I noticed in previous security updates someone has taken the time to start a thread about the matter and way to go about deploying it. Since I haven't seen that yet today I thought I'd start one to get the ball rolling.
Question
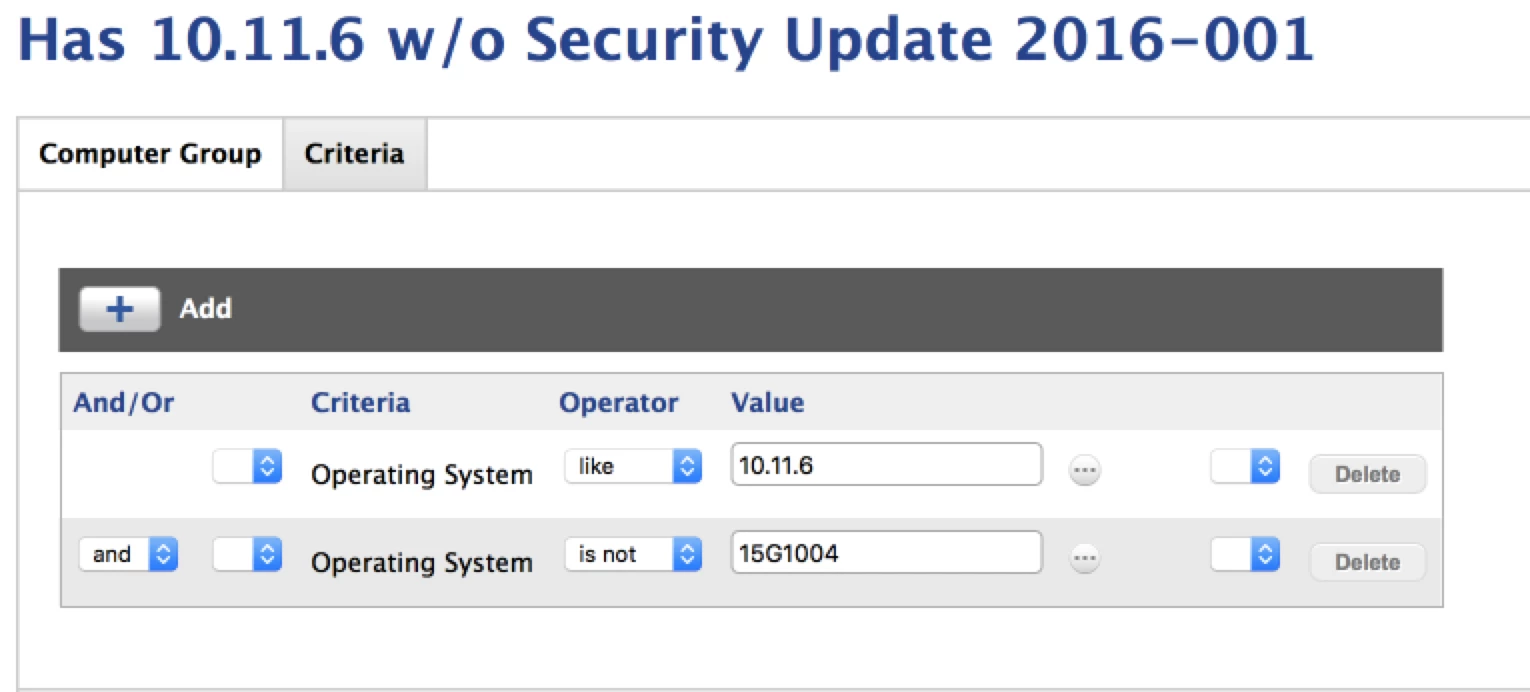
Security Update 2016-001 El Capitan & Security Update 2016-005 Yosemite
 +3
+3Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.