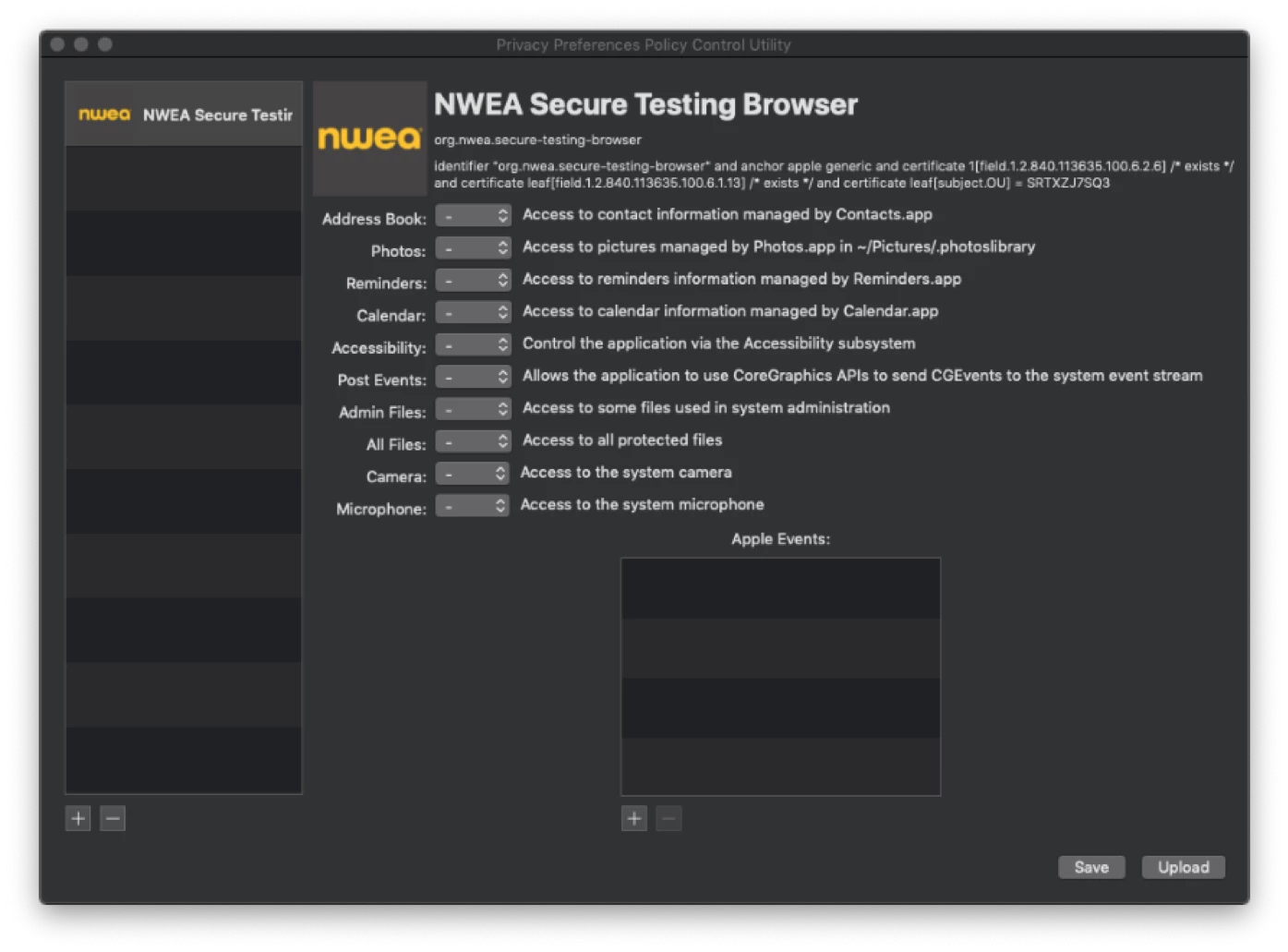
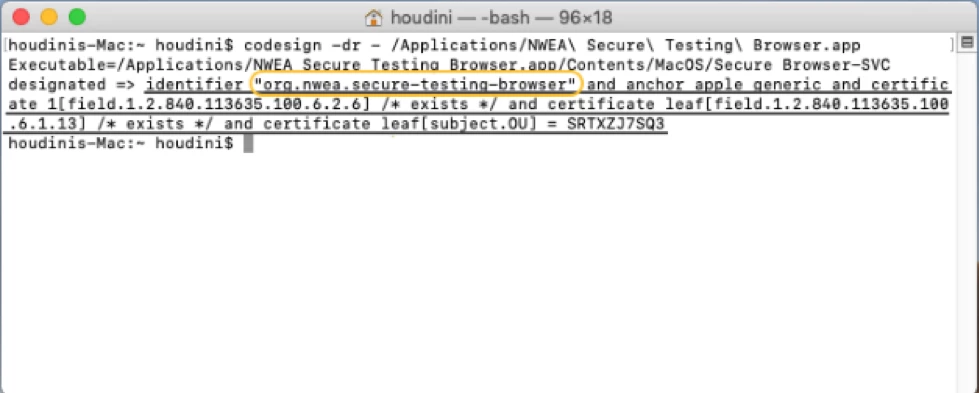
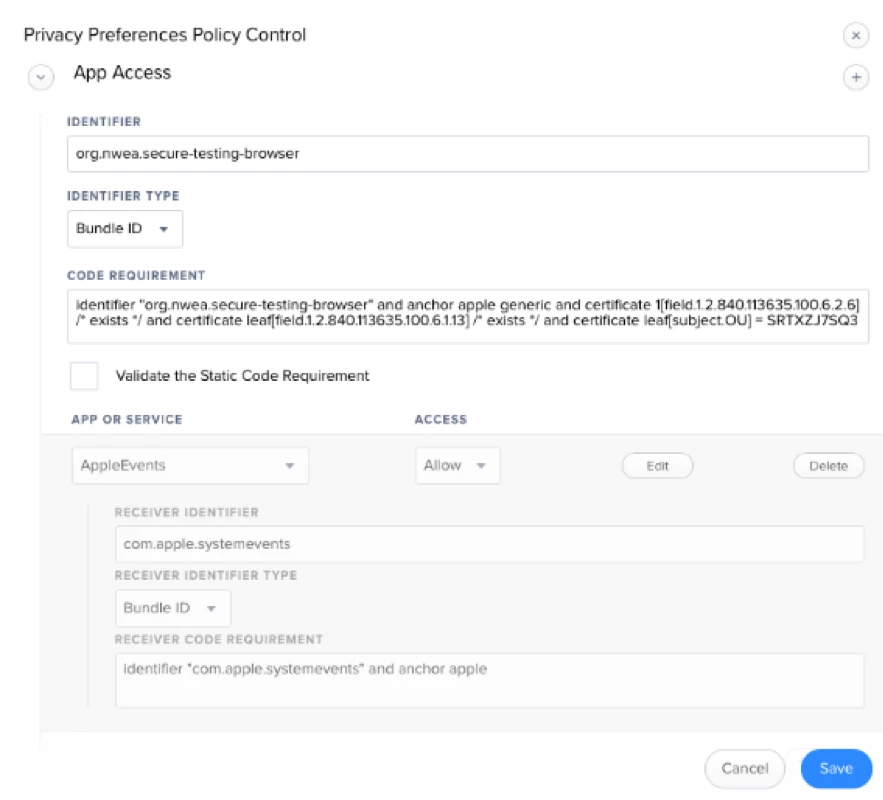
Hi,
I am trying to create a PPPC config for NWEA. I downloaded the PPPC Utility and tried to add the NWEA app from /Applications but it will not add it to the PPPC Utility. I have tried adding it with the + and also dragging it in. Other apps seem to add fine. Any ideas what's going on?