- Jamf Nation Community
- Products
- Jamf Pro
- Re: WPA2 Enterprise TTLS/PAP RADIUS
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
WPA2 Enterprise TTLS/PAP RADIUS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on
06-29-2018
10:49 AM
- last edited
2 weeks ago
by
![]() kh-richa_mig
kh-richa_mig
I am trying to set up a network profile to use RADIUS with TTLS/PAP. The profile works if I include a username/password in the profile but it won't prompt the user for them if I don't include them.
I have tried enabling/disabling the "use a login windows configuration" and "use directory authentication" options. Anything I am missing to prompt the user to enter it?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-01-2018 08:53 PM
F.Y.I: Debug for RADIUS and macOS WPA2 issues
https://documentation.meraki.com/MR/Encryption_and_Authentication/Advanced_RADIUS_and_WPA2_Debugging_using_macOS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-06-2019 12:17 PM
@esam Were you able to find a solution for this? I am running into the exact issue deploying Onelogin Radius authentication.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-13-2019 12:39 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-06-2019 06:44 AM
same issue and not fixed in Jamf Pro 10.16.1 (maybe it's radius issue). the workaround is create a package with 802.1x wifi profile and a postinstall script. then use policy to deploy the 802.1x profile package.
#!/bin/bash
/usr/bin/profiles -I -F /path/to/802.1x.mobileconfig- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-15-2020 02:22 PM
Bumping this if only for that Meraki link. That got me exactly what I needed today! Thanks @takayuki
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-27-2020 09:37 AM
@shan3 @esam @smansoor @grahamfw - I got this working in our environment: OneLogin for RADIUS auth, JAMF for Profile/Cert Deployment, Meraki Network.
Check this out: https://onelogin.service-now.com/kb_view_customer.do?sysparm_article=KB0010466
If you have more specific questions for me, fire away! Also I am way more likely to respond on the Mac Admins Slack if you wanna find me there: Breck
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-29-2020 03:46 PM
@Br3ck Do your users have to change their OneLogin passwords regularly? If so, how does this affect the WiFi config on their machines? I ended up locking myself out of OL in my testing because I changed my password, but my Mac didn't know about it and kept trying to authenticate to OL RADIUS with my old pw. Any help on this would be much appreciated - its the only thing stopping me from deploying OL RADIUS here.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-30-2020 09:44 AM
@typeraj - Hey Raj! So yeah we totally run into this and its clunky as hell... I've found the sure fire way to fix this is to delete the old keychain entry associated with your previous password. I have a little script that can do this I threw in Self Service for users. Sometimes it just works as you would expect though, MacOS prompts for the new password after it's been changed in OneLogin, the user puts it in and they are on their way. Do you have the ability to do cert based auth instead of username/pass? This is eventually where we want to get but we don't have a CA yet unfortunately.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-30-2020 05:06 PM
@Br3ck I'd love to do cert based auth but its not an option for us at the moment. I do like the idea of a little SS script, its an extra step but I don't think our users will mind too much. Any chance you can share what you have? Happy to Slack you if you'd prefer.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-31-2020 10:57 AM
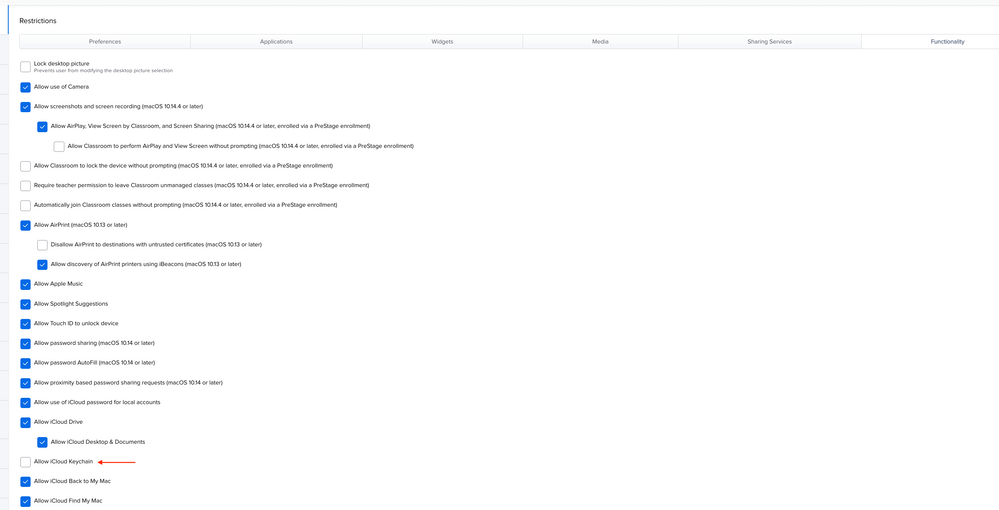
@typeraj - for sure, see below. Keep in mind that if you have users using iCloud keychain that that is a whole other can of worms. I would honestly stop iCloud keychain on your fleet if you can. I haven't gotten around to it but there are some jamf nation threads with some hacky ways to prevent icloud keychain from working without fully blocking iCloud entirely. Also note that your user would need to be on ethernet for this SS mechanism to work... its all very ugly but hey very secure! ;)
#!/bin/sh
#Determine the currently logged in user and save their account name as the loggedInUser
loggedInUser=$( ls -l /dev/console | awk '{print $3}' )
su "$loggedInUser" -c '/usr/bin/security delete-generic-password -s com.apple.network.eap.user.item.wlan.ssid.<INSERT SSID HERE>'
security delete-generic-password -l "<INSERT SSID HERE>" "/Library/Keychains/System.keychain"
exit 0- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-04-2020 04:30 PM
@Br3ck Thanks for sharing mate :-) For iCloud Keychain, I tested a config profile with the restrictions payload and it seems to work well. If it was enabled on the Mac prior to receiving the profile, it just disables it silently and converts the keychain back to Local Items.