Hello all,
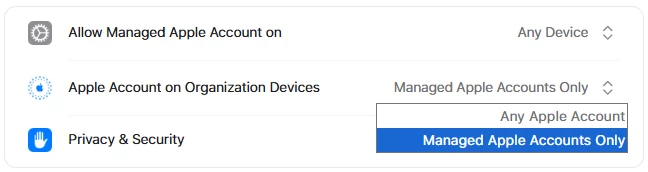
I know there have been a couple of topics around this already but I can't seem to find a solid solution for this. We are a university and have both user assigned and public apple computers and laptops. I would like todo one of the following:
1. Prevent users from login into their personal apple ID's and lock the devices to only use our ITS apple ID (make sure they can not log out of it).
2. Simply block the ability to sign into any apple ID.
3. Force sign out users already signed into their personal apple ID's.
I have tried to set this up using a configuration profile under Restrictions > Preferences but this does not work (once the profile is applied the section is still visible). I also don't like the restrictions method as this includes many other options I don't want to use (in Applications, Widgets, Media, ect).
We are using Jamf PRO and Apple School Manager.
Thanks!