- Jamf Nation Community
- Products
- Jamf Pro
- Re: Silent install issue with Fireeye HX agent v33...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Silent install issue with Fireeye HX agent v33.51.0
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-28-2021 06:40 AM
Last week our cyber security team provided us the newest Fireeye client for Mac OS 11.
Installing via Jamf Pro Cloud pkg is causing a dialog for the user to consent to the P2BNL68L2C.com.fireeye.helper system extension. It's the same dialog on a standard install.
We've testing out the initial app install and get an install prompt that requires manual intervention. Even added P2BNL68L2C.com.fireeye.helper to system extensions, approved kernel extensions to see what would happen: Intervention was still required. We’ve been pretty liberal with the PPPCs and have had the prior kext which doesn’t appear to be used in Big Sur both included and not.
When reaching out to Fireeye support they initially offered assistance after a few emails gave a blanket "Silent uninstallation with MDM solutions is not currently supported on macOS 11.". They plan on adding support in future releases.
Prior versions of the Fireeye Client for Mac OS packaged and performed silent installs without issue and we're hoping someone here has seen and figured a work around.
thanks in advance.
Bill
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-28-2021 03:05 PM
So far we are deploying FireEye HX agent 33.46 on 1600 Macs in Big Sur with no problems. We make sure any PPPC or Extension approval profiles are deployed before the agent is installed.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-05-2021 10:08 AM
Hello
@Phantom5 Are you able to provide what you profile looks like for PPPC and Extension Approval? We just received the 33.51.0 installer. We pushed out to my Mac and I received the pop up. The System extension we used for v32 does not appear to work (the profile was already in my device). Many thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-06-2021 09:47 AM
Did you ever get this resolved? I am having the same issue while upgrading from 32 to 33.51.0. The new FireEye Helper is causing a System Extension pop up.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-10-2021 02:26 PM - edited 09-02-2021 04:00 PM
Hey Folks,
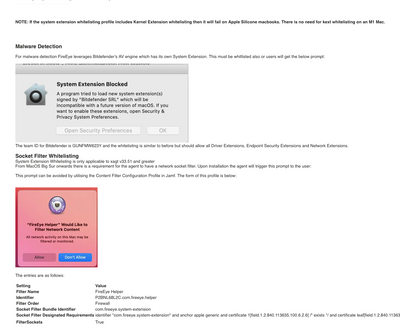
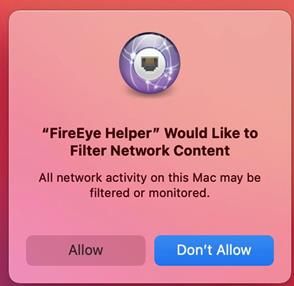
I have resolved our issue of receiving the System Extension "content" block and also the FireEye Network Filter pop up. After many hours of research, testing and a phone call to FireEye I finally have the ingredients to silently upgrade/install version 33.51.10 to Big Sur.
**Note - we do not use BitDefender
** These are not all of my notes**.
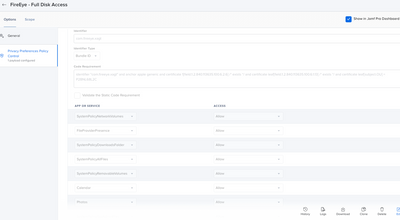
I also left my previous PPPC profile on which allowed Full Disk Access to xagt. Which basically included every service. It does not hurt to have more than you needed. You can also check with your CSIRT team to see what they needed scanned.
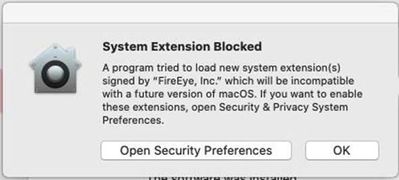
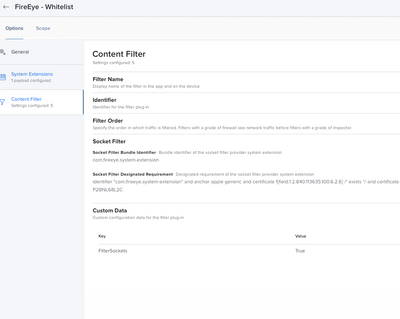
| Setting | Value |
| Filter Name | FireEye Helper |
| Identifier | P2BNL68L2C.com.fireeye.helper |
| Filter Order | Firewall |
| Socket Filter Bundle Identifier | com.fireeye.system-extension |
| Socket Filter Designated Requirements | identifier "com.fireeye.system-extension" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = P2BNL68L2C |
| FilterSockets | True |
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-02-2021 10:21 AM
Great write-up... Thank you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-15-2021 06:10 PM
This is a really useful write up and thank you for that. I do have one question. I go to add the Socket Filter Whitelisting and all the fields you identified are there, with the exception of FilterSockets. I'm entering it in the payload for Content Filtering in the configuration profile, but perhaps I'm supposed to be entering it elsewhere.
Again, thanks so much.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-16-2021 08:02 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-16-2021 10:05 AM
Hi Pueo,
Got it, and thanks so much again.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-31-2021 11:39 AM
@pueo - Many thanks. I can't imagine how many hours this saved me nor do I want to think about how long you had to work to get this all working correctly.
This is the first time I have had to specifically call out a system extension by name in order for it to be approved. Typically approving by team identifier has been enough for me.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-31-2021 05:04 PM
No problem. There is more. After more than a few emails to FE they eventually gave me updated documentation with the exact procedure a MDM Admin needs to follow in order to successfully deploy FireEye v33.51.0.
One of the bigger changes was adding more settings to the PPPC (whitelist) setting. The previous documentation only had ALLsystemfiles but they now suggest to have quite a few more. They also provide screen shots for Whitelisting and setting up Malware detection.
Upgrading FE is easy. Push out profiles, push out HX client (we are using HX Console for agent. Anyways if you need the pdf there must be away I can send it to you.
p.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-16-2021 10:56 AM
Hi @pueo
Can you tell me the name of the PDF you got from FireEye/Mandiant so I can try to get it from support, or put it up in a place I can grab it? Unfortunately, when I try to distribute the config profile, I get the error "The ‘VPN Service’ payload could not be installed. The VPN service could not be created." so I want to verify that I'm setting it up correctly.
Thanks,
Michael
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-17-2021 08:08 AM
Sorry for the delay Michael. Sent to you private messages.
ash
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-17-2021 01:45 PM
Got it going! Thanks for all your help!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-18-2021 06:45 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-25-2021 01:07 AM
I'm struggling with the System Extension approval popup and PPPC Payload but FireEye support claim they have no resources on this to help and that it's up to me to figure out...
If someone could post their PPPC payload for xagt that would help greatly or If anyone happens to have a copy of the MDM deployment PDF that @pueo was sent from FireEye i would be forever in your debt if you could send it to me as well.
The FireEye docs talk about packaging and installing it, but nothing about getting it to silently install/upgrade.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-27-2021 11:38 AM
Hi @johnsz_tu - I apologize for not responding sooner. I never did get the PDF. I did find a a page on the FireEye community which gave me the details I needed though. The page is here - https://community.fireeye.com/CustomerCommunity/s/article/000003689
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-27-2021 01:14 PM
@mlarson Sorry I didn't follow up with documentation.
Do the attachments I just added to the post resolve your issue?
Cheers,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-27-2021 02:33 PM
Hi @pueo, The screenshots look good and I was able to get it resolved from the FireEye community page I linked to earlier. Thanks again for all the help you've provided.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-27-2021 01:11 PM
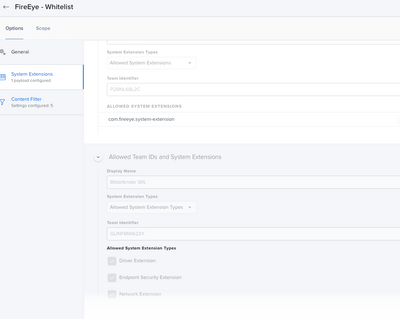
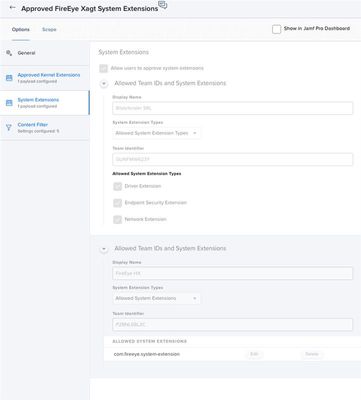
Hello. Sorry for the delay in replying. I am happy to help with screen shots to get you moving along with your FE deployment. The first two screen shots are taken from the Documentation. The differences between the previous FE installer and the current one (33.51) is you now need a Content Filter.
Again, apologies for the tardiness.
Cheers.
Our Profiles.
System Extension
Content Filter.
FE Documentation
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-27-2021 02:39 PM
@pueo Thank you so much!!
That will help so much.
I managed to get through the System Extension dialog yesterday, and have started battling with the Popup for the Network Filter
Going to try to build based on the screenshots above today
Really appreciate it 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-22-2021 11:58 AM
Hi @pueo ,
We've been trying to get this upgrade to v.33.51.1 for more than a month and it's still failing for us...Engaged some FireEye tech for this issue and he sent the same guide that you provided the screenshots from, but it doesn't seem to go through the installation, failing somewhere while running the xagtSetup (see below):
"Installing FireEyewPostinstall v.33.51.1 PROD.pkg...
Successfully installed FireEyewPostinstall v.33.51.1 PROD.pkg.
Running script FireeyePostinstall v.33.51.1...
Script exit code: 1
Script result: installer: Package name is FireEye Agent
installer: Installing at base path /
installer: The install failed. (The Installer encountered an error that caused the installation to fail. Contact the software manufacturer for assistance. An error occurred while running scripts from the package “xagtSetup_33.51.1.pkg”.)
Error running script: return code was 1."
Again, I've already created the required Config Profiles as per the FireEye guide, still No Bueno! 😞
Any ideas?
Thanks,
CC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-23-2021 05:21 PM
Hello
**Sorry for the double reply. A few lost screens a re write and I can't figure out how to remove a old post**
-
We keep our FE Agent very basic when it comes to deployment.
For new machines Jamf will install the repackaged client using the following post install script (we use DEPNotify for deployments):
#!/bin/sh
## postinstall
sudo installer -pkg /private/tmp/FireEyeAgent/xagtSetup_33.51.0.pkg -target /
sudo rm -r /private/tmp/FireEyeAgent
--
After this, once the agent checks in with HX the agent will receive any other configurations it needs. Keep it simple
I packaged this small script using Composer. It took many attempts to get it working.
Things to try
- Test script locally
- Remove spaces from pkg name
- check jamf and install.log files.
As a reminder: Think locally first..:-)
a.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-25-2021 05:40 AM
Hi @pueo,
Thanks for the suggestions. And, you are right, the best test is to try it locally, which I've already done that...I've got the .dmg copied locally and tried to go through the normal installation, but it failed at the end. So, I'm not sure if I'm doing something wrong or if this package received from FireEye has some problems with it.
Thanks,
CC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-25-2021 07:33 AM
Try using a pkg instead. I rarely if ever use a DMG.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-25-2021 07:34 AM
If the agent does not install just from double clicking the package on a local Mac, then you may have a damaged agent.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-25-2021 07:36 AM
Actually, the .dmg has the package and JSON files, when I double-clicked it. I ran the pkg and got the Failed message right at the end.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-25-2021 07:48 AM
Sounds like a damaged pkg file. Maybe try on one more machine. I drag both the json and the pkg file to the /private/tmp/FireEyeAgent folder (I created the FireEyeAgent folder). Then package it up with the post install script.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-25-2021 08:02 AM
Yeah, I've tried that too initially...directly from the /private/tmp/FireEyeAgent folder...No dice either! 😞
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-23-2021 05:05 PM
Hello @cc_rider
I can't see the contents of your package or any scripts. So I have posted what I did and I works for us.
For new/reimaged Macs we deploy the FE Agent as part of our DEP Notify script. This is not important.
My post install script for FE is posted below:
--
#!/bin/sh
## postinstall
sudo installer -pkg /private/tmp/FireEyeAgent/xagtSetup_33.51.0.pkg -target /
sudo rm -r /private/tmp/FireEyeAgent
--
I packaged this small script using Composer. It took many attempts to get it working.
Does you script work locally? You should be able to run it locally after moving the pkg into whatever directory it loads from.
Remove spaces from you pkg file or use _ or - to join words. This will help simplify things and help trouble shooting. maybe use one name like FEAgent.pkg, test then build up from there.
check jamf.log and install.log.
Test locally..then jamf..
Good luck!
Cheers,
a.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-19-2022 09:24 AM
Hi @pueo ,
Sorry for the long wait before my reply, but our peeps in charged to manage the FireEye appliance had to upgrade it to a newer version, therefore that's why I had to put on hold the testing...Anyways, I just received the v.34.28.1 to test with, but I need to make sure now that I'm following the correct path. 🙂
Could you please tell me how are you doing with upgrading from a lower version to v.34.28.1? Previously, we have been using a script to remove ALL the necessary files/folders/entries before you install the new version...From FireEye tech, I've got this instruction:
"please make sure that the customer correctly removed the system extension and rebooted the mac. The correct command to remove everything is to add the remove helper switch: sudo /Library/FireEye/xagt/uninstall.tool --remove-helper
After running this command and rebooting, the customer should install version 34.28.1 and allow the FireEye and Bitdefender kernel extensions."
Is it going to be enough that "uninstall.tool" with the switch like that?
Thanks,
CC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-04-2022 06:34 AM
Questions about the configuration profile. Kext whitelisting will fail on Apple Silicon. Should I have two configurations profiles one with Kext for Intel and another without Kext for AS? Or just the one and just let the Kext fail?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-04-2022 09:46 AM
@mlitton Kernel Extensions are a thing of the past now, so I guess you are running a macOS less than Catalina? Create two Profiles, one for System Extension and one for Kernel Extension and scope to the appropriate macOS. It does not hurt having both profiles on each machine but can add confusion.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-18-2022 11:16 AM
Thanks @pueo for sharing your findings on this FireEye HX/xagt release and config screens (just love those vendors hiding important info behind their support portals).
Adding to your reply to @mlitton question... agree w/ creating two profiles for Kext (Intel) and SysExt (ARM), but probably best to exclude each config profile scopes via smart groups for "Architecture type" is/not "arm" or is/not "x86_64"? Otherwise, you're potentially generating extra log chatter and performance overhead for failed installs.