- Jamf Nation Community
- Products
- Jamf Pro
- Re: System Preferences for Standard Users
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
System Preferences for Standard Users
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-21-2015 07:46 PM
I've been testing the enrolment of standard users within local groups to manage system settings such as printing and networking, normally reserved for Admins. Does anyone have a list or a resource that easily allows me to see what groups allow what functionality? Trail and error is taking it's toll on me...
Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-21-2015 08:27 PM
in general, anything that effects the system is admin only ie. network, printing, security settings
Printing is a bit of irregular one, as the preference pane is locked, but if the standard user is a member of lpadmin group then they are able to add and remove printers.
If you want to get right into it i recommending reading through this post by the one and only Rich Trouton
https://derflounder.wordpress.com/2014/02/16/managing-the-authorization-database-in-os-x-mavericks/
There is a couple links at the bottom of the post that give you an idea of how the authorisation database works and what you can do with it
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-21-2015 08:45 PM
Really good resource here that I believe is also referenced in @rtrouton 's blog:
http://www.dssw.co.uk/reference/authorization-rights/index.html
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-21-2015 08:56 PM
@calumhunter Thanks for the quick response.
I was running through the guide, but running under a local administrative user on Yosemite, I get the following result:
james-test-mbp:~ local-admin-user$ security authorizationdb read referenced.rights
NO (-60005)Still feeling adventurous I continued with the following:
james-test-mbp:~ local-admin-user$ sudo security authorizationdb write system.preferences allow
Password:
YES (0)
james-test-mbp:~ local-admin-user$ sudo security authorizationdb write system.preferences.network allow
YES (0)Feeling lucky, I ventured to my trusty control panel and ... nought.
Let's reboot...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-21-2015 09:37 PM
What exactly are you trying to achieve™?
Allow non-admins access to the network sys prefpane? For what purpose exactly?
Perhaps there are better ways to achieve the end goal
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-21-2015 09:50 PM
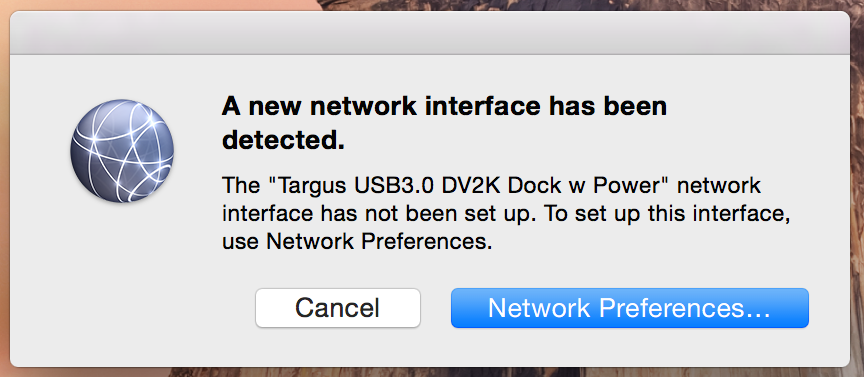
I need to allow a standard user to allow the use of and configure a new interface when plugged into the machine. These interfaces are typically created through the use of USB based docking stations. I've added an example of what a standard user is prompted with when connecting to an unfamiliar dock.
I also need to allow a standard user to create, edit and remove printers.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-21-2015 10:39 PM
Edit to add:
a good guide on what system rights are available is here:
http://www.dssw.co.uk/reference/authorization-rights/index.html
Ah right ok, you could perhaps create a script to run from self service that detects new hardware. But configuration of that might get a bit more complicated if they want to do any more than DHCP
in which case your pretty much on the money with those two security commands but there is one more you need for 10.9 and 10.10 from what I can tell
so try this
sudo security authorizationdb write system.preferences allow
sudo security authorizationdb write system.preferences.network allow
sudo security authorizationdb write system.services.systemconfiguration.network allowYou'll need a reboot for that to take effect.
Allowing standard users to add/remove printers is as easy as adding them to the lpadmin group
ie.
dseditgroup -o edit -a $username -t user lpadminyou could run that as a login script. Its idempotent, but you could run some checks first.
Here is a login script that I run. For Casper, you will need to fix up the logged_in_username variables. Casper provides the username as $3 so just set logged_in_username to $3 and you should be right
#!/bin/bash
##############################################################
# #
# Author: Calum Hunter #
# Date: 15-05-2015 #
# Version: 0.1 #
# Purpose: Login script to ensure the user is a member of #
# the lpadmin group in order to add/remove #
# printers. #
# #
##############################################################
# Script Configuration
logger_tag="LoginScript_lpadmin_group_check"
logged_in_user_id="$1"
logged_in_user_name=`id -un $1`
printer_group="lpadmin"
# Script Functions
check_group_membership(){ # Function to test if a user is a member of the $printer_group
member_check=`dsmemberutil checkmembership -U $logged_in_user_name -G $printer_group`
if [ $? != "0" ]; then
logger -p 2 -s -t $logger_tag "Error! Got error from dsmemberutil while trying to checkmembership of user $logged_in_user_name for presence in group $printer_group"
exit 1
fi
if [ "$member_check" = "user is not a member of the group" ];
then
logger -p 5 -s -t $logger_tag "User: $logged_in_user_name is NOT a member of: $printer_group"
add_user_to_lpadmin $logged_in_user_name
elif [ "$member_check" = "user is a member of the group" ];
then
logger -p 5 -s -t $logger_tag "User: $logged_in_user_name IS a member of group: ${printer_group}, nothing to do here."
exit 0
fi
}
add_user_to_lpadmin(){ # Function to add a user to the lpadmin group
logger -p 5 -s -t $logger_tag "Adding $logged_in_user_name to $printer_group ...."
dseditgroup -o edit -a $1 -t user $printer_group
if [ $? != "0" ]; then
logger -p 2 -s -t $logger_tag "Error! Got error from dseditgroup trying to add $1 to $printer_group "
exit 1
fi
logger -p 5 -s -t $logger_tag "User: $logged_in_user_name added to: $printer_group successfully."
}
#--- Run Script Functions ---#
check_group_membership
exit 0- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-18-2015 05:46 AM
@calumhunter The three lines to grant standard user access to the network preferences, I am guessing that that is all of the data that the script needs to contain to grant this. Is that correct?
Also, when should that run? Just once per machine at build time? Continuously at machine startup/login?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-18-2015 05:50 AM
yeah for a first boot script it would be
#!/bin/sh
security authorizationdb write system.preferences allow
security authorizationdb write system.preferences.network allow
security authorizationdb write system.services.systemconfiguration.network allow
exit 0that will modify the authorization database. it should survive reboots and os updates (maybe?)
you could make your script check the status of those keys and if its not allow set it to allow if you wanted to go that way
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-19-2015 05:12 AM
Easiest way to handle printing if you're going to enable everyone to add/remove printers anyhow:
/usr/sbin/dseditgroup -o edit -n /Local/Default -a everyone -t group lpadminAll users will then be able to add printers as necessary. The only thing that can be tricky is the printer drivers themselves, which can require admin rights to install (or Self Service).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-14-2016 11:00 AM
@ jazzyj Did you ever get this working?
I'm Trying to follow along here to give users access to network system preferences on OS X 10.11.4
Have tried
security authorizationdb write system.preferences allow
security authorizationdb write system.preferences.network allow
security authorizationdb write system.services.systemconfiguration.network allow
but still after a reboot standard users have no access
Have also read through RTroutons blog on how this works with OS X 10.10, but still no success
https://derflounder.wordpress.com/2014/02/16/managing-the-authorization-database-in-os-x-mavericks/
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-19-2016 08:08 AM
Hi all,
I have a followup on this matter.
As the commands work fine I now want to be able to revert the setting as I only want someone to have this access temporarily.
I am able to lock the pref again but clicking the lock now results in nothing. I mean that I cannot unlock the pref, no user/pass is asked. In other words .. it is broken....
Any ideas?
What I have done to lock the pref again is remove the lines <key>rule</key> and the containing string allow.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-19-2016 08:20 AM
@rblaas I have tested and verified that is these commands unlock the preference
security authorizationdb write system.preferences allow
security authorizationdb write system.preferences.datetime allow
These commands will lock the preference
security authorizationdb write system.preferences authenticate-admin
security authorizationdb write system.preferences.datetime authenticate-admin
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-19-2016 08:41 AM
@donparfet Thanks for your quick reply.
I have tried your solution but no luck..
This is what I have done
To unlock:
security authorizationdb write system.preferences.network allow
security authorizationdb write system.services.systemconfiguration.network allow
To Lock
security authorizationdb write system.preferences.network authenticate-admin
security authorizationdb write system.services.systemconfiguration.network authenticate-admin
(after running the lock commands the pref is still unlocked. I can not lock it manually. Also after reboot the pref is still unlocked)
I am not running the system.preferences authenticate-admin because I have another pref which I do want to stay open. (printers)
To clarify: I want a normal user to be able to change the network settings. Maybe I am just doing it wrong aka wrong settings.
EDIT: I have tried using default and that seems to work.. Will do some more testing but for now it does the trick..
(security authorizationdb write system.services.systemconfiguration.network default)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-19-2016 10:19 AM
Could this be handled in a different automated way without having to elevate permissions?
When you connect the device, does it update a file? Maybe a LaunchDaemon with a WatchPath, e.g.:
WatchPaths = (
"/Library/Preferences/SystemConfiguration"
);This could trigger a script. Do you feel you could script the addition of a new dock?
networksetup may help you here, e.g. to start with:
networksetup -listallhardwareports