- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-03-2023 12:59 PM
I'm new to Jamf Pro, and I asked our on-boarding solutions expert on some best practices for creating User Groups in Jamf to limit access for our Tier 1 IT Staff, but they were not to helpful.
Are there any good tips on what permissions to setup for a least privileged model within Jamf Pro for our IT Staff?
Ideally a setup that goes from Tier 1 (least privileged) to Tier 3 (most privileged) in terms of what these users can get to and modify on the Jamf Pro settings side and what harm they can do to devices. We don't want our Tier 1's to be able to wipe a device for instance.
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-06-2023 05:38 AM
JAMF's Access Control more or less sucks, which is probably why they were not helpful.
- Best option: Use AD Groups. Provision each AD group with the access you want it to have, and put the users in the correct AD Group. For this you will need LDAP setup in JAMF Pro to the AD Tennant with the AD Group(s) you are wanting to use.
- Not the worst option: Create JAMF local groups, and add JAMF local accounts to the groups. This is not synced with AD and does not require LDAP to be configured.
- Worst option: Grant access to users directly.
- Note: If a user is in multiple groups, or has access provisioned directly they will receive the most privileged access among all access they have.
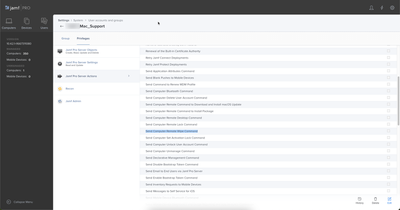
What you are specifically looking for is in System > User Accounts and Groups > {select the account or group you want to mess with} > JAMF Pro Server Actions > Send Computer Wipe Command. Uncheck the box to remove the option to wipe the device from the computers inventory record.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-06-2023 05:38 AM
JAMF's Access Control more or less sucks, which is probably why they were not helpful.
- Best option: Use AD Groups. Provision each AD group with the access you want it to have, and put the users in the correct AD Group. For this you will need LDAP setup in JAMF Pro to the AD Tennant with the AD Group(s) you are wanting to use.
- Not the worst option: Create JAMF local groups, and add JAMF local accounts to the groups. This is not synced with AD and does not require LDAP to be configured.
- Worst option: Grant access to users directly.
- Note: If a user is in multiple groups, or has access provisioned directly they will receive the most privileged access among all access they have.
What you are specifically looking for is in System > User Accounts and Groups > {select the account or group you want to mess with} > JAMF Pro Server Actions > Send Computer Wipe Command. Uncheck the box to remove the option to wipe the device from the computers inventory record.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-06-2023 01:27 PM
We do not plan on using LDAP or vLDAP at this time, so AD groups is a no go. I was specifically looking for some sort of local group least privilege documentation, to setup our Tier 1-3 users with the proper privileges.
Seeing as there really isn't any that I can find at this time, we may just give most of our IT staff admin privileges, as we don't have the time nor resources to dig into the Jamf Pro privilege systems at great length.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-06-2023 01:41 PM
You can make JAMF Groups, and assign whatever access you want to them. Then Assign JAMF user accounts to those groups. As for what Access falls in to what Tier, that is on you guys to determine, no one can do that for you.
Honestly, figuring out and setting up permissions will take you all of 10 minutes. If you are not going to invest the time in figuring out how to Manage a MDM Environment, you may want to consider managing devices at all. JAMF not any other MDM platform is set it and forget it, it requires configuration and maintenance which will require research and time. You can contract this out if you are that set in not figuring this out but need to manage devices, though keep in mind you would be handing the keys to your castle to a contractor.