- Jamf Nation Community
- Products
- Jamf Pro
- Re: Trying to find out what specific "changes to t...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-01-2022 06:54 AM
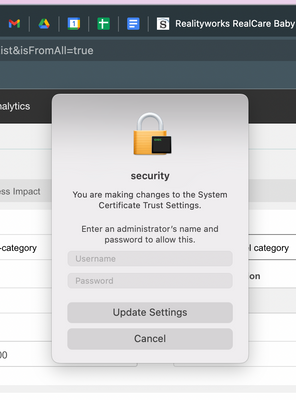
I'm seeing this popup on some of our users devices since the upgrade to Monterey, but I'm not entirely sure what it's trying to do, and it seems like I need to know in order to prevent it from popping up by automating what it's trying to do. I think this is from trying to install FortiClient, but I'm not positive.
How can I tell what it's doing so I can make this easier on our users?
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-01-2022 09:11 PM
Most of the answer is already in the question.
Go to Keychain
System > Certificates
There is one cert it is trying to edit.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-01-2022 06:57 AM
You will need to find the cert password t is trying to install in the keychain and export it. Then upload and deploy via Jamf and click the check box allow access to all apps.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-01-2022 07:00 AM
Is there an easy way to check what cert password it's trying to install in the keychain? That is primarily what I'm having trouble with. I'm not sure if there are any specific logs I should be looking at, as I've done very little with certs on Mac.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-01-2022 08:40 AM
I would setup a fresh virtual machine and check the keychains before and after install of this app.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-01-2022 09:11 PM
Most of the answer is already in the question.
Go to Keychain
System > Certificates
There is one cert it is trying to edit.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-17-2022 02:55 PM
Don't know if you're still trying to figure this out, but here's what I found out:
FortiClient installs two ZTNA certs to the Keychain > login
One of the certs matches the serial number of the FortiClient EMS, and should be the same for every user. The other cert is specific to each endpoint, and the name of that cert matches the UID2 serial that you see if you open FortiClient > About.
I figured that the first cert could be exported and pushed through a configuration profile, but it doesn't install to the keychain, and when I install the client I still get the prompt to approve changes. Maybe I'm missing a piece here, I've never pushed a cert via config profile.
I'm still working on this, but wanted to post this info in case it serves you. Perhaps we can figure it out together.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-10-2023 09:21 AM
Hi,
Were you able to find a solution for this issue?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-10-2023 09:34 AM
Following the instructions from the other users, I was able to get rid of this message by adding the certificate I found to my pre-forticlient-install config profile. Of note, I did notice that a lot of the issues/popups I see on installing forticlient are different between MacOS versions - my prep config profile doesn't work properly on Big Sur vs Monterey, as an example.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-10-2023 09:39 AM
Hi dungeonadept,
Where I am all devices are Monterey and Ventura. If there is no Forti Client installed on the device before, I do not encounter pop-up windows. However, if the Forti Client is already installed on the device, I encounter the pop-up problem and it asks the user to enter a password.
How can I find the certificate you are talking about? Can you describe it to me? Or if you can share your profile file, I can better understand what I'm doing wrong.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-10-2023 11:08 AM
Hi Everyone,
I solved the problem. Thanks everyone. If anyone needs help, they can reach me here.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-03-2023 05:38 AM
Hi @ulascelik - I'm interested in the solution you found
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-01-2023 07:15 AM
How did you get this resolved? I thought I had this fixed, but it turns out that even though I'm including our EMS cert, it's still giving me the Certificate Trust Settings popup, assuming it's for the second cert.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-06-2024 12:07 PM
looking for this solution as well as I continue to get this prompt on new deployments
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-06-2024 12:08 PM
Hello,
looking for this solution as I continue to get this prompt on new deployments
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-27-2023 01:45 PM
Hi there @hdagidir - I'm interested in the solution you found. I'm using the mobileconfig from Fortinet support, which seems to work best from other put-together profiles I attempted. I am attempting to deploy update of 707 from existing installs of 648. I'm down to two prompts:
Forticlientagent wants to change the system cert (requires admin pass, our staff are standard)
VPN service asking for login password, which I think is FCT asking permission to access the cached cred in keychain for the existing VPN credential so it can autofill in the app?
I gather from the original threads and great info from @JDaher @dungeonadept and others that I need to locate and include a cert from an existing install (or elsewhere), likely the one designating my EMS serial. I do see one in the system root CA keychain. I do not see a unique one for the individual client/endpoint. Are we saying this needs to be deployed prior to install? I have a bunch of bits and pieces of the resolution here, and am just trying to unify it all for my case. We use Jamf School, so there are often differences in the solutions found by Pro users and the steps to reproduce success are different. Hoping that's not the case here! : )
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-06-2024 04:43 PM
Hello @MasterNovice
I posted the link below in another discussion on this. It is a guide for deploying v7.2 but it's likely that the instructions are the same for 7.0.7. Specifically, the instructions regarding downloading the config profile from FortiClient and editing it to add your certificate information:
The profile does need to be deployed prior to the installation, although I think that you can deploy it post-installation and just restart the machine.
I just went through this process and have tested it on a couple machines. The installation went smooth, with no user prompts at all. Good luck.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-08-2024 07:40 PM
I want to make an edit to my post on 6/17/22 about the certs that FC installs. On the latest versions we have installed (7.0.7 & 7.2.2) this is what I've noticed:
- FortiClient DNS Root
- ZTNA Root CA certificate - This cert number matches the serial number of the FortiClient EMS, and its number is the same for every user.
- The third certificate is specific to each endpoint, and its name matches the UID2 number that you see when you open FortiClient > About.