- Jamf Nation Community
- Products
- Jamf Pro
- OS X 10.10.5 available
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
OS X 10.10.5 available
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-13-2015 10:13 AM
http://9to5mac.com/2015/08/13/os-x-10-10-5/
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-13-2015 10:41 AM
These are the security fixes -
Safari 8.0.8, Safari 7.1.8, and Safari 6.2.8 is now available and
addresses the following:
Safari Application
Available for: OS X Mountain Lion v10.8.5, OS X Mavericks v10.9.5,
and OS X Yosemite v10.10.4
Impact: Visiting a malicious website may lead to user interface
spoofing
Description: A malicious website could open another site and prompt
for user input without a way for the user to tell where the prompt
came from. The issue was addressed by displaying the prompt origin to
the user.
CVE-ID
CVE-2015-3729 : Code Audit Labs of VulnHunt.com
WebKit
Available for: OS X Mountain Lion v10.8.5, OS X Mavericks v10.9.5,
and OS X Yosemite v10.10.4
Impact: Visiting a maliciously crafted website may lead to an
unexpected application termination or arbitrary code execution
Description: Multiple memory corruption issues existed in WebKit.
These issues were addressed through improved memory handling.
CVE-ID
CVE-2015-3730 : Apple
CVE-2015-3731 : Apple
CVE-2015-3732 : Apple
CVE-2015-3733 : Apple
CVE-2015-3734 : Apple
CVE-2015-3735 : Apple
CVE-2015-3736 : Apple
CVE-2015-3737 : Apple
CVE-2015-3738 : Apple
CVE-2015-3739 : Apple
CVE-2015-3740 : Apple
CVE-2015-3741 : Apple
CVE-2015-3742 : Apple
CVE-2015-3743 : Apple
CVE-2015-3744 : Apple
CVE-2015-3745 : Apple
CVE-2015-3746 : Apple
CVE-2015-3747 : Apple
CVE-2015-3748 : Apple
CVE-2015-3749 : Apple
WebKit
Available for: OS X Mountain Lion v10.8.5, OS X Mavericks v10.9.5,
and OS X Yosemite v10.10.4
Impact: A malicious website may trigger plaintext requests to an
origin under HTTP Strict Transport Security
Description: An issue existed where Content Security Policy report
requests would not honor HTTP Strict Transport Security. This issue
was addressed through improved HTTP Strict Transport Security
enforcement.
CVE-ID
CVE-2015-3750 : Muneaki Nishimura (nishimunea)
WebKit
Available for: OS X Mountain Lion v10.8.5, OS X Mavericks v10.9.5,
and OS X Yosemite v10.10.4
Impact: Image loading may violate a website's Content Security
Policy directive
Description: An issue existed where websites with video controls
would load images nested in object elements in violation of the
website's Content Security Policy directive. This issue was addressed
through improved Content Security Policy enforcement.
CVE-ID
CVE-2015-3751 : Muneaki Nishimura (nishimunea)
WebKit
Available for: OS X Mountain Lion v10.8.5, OS X Mavericks v10.9.5,
and OS X Yosemite v10.10.4
Impact: Content Security Policy report requests may leak cookies
Description: Two issues existed in how cookies were added to Content
Security Policy report requests. Cookies were sent in cross-origin
report requests in violation of the standard. Cookies set during
regular browsing were sent in private browsing. These issues were
addressed through improved cookie handling.
CVE-ID
CVE-2015-3752 : Muneaki Nishimura (nishimunea)
WebKit Canvas
Available for: OS X Mountain Lion v10.8.5, OS X Mavericks v10.9.5,
and OS X Yosemite v10.10.4
Impact: A malicious website may exfiltrate image data cross-origin
Description: Images fetched through URLs that redirected to a
data:image resource could have been exfiltrated cross-origin. This
issue was addressed through improved canvas taint tracking.
CVE-ID
CVE-2015-3753 : Antonio Sanso and Damien Antipa of Adobe
WebKit Page Loading
Available for: OS X Mountain Lion v10.8.5, OS X Mavericks v10.9.5,
and OS X Yosemite v10.10.4
Impact: Cached authentication state may reveal private browsing
history
Description: An issue existed in caching of HTTP authentication.
Credentials entered in private browsing mode were carried over to
regular browsing which would reveal parts of the user's private
browsing history. This issue was addressed through improved caching
restrictions.
CVE-ID
CVE-2015-3754 : Dongsung Kim (@kid1ng)
WebKit Process Model
Available for: OS X Mountain Lion v10.8.5, OS X Mavericks v10.9.5,
and OS X Yosemite v10.10.4
Impact: Visiting a malicious website may lead to user interface
spoofing
Description: Navigating to a malformed URL may have allowed a
malicious website to display an arbitrary URL. This issue was
addressed through improved URL handling.
CVE-ID
CVE-2015-3755 : xisigr of Tencent's Xuanwu Lab
Safari 8.0.8, Safari 7.1.8, and Safari 6.2.8 may be obtained from
the Mac App Store.
Information will also be posted to the Apple Security Updates
web site: https://support.apple.com/kb/HT201222
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-13-2015 11:14 AM
Combo Update is here:
https://support.apple.com/kb/DL1832?locale=en_US
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-13-2015 11:24 AM
Does anyone know yet if the issue released here is addressed in this version? I had heard that the latest betas of 10.10.5 fixed the issue, but I haven't installed this yet to see. Wondering if anyone has already done the work of testing and can confirm/deny any fixing, etc.
If this does plug this very serious issue, I think we'll be fast tracking this update into production and Self Service pretty quickly.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-13-2015 11:26 AM
@mm2270 Yep, that's definitely fixed in the release.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-13-2015 11:27 AM
Awesome! Thanks for the quick confirmation @RobertHammen Time to test and get prepped then!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-13-2015 11:29 AM
Also OS X Server -
OS X Server v4.1.5 is now available and addresses the following:
BIND
Available for: OS X Yosemite v10.10.5 or later
Impact: A remote attacker may be able to cause a denial of service
Description: An assertion issue existed in the handling of TKEY
packets. This issue was addressed by updating BIND to version
9.9.7-P2.
CVE-ID
CVE-2015-5477
OS X Server v4.1.5 may be obtained from the Mac App Store.
Information will also be posted to the Apple Security Updates
web site: https://support.apple.com/kb/HT201222
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-13-2015 07:55 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
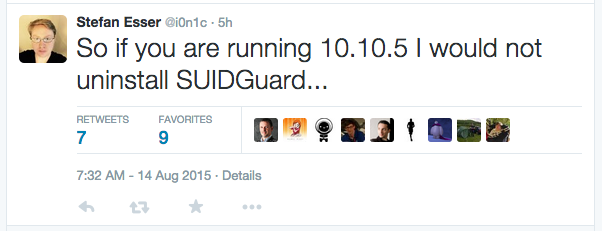
Posted on 08-14-2015 06:52 AM
So... what is meant exactly by his tweet? Everything I've read so far indicates this was patched in 10.10.5. Is Stefan just spreading FUD here or is there still a legitimate concern? I just looked at his Twitter feed and all I see are cryptic posts like the one above, no real indication of anything substantial. I have not been able to find any posts/evidence yet that this update doesn't actually fix the issue, or if it introduces extra issues.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-14-2015 10:53 AM
I tested against it this morning, and definitely seems to be fixed in our ENV
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-14-2015 12:27 PM
"Hmm, so Apple released 10.10.5 fixed some bugs and made another security problem worse than before"
Sounds like there's another vulnerability. Pretty unlikely Apple releases another dot release of 10.10, so we may see a Security Update 2015-001 for Yosemite if this is deemed to be critical.