- Jamf Nation Community
- Products
- Jamf Pro
- WPA2 Enterprise WiFi Broken on 10.12.6 & 2017 MacB...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
WPA2 Enterprise WiFi Broken on 10.12.6 & 2017 MacBook Pro
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-11-2017 03:11 AM
Hi guys,
So this may be related to the issue at this post:
[https://www.jamf.com/jamf-nation/discussions/24129/sierra-10-12-5-upgrade-breaking-corp-wifi](link URL)
We just took delivery of 5 shiny new MacBook Pro 2017 models with two thunderbolt ports but no touchbar.
We currently have 35 older MacBooks running El Cap 10.11.6 that have config profiles deployed on them with a Network payload and a Certificate payload. These are bound to our Active Directory.
The setup we have working with these is a machine based authentication to the WiFi at the login window, and then the user logs in to authenticate both to the network and then to their AD account.
This has worked fine, but deploying this same config profile to these new MacBooks doesn't work.
The WiFi icon seems to flash solid briefly several times at the login window, but it isn't successfully authenticating to the network.
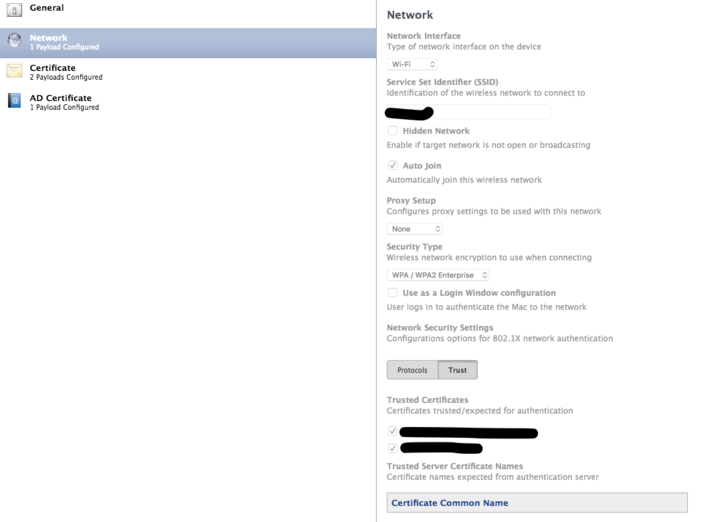
The network settings we have set are:
**Auto-Join (checked)
Security Type: WPA/WPA2 Enterprise
Use as login window configuration (checked)
Protocols:
PEAP
Use Directory authentication (checked)**
And in the trust tab, I have checked a series of certs that are the root and intermediate certs for our AD as well as the CA for our AD. I added these to the 'Certificate' payload.
I don't necessarily think the settings in my profile are incorrect, since it works on the older MacBooks running El Cap, but clearly something has changed in Sierra that has thrown everything out of whack.
One error I do see in the WiFi logs on the new MacBooks is something about an EAPOL frame being dropped and it not being a key frame.
Anyone see anything I'm missing?
Thanks for your help,
Rory.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-11-2017 06:25 AM
This may be a dumb question, but have you checked the AD binding? Maybe unbinding them and manually rebinding the machines to AD may solve your issue.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-11-2017 06:35 AM
Somethings did change between 10.11.6 and 10.12 - the machine doesn't trust the radius cert. You could test this by logging in to the machine with an admin account - going to Keychain and finding the radius cert and see if its trusted - then trust all - reboot and see if you can login.
If it does work then your configuration profile needs some tweaking with the certs.
related article - [https://www.jamf.com/jamf-nation/discussions/24129/sierra-10-12-5-upgrade-breaking-corp-wifi](link URL)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-11-2017 07:16 AM
@duffcalifornia Thanks, yeah I've tried that and it doesn't seem to make a difference
@bwiessner I'll double check those trust settings...I'm pretty sure all the relevant certs are trusted but I'll double check the RADIUS one as well and report back.
Cheers
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-18-2017 07:31 AM
Just got this working...turns out we didn't quite have the full set of certs from root upwards. Obviously this meant it wouldn't authenticate as there was an element of the connection it wasn't trusting.
Thanks guys.