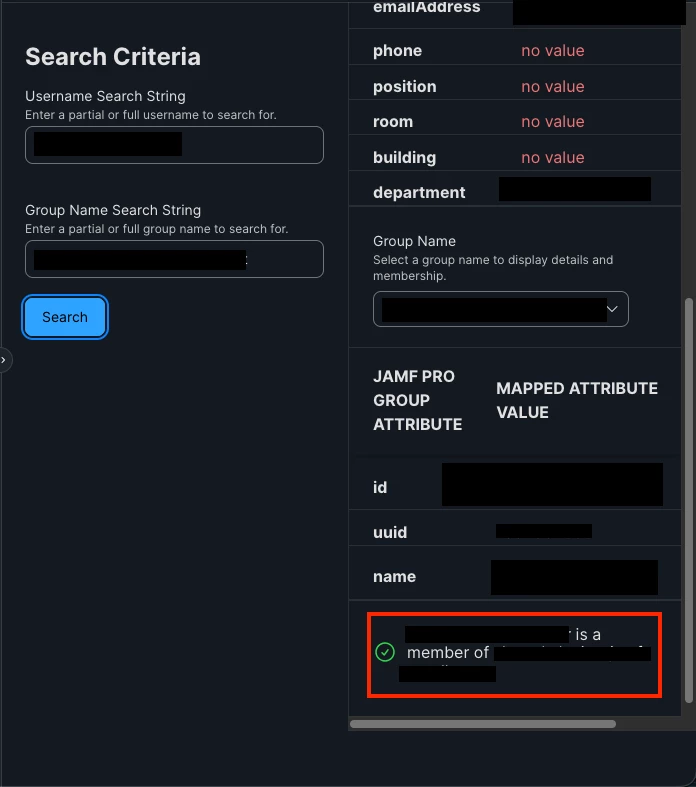
So we have Google LDAP connected to Jamf. It's working great for populating User & Location information, etc. However, I'd really like to leverage 'Directory Service User Group' to scope stuff. It just doesn't seem to be working. I've tried to do some reading and I've found people saying it's unreliable. When I go to Cloud Identity Providers > Google LDAP > and do a lookup of myself or others + and also search for a group name - it correctly returns that I'm a member of ___-staff group.
There's a specific policy I want to exclude for this staff group. I can go to exclusions for this policy > Directory Service User Groups > search for the staff group I'm apart of > it finds it, and I add it. After doing that, I still see my computer as pending like it's still in the scope. User & Location info is accurate, my local account matches LDAP user name, etc.
How are people future-proofing scoping?
My other option is to hand-build Departments in Jamf that match Department values from Google/LDAP, I think that works. But I'd rather leverage existing LDAP Groups, that Jamf is correctly seeing I'm apart of.