- Jamf Nation Community
- Products
- Jamf Pro
- Zscaler, the nonsensical adventure of configuratio...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-07-2023 06:33 AM - edited 04-07-2023 06:35 AM
I recently had to configure Zscaler for my environment and I figured I would share incase it helps anyone.
- Prior to 3.9 Zscaler was configured with a script, the JAMF documentation is eh and the got the script they provide from someones GitHub repo.
- With 3.9 Zscaler is now configured with a configuration profile, which at the time of writing is documented for intune and not JAMF. Zscaler has advised they will update their JAMF Documentation, but as of 6 weeks and they still have not updated their documentation.
- The intune docuemtantation is simple enough to use with JAMF. Deploying Zscaler Client Connector with Microsoft Intune for macOS | Zscaler
- The Zscaler app can be provided in 2 ways. The non-managed app which will not respect any configuration profiles, and a deployable .pkg which is what you want to use. Build the policy to deploy the package as usual, nothing screwy here.
Configuration profiles:
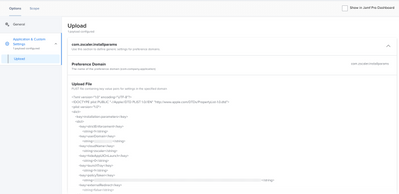
- The install parameters configuration profile. The bread and butter of configuring Zscaler is the com.zscaler.intallparams Configuration Profile. Most of the values are common sense, the userDomain is unique to your organization, and you will get the policyToken from Zscaler. The cloudName will likely be zscaler unless you are doing something specific at which is could be zscaler2 or beta.
Preference Domain: com.zscaler.installparams
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>installation-parameters</key>
<dict>
<key>strictEnforcement</key>
<string>1</string>
<key>userDomain</key>
<string>SomeValueHere</string>
<key>cloudName</key>
<string>zscaler</string>
<key>hideAppUIOnLaunch</key>
<string>0</string>
<key>launchTray</key>
<string>1</string>
<key>policyToken</key>
<string>SomeValueHere</string>
<key>externalRedirect</key>
<string>false</string>
</dict>
</dict>
</plist>
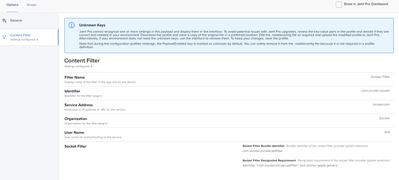
- Socket Filter
- System Extension
- Firewall configuration
Zscailers documentation specifically says you need to modify this for your organizations need, so I am just providing the example they give.
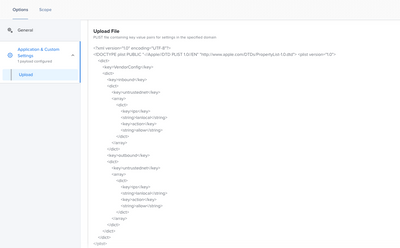
Preference Domain: com.zscaler.socket-filter
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd"> <plist version="1.0">
<dict>
<key>VendorConfig</key>
<dict>
<key>inbound</key>
<dict>
<key>untrustednet</key>
<array>
<dict>
<key>ips</key>
<string>lanlocal</string>
<key>action</key>
<string>allow</string>
</dict>
</array>
</dict>
<key>outbound</key>
<dict>
<key>untrustednet</key>
<array>
<dict>
<key>ips</key>
<string>lanlocal</string>
<key>action</key>
<string>allow</string>
</dict>
</array>
</dict>
</dict>
</dict>
</plist>
- Root Certificate
Zscaler will also need a root certificate to be deployed with JAMF.
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-12-2023 06:22 AM
The firewall configuration (com.zscaler.socket-filter) is provided by zscaler as a template, what we use is in the examples above. You will need to work with the zscaler team to determine what keys you want to use and what they need to be set to based on your organizations needs.
Blocking/filtering all traffic works very poorly, especially if you want things like Apple (OS Updates, MDM Commands, etc) and JAMF to work when zscaler is not authenticated. The more heavy handed the configuration, the more bypasses/exemptions will be needed. We are similar in requiring all traffic to flow through zscaler, over the past 6 months I have had hundreds of hosts and ports exempted in the pac file for things to actually work correctly.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-12-2023 05:01 AM
@AJPinto Thanks for this post.
We have also implemented zscaler and it seems to work good for us. I am wondering where I can find the Zscaler documentation regarding Firewall Rules and Socket Filter. In our environment we haven´t configured this, we only allowed incoming traffic for zscaler.
Do you have the links to firewall and socket filter samples
Thanks in Advance
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-12-2023 06:22 AM
The firewall configuration (com.zscaler.socket-filter) is provided by zscaler as a template, what we use is in the examples above. You will need to work with the zscaler team to determine what keys you want to use and what they need to be set to based on your organizations needs.
Blocking/filtering all traffic works very poorly, especially if you want things like Apple (OS Updates, MDM Commands, etc) and JAMF to work when zscaler is not authenticated. The more heavy handed the configuration, the more bypasses/exemptions will be needed. We are similar in requiring all traffic to flow through zscaler, over the past 6 months I have had hundreds of hosts and ports exempted in the pac file for things to actually work correctly.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-04-2024 12:57 PM
@AJPinto wrote:
..
over the past 6 months I have had hundreds of hosts and ports exempted in the pac file for things to actually work correctly.
This is the hardest part. Zscaler has been in our environment for years and it's still taking figurative-acts-of-god to get proper exemptions in place for ZCC, VPN, and the default proxy .pac file to prevent users from being soft-bricked with Macs having no connectivity and no way to remotely support them.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-14-2024 03:21 PM
@AJPinto I've been stuck in this hell, trying to setup the installparams, I'm trying to enforce the hideAppUIOnLaunch that I have set as 1, every thing else is the same as far as our config goes, but in our case its not doing anything. After the user logs on their desktop the UI will pop up and that is what we are trying to stop.
Sorry for resurrecting this...