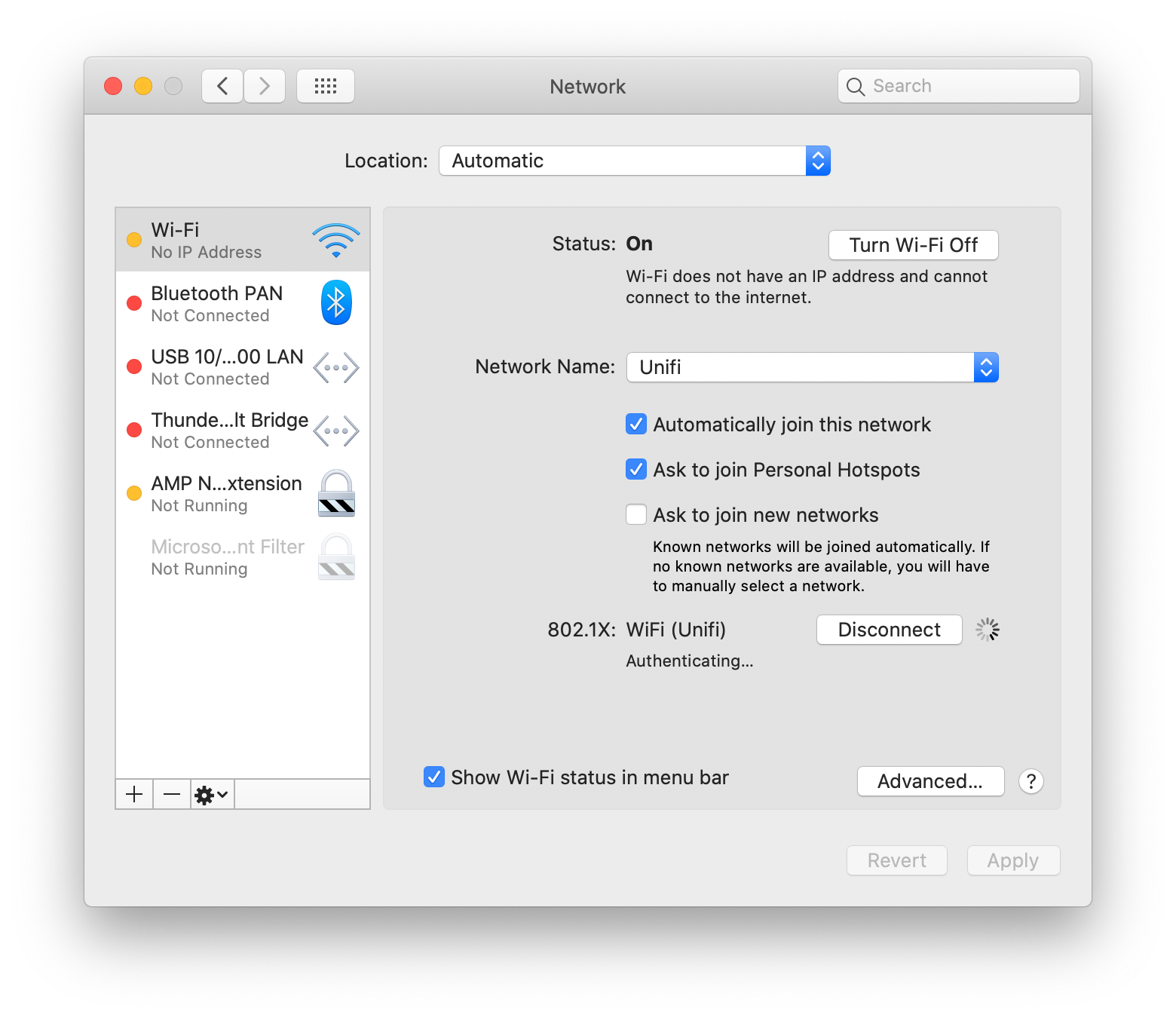
Long story short, a few months ago we changed CA's and found ourselves stuck with updating the existing wifi configuration profile. We ended up having to change the entire company's wifi SSID to get around this. (more info here - https://www.jamf.com/jamf-nation/discussions/23826/config-profile-question)
We ultimately decided to deploy the wifi config profile through a script using the "profiles -I -F" command instead of configuration profile for fear of getting stuck in the same situation. While the cutover to the new CA server went relatively seamless, we don't have a seamless way of updating the wireless certificates. (it only works if the user goes through Self Service)
What I'm looking for:
I'm looking for a way to have seamless wifi certificate renewals.
Here's the problem:
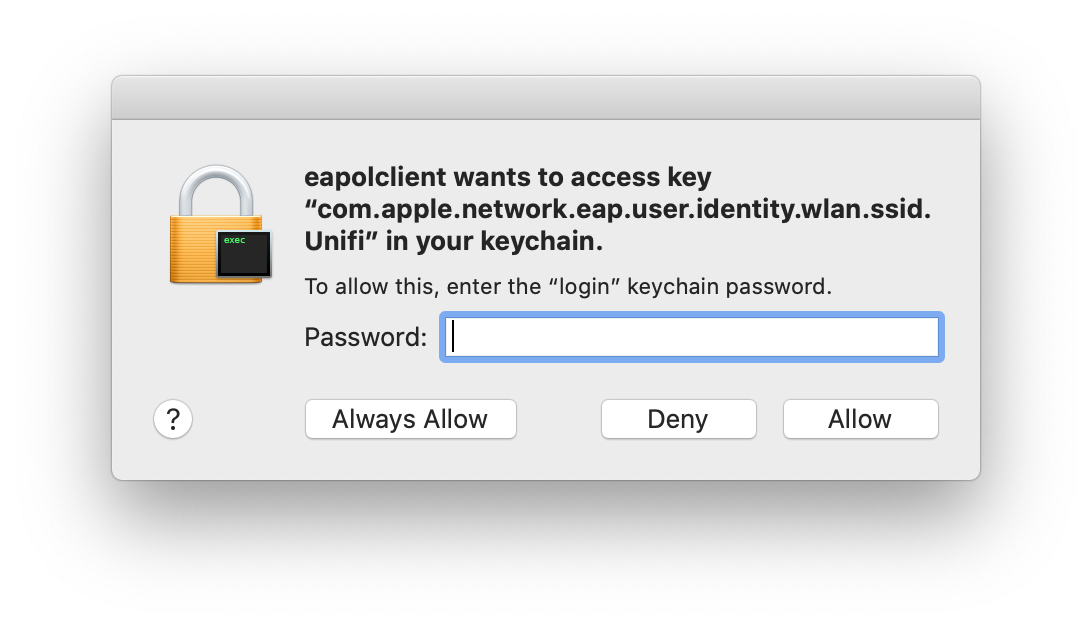
Running the script as the logged on user through Self Service works 100%. It'll remove the old wifi cert, download a new wifi cert, then It'll create the com.apple.network.eap.user.identity.wlan.ssid.SSIDHERE in the user's keychain properly.
When pushing the same exact script from Casper, it'll remove the old wifi cert, download a new wifi ciert, but the com.apple.network.eap.system.identity.wlan.ssid.SSIDHERE keychain entry is created in the system keychain. The user is unable to connect to wifi with this setting.
I've tried multiple variations of things for days and can't get it to work. How are people managing 802.1x wifi profiles and how are you renewing them?
#!/bin/sh
# Wifi Self Service.sh
# Script to connect to SSID
# Brandon Wong 4/24/2017
function connectWifi (){
/usr/bin/profiles -I -F /Library/LC/LC-#.mobileconfig
Cert="$compname.DOMAIN.com"
#security set-identity-preference -n -s "com.apple.network.eap.user.identity.wlan.ssid.SSID" /Library/Keychains/System.keychain
security set-identity-preference -c "$Cert" -s "com.apple.network.eap.user.identity.wlan.ssid.SSID" /Library/Keychains/System.keychain
#sudo security set-identity-preference -c "$Cert" -s "com.apple.network.eap.user.identity.wlan.ssid.SSID" /Library/Keychains/System.keychain
wservice=`/usr/sbin/networksetup -listallnetworkservices | grep -Ei '(Wi-Fi|AirPort)'`
whwport=`networksetup -listallhardwareports | awk "/$wservice/,/Ethernet Address/" | awk 'NR==2' | cut -d " " -f 2`
hwports=`networksetup -listallhardwareports | awk '/Hardware Port: Wi-Fi/,/Ethernet/' | awk 'NR==2' | cut -d " " -f 2`
wirelessnw=`networksetup -getairportnetwork $hwports | cut -d " " -f 4`
sleep 10
if [[ $wirelessnw == "SSID" ]]; then
echo "Connected to SSID"
else
echo "Machine is not connected to SSID. Checking identity preference"
security get-identity-preference -s "com.apple.network.eap.user.identity.wlan.ssid.SSID" /Library/Keychains/System.keychain
fi
}
function bindToDomain (){
# Unbind machine from domain
dsconfigad -remove -force -username macimaging -password $Pass
sleep 10
echo "Unbinding"
killall opendirectoryd
sleep 5
## Testing has shown that unbinding twice may be necessary.
dsconfigad -remove -force -username username -password $Pass &> /dev/null
sleep 10
echo "Unbinding twice just incase"
## Begin rebinding process
#Basic variables
computerid=`scutil --get LocalHostName`
domain=SSID.us
udn=
OU="CN=Computers,DC=Corp,DC=#,DC=com"
#Advanced variables
alldomains="disable"
localhome="enable"
protocol="smb"
mobile="enable"
mobileconfirm="disable"
user_shell="/bin/bash"
admingroups="Corp"
namespace="domain"
packetsign="allow"
packetencrypt="allow"
useuncpath="disable"
passinterval="90"
# Bind to AD
dsconfigad -add $domain -alldomains $alldomains -username $udn -password $Pass -computer $computerid -ou "$OU" -force -packetencrypt $packetencrypt
sleep 1
echo "Rebinding to AD and setting advanced options"
#set advanced options
dsconfigad -localhome $localhome
sleep 1
dsconfigad -groups "$admingroups"
sleep 1
dsconfigad -mobile $mobile
sleep 1
dsconfigad -mobileconfirm $mobileconfirm
sleep 1
dsconfigad -alldomains $alldomains
sleep 1
dsconfigad -useuncpath "$useuncpath"
sleep 1
dsconfigad -protocol $protocol
sleep 1
dsconfigad -shell $user_shell
sleep 1
dsconfigad -passinterval $passinterval
sleep 1
#dsconfigad adds "All Domains"
# Set the search paths to "custom"
dscl /Search -create / SearchPolicy CSPSearchPath
dscl /Search/Contacts -create / SearchPolicy CSPSearchPath
sleep 1
# Add the "XXXX.XXXXX.us" search paths
dscl /Search -append / CSPSearchPath "/Active Directory/CORP/DOMAIN.com"
dscl /Search/Contacts -append / CSPSearchPath "/Active Directory/CORP/DOMAIN.com"
sleep 1
# Delete the "All Domains" search paths
dscl /Search -delete / CSPSearchPath "/Active Directory/CORP/All Domains"
dscl /Search/Contacts -delete / CSPSearchPath "/Active Directory/CORP/All Domains"
dscl /Search -delete / CSPSearchPath "/Active Directory/CORP/#.us"
dscl /Search/Contacts -delete / CSPSearchPath "/Active Directory/CORP/#.us"
dscl /Search -delete / CSPSearchPath "/Active Directory/CORP/#.us"
dscl /Search/Contacts -delete / CSPSearchPath "/Active Directory/CORP/#.us"
sleep 1
# Restart opendirectoryd
killall opendirectoryd
sleep 3
dependenciesCheck
}
function dependenciesCheck(){
# Check for an AD computer object
ad_computer_name=`dsconfigad -show | grep "Computer Account" | awk '{print $4}'`
compObj=`dscl /Active Directory/CORP/All Domains read /Computers/$ad_computer_name RecordName | awk '{print $2}'`
if [ $ad_computer_name = $compObj ]; then
echo Matching AD object exists. Continue script...
# Make sure mobileconfig exists
file=/Library/LC/NAMEOFCONFIG.mobileconfig
if [ -f "$file" ]; then
connectWifi
else
echo Profile missing. Downloading profile
jamf policy -trigger *TRIGGER*
if [ -f "$file" ]; then
connectWifi
else
echo Cannot connect to *SSID*. Mobileconfig is missing.
exit 1
fi
fi
else
echo "Missing Domain Binding"
bindToDomain
fi
}
# HARDCODED VALUES ARE SET HERE
Pass=""
# CHECK TO SEE IF VALUES WERE PASSED FOR $4, AND IF SO, ASSIGN THEM
if [ "$4" != "" ] && [ "$Pass" == "" ]; then
Pass=$4
fi
# Check to make sure Pass variable was passed down from Casper
if [ "$Pass" == "" ]; then
echo "Error: The parameter 'Pass' is blank. Please specify a value."
exit 1
fi
# Variables
currUser=`stat -f "%Su" /dev/console`
echo "Current user is $currUser"
# Cleanup duplicate machine certificates
compname=`dsconfigad -show | grep "Computer Account" | awk '{print $4}' | sed 's/.$//'`
Certs="$compname.#.com"
hashes=$(security find-certificate -c "$Certs" -a -Z|grep SHA-1|awk '{ print $NF }')
for hash in $hashes; do
echo deleting duplicate certs $hash
sudo security delete-certificate -Z $hash
done
# Check dependencies
dependenciesCheck
exit 0