So i get the following pop up on a new Mojave build.
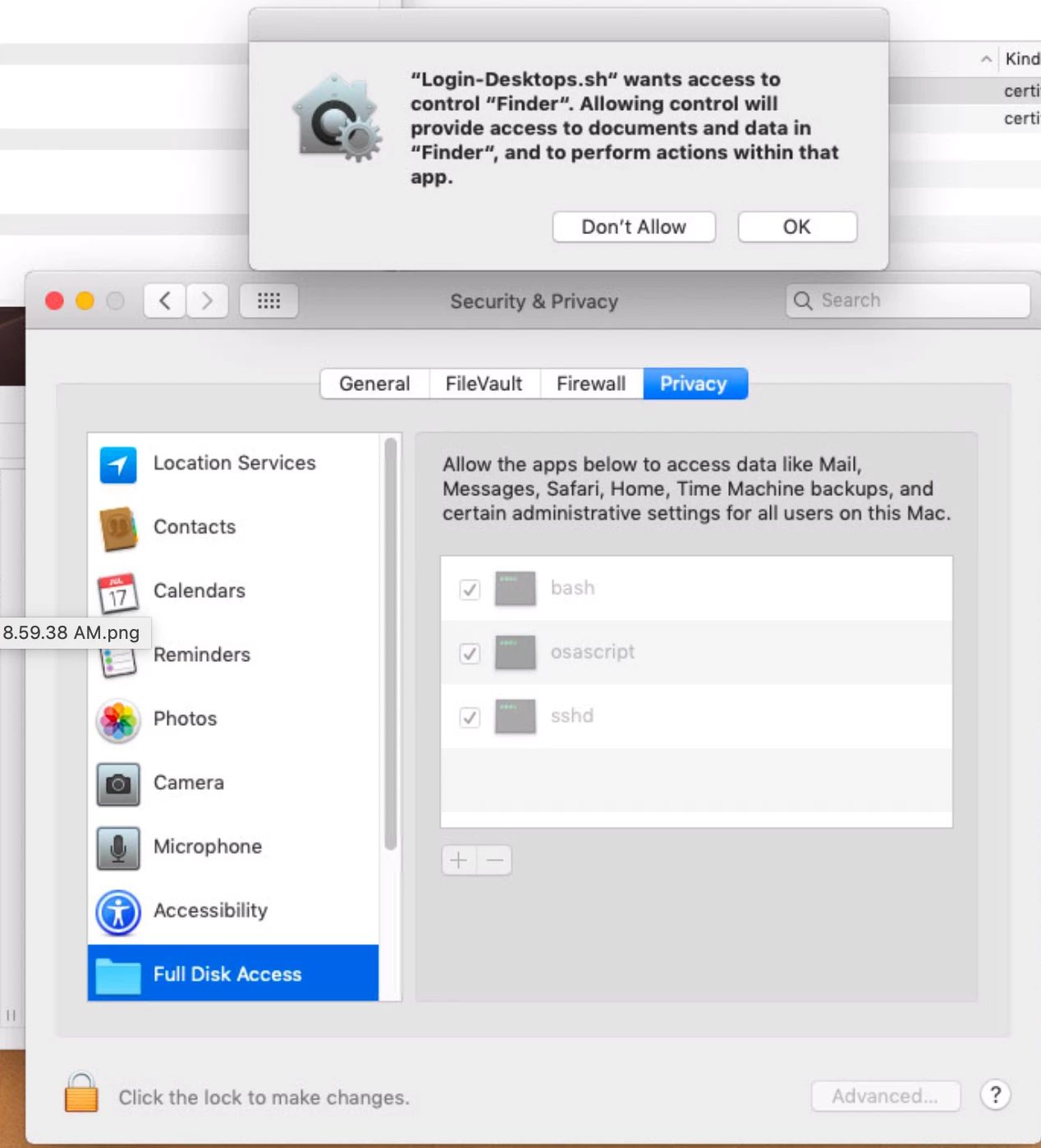
I even allowed bash and osa script bianries to have full disk access (thats what My script does, basically mounts some network shares for me at user login)
I ran thru trying to codesign my script.sh file whitelist it using various methods
using this tool after i code signed the script to whitelist https://github.com/carlashley/tccprofile
looked at the following urls in depth, but nothing seems to work for my pop up
https://derflounder.wordpress.com/2018/08/31/creating-privacy-preferences-policy-control-profiles-for-macos/
The reference below doesn't talk about how to allow access to finder, just some other apps and system files.
https://developer.apple.com/enterprise/documentation/Configuration-Profile-Reference.pdf
I can post the script but i dont think there is an issue with the script since it has worked fine for the past year or so on 10.12.6 and 10.13.3
Unless there is a better way to mount network shares based on teh mobile account logged in.
I also contacted Jamf and Apple.
Jamf said to use their utility
https://github.com/jamf/PPPC-Utility
Apple engineers are still "researching" a way around this pop up.
Any help is appreciated.
-Peter




