Hi everybody,
I would like to have your opinion, and help if you can, about DEP issue I have.
I can't use DEP for now.
it never worked and nobody seems to find a solution.
My computers are register in DEP and everything is configured on Jamf (PreStage Enrollments).
When I prepare a computer, DEP seems to be ok but enrollment is not done.
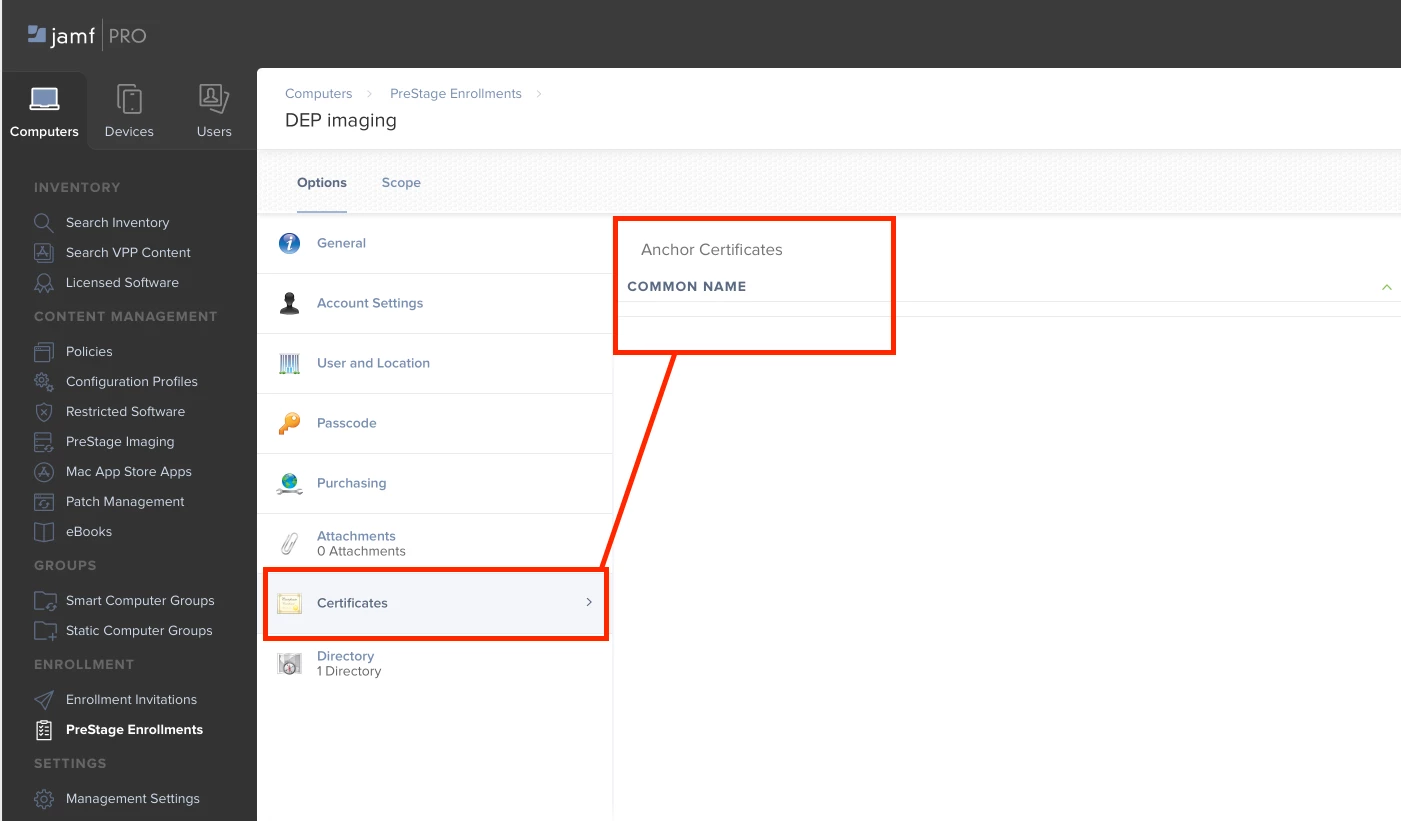
For enrollment to occur, our computers must have internal certificates (root and intermediate).
The problem is that as long as we do not install these certificates, communication with JSS will not happen and therefore by possible enrollment.
If you have to install the certificates manually, the interest of the DEP disappears.
In addition, the settings of "PreStage Enrollments" are not done (creation of an admin account for example).
If you know a solution, I take it with pleasure :-)