Hi
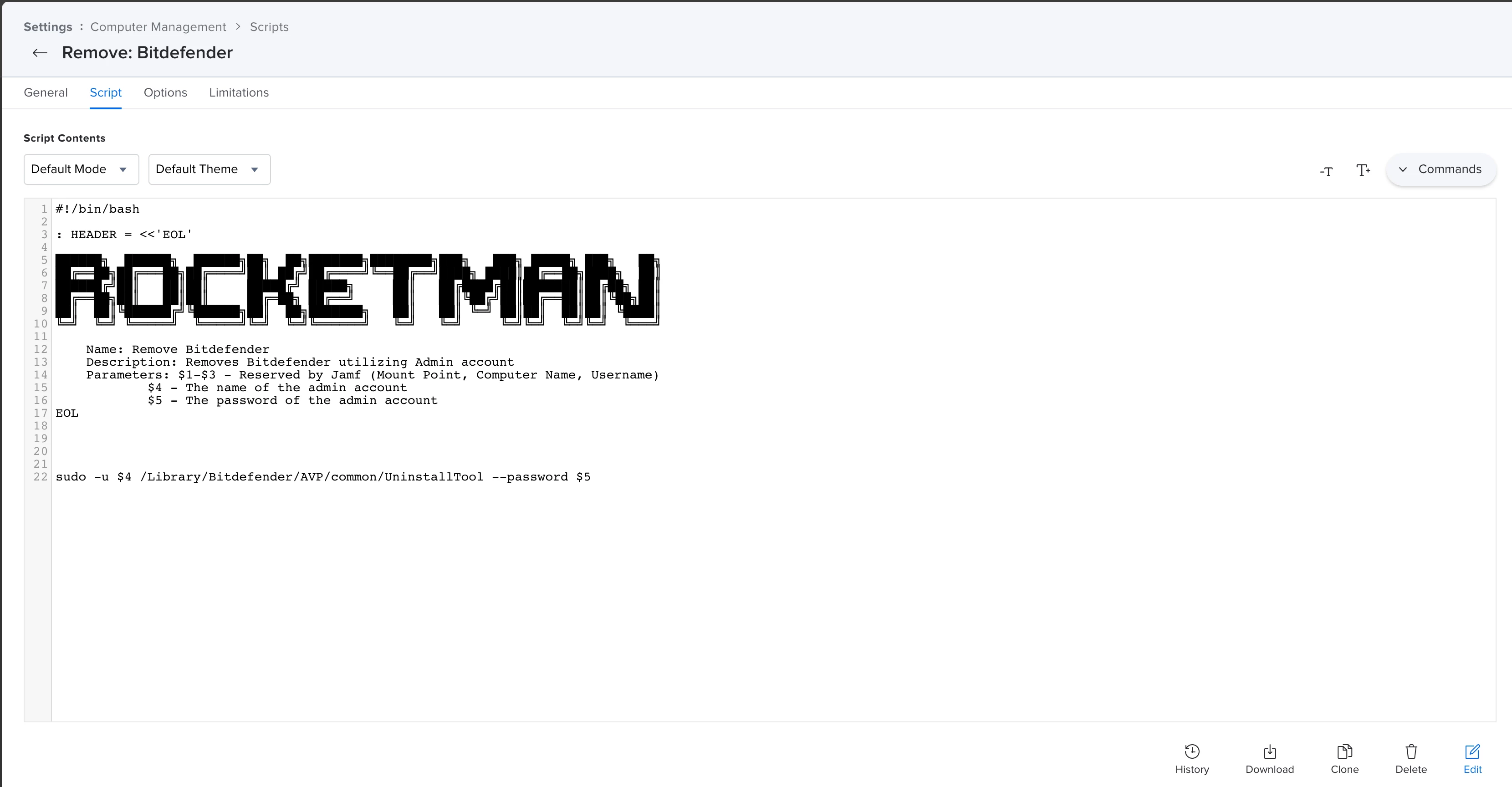
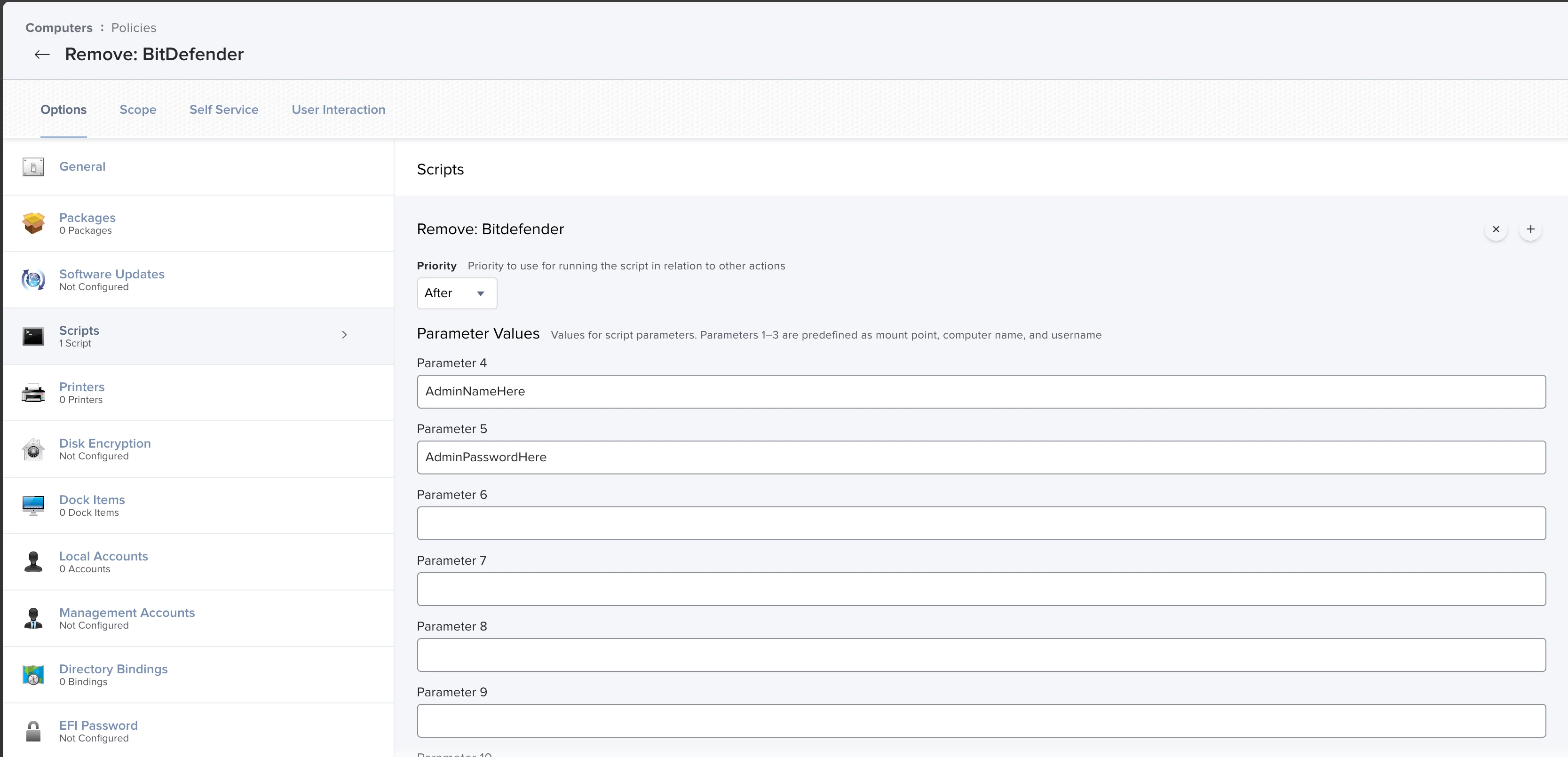
We are trying to put together a silent uninstaller for out BItDefender endpoints. The command requires a --password flag which we don't want to be pushing our Jamf management account password over plaintext in this command. I am trying to put together a script that creates a new admin user, runs the uninstaller, and then deletes the admin user. I am running into issues switching to the created admin account to authenticate. Is there a certain way you can sudo su in a script? Below are the two variations we have tried and tested unsuccessfully:
jamf createAccount -username bdremover -realname "BitDefender Remover" -password <random password> -home /Users/bdremover -hiddenUser -admin -secureSSH
sudo /Library/Bitdefender/AVP/common/UninstallTool --password=<random password>
jamf deleteAccount -username bdremoverjamf createAccount -username bdremover -realname "BitDefender Remover" -password <random password> -home /Users/bdremover -hiddenUser -admin -secureSSH
sudo -U bdremover /Library/Bitdefender/AVP/common/UninstallTool --password=<random password>
jamf deleteAccount -username bdremover