- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-02-2023 05:20 AM
Is there a way to enable reasonable security audit log retention via script to comply with CIS Level 1 requirements? Thank in advance
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-02-2023 06:08 AM
For Ventura, try this
chflags nouchg /etc/security/audit_control; sleep 2; /usr/bin/sed -i.bak 's/^expire-after.*/expire-after:60d OR 1G/' /etc/security/audit_control; /usr/sbin/audit -s
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-02-2023 05:32 AM
Hey @deep786
Yes this can be achieve with the following where $ODV is the organisational defined value.
/usr/bin/sed -i.bak 's/^expire-after.*/expire-after:$ODV/' /etc/security/audit_control; /usr/sbin/audit -s
To check the current set value
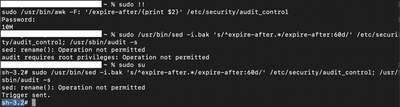
/usr/bin/awk -F: '/expire-after/{print $2}' /etc/security/audit_control
Hopefully this is helpful!
Cheers,
Thijs
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-02-2023 05:53 AM
not able to edit "audit_control" file , Error permission denied
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-02-2023 06:02 AM
I am login as a root user but still not able to edit.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-02-2023 06:08 AM
For Ventura, try this
chflags nouchg /etc/security/audit_control; sleep 2; /usr/bin/sed -i.bak 's/^expire-after.*/expire-after:60d OR 1G/' /etc/security/audit_control; /usr/sbin/audit -s