-2022 02:22 PM
This might help you in your quest for a solution:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-13-2022 02:13 PM
Can you verify the app in Intune for the connector has the correct permissions:
The Jamf Pro enterprise application in Azure has the wrong permission or more than one permission. When you create the app in Azure, you must remove all default API permissions and then assign Intune a single permission of update_device_attributes.
This would cause the registration to fail.
I am guessing your MS licensing is at least a P1 and your Jamf clients have valid licenses?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-13-2022 04:43 PM
To weigh in, I’m seeing the issue as well and it works as expected for Intel devices with Monterey, and for Apple Silicon Devices with Ventura but NOT for Intel devices on Ventura.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-15-2022 01:14 AM
For us, for ages, we've always failed on the first attempt - worst case the JamfAAD app hangs on the first try and has to be forced-quit. On the second attempt it works. I reached out to Jamf Support who wanted full system logs, which I did not give them.
Since then, I've also implemented the web app support in JamfAAD, but looking at the suggestions above it's possible your problem is competely different.
It just seems like you're not getting the last login window from a browser or WebView, which is what I had.