Welcome to Part 3 of our discussion of Certificates, SCEP, and 802.1x. In our previous post we took a look at how Active Directory Certificate Services works. In our final part in this series, we will explore SCEP and 802.1x.
What is SCEP?
- SCEP = Simple Certificate Enrollment Protocol
What does SCEP do?
- SCEP is a certificate management protocol that helps IT administrators issue certificates automatically.
- SCEP is used by a Windows Server Role called NDES or offered as a service by a third-party Certification Authority (CA).
What is NDES?
- NDES = Network Device Enrollment Service
- NDES is a Windows Server Role Service which works with the Active Directory Certificate Services Role to distribute certificates via SCEP.
What does NDES do?
- NDES allows software on routers and other network devices (e.g., Macs and iPads) running without domain credentials to obtain certificates based on the Simple Certificate Enrollment Protocol (SCEP).
How does NDES work?
- NDES uses the Microsoft Internet Information Services (IIS) web server to allow supplicants to connect and request certificates.
- When a request comes in it is processed by a web application that runs via IIS. This application is what handles the SCEP authentication flow and passes the request to the Certificate Authority, then passes the signed certificate back to the supplicant.
How is SCEP used with Active Directory and NDES?
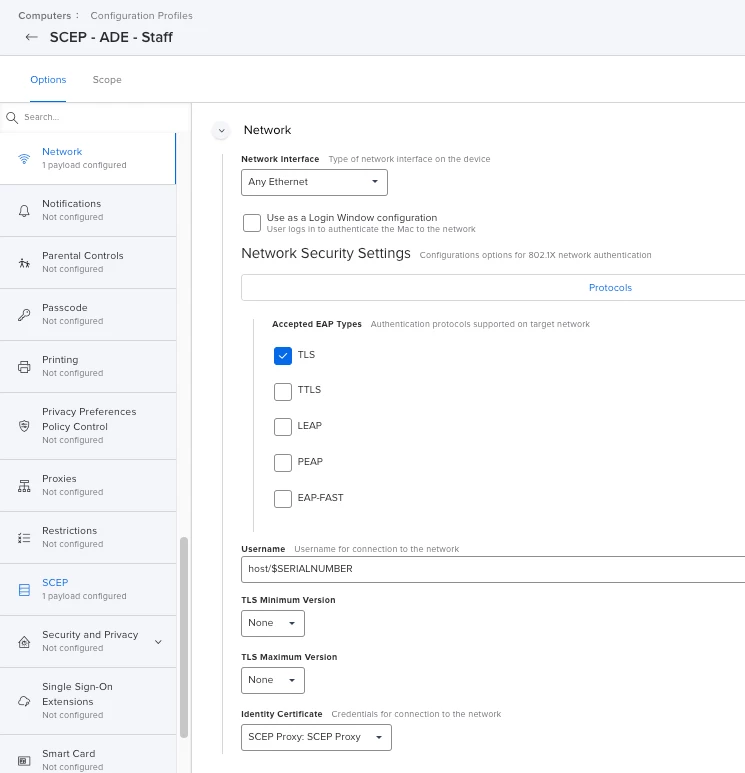
- A SCEP profile is created and distributed to a computer via MDM. This profile includes information on what information the certificate should contain and how to create the Certificate Signing Request (CSR).
- The NDES server is configured to match incoming requests to a Certificate Template on the CA server. Only one Certificate Template can be used with one SCEP server.
- During the installation of the profile, the Certificate Signing Request is sent by a supplicant (a computer or device, or by Jamf Pro in some configurations) to the Certification Authority. For Active Directory environments not using AD CS Connector, NDES is the service that listens for these requests on behalf of the Certification Authority.
- There is a form of authentication used with SCEP called a challenge which prevents unwanted supplicants requesting a certificate. This is seen as the Challenge Type in configuration profiles.
- Dynamic Challenges require authentication by a service account to receive the challenge password, which is then used to authenticate the CSR.
- Static Challenges require only a pre-shared key which is used to authenticate the CSR.
- Other challenge types require information determined by the certification authority used.
- Once the request has been authenticated by SCEP, it is sent to the CA which verifies that the certificate request is valid, then creates and signs the certificate based on the certificate template specified by the SCEP server.
- Once signed, the certificate is sent back to the supplicant (or to Jamf Pro, then to the supplicant) and installed on the device.
What is NPS?
- NPS = Network Policy Server
- NPS is a Windows Server Role which includes the RADIUS role service. This role allows admins to create and enforce organization-wide network access policies for connection request authentication and authorization.
What is RADIUS?
- RADIUS = Remote Authentication Dial-In User Service
What does a RADIUS server do?
- RADIUS is a networking protocol that provides centralized authentication, authorization, and accounting management for users who connect and use a network service.
- RADIUS servers allow organizations to utilize a central database (or directory) to maintain user profiles that remote servers and services can share for authentication to network resources.
- RADIUS clients are the network access points that computers or devices connect to (wireless routers, VPNs, etc.).
What does NPS do?
- NPS allows admins to centrally configure and manage network access authentication and authorization.
- NPS performs centralized authentication, authorization, and accounting for wireless, authenticating switch, remote access dial-up and virtual private network (VPN) connections.
- When admins use NPS as a RADIUS server, they configure network access servers, such as wireless access points and VPN servers, as RADIUS clients in NPS.
- Admins can also configure network policies that NPS uses to authorize connection requests, and admins can configure RADIUS accounting so that NPS logs accounting information to log files on the local hard disk or in a Microsoft SQL Server database.
What is 802.1x?
- 802.1x is a standard that defines how to provide authentication for devices that connect with other devices on local area networks.
- 802.x networks utilize a RADIUS server for authentication.
- Two popular authentication protocols used with 802.1x networks are:
- EAP-TLS – Certificate-based authentication.
- EAP-PEAP – Credential-based authentication (username/password).
While 802.1x is nothing more than an authentication standard, it is often used as descriptor for a wireless network which uses 802.1x authentication.
What does an 802.1x network do?
- 802.1x networks are Wi-Fi, wired, or virtual (VPN) networks which require a specific kind of authentication to access.
- EAP-TLS authentication utilizes TLS encryption provided by the authentication server and authenticates the user or device based on a pre-installed certificate.
- EAP-PEAP authentication utilizes TLS encryption provided by the authentication server to encrypt the username and password during authentication. It often uses Active Directory authentication rather than a Pre-Shared Key.
How does macOS work with 802.1x networks?
Information provided from Apple Documentation: Connect Apple devices to 802.1X networks
- During the 802.1X negotiation, the RADIUS server presents its certificate to the device supplicant automatically.
- The RADIUS server certificate must be trusted by the supplicant by either anchoring trust to a particular certificate or to a list of expected hostnames matching the certificate’s host. Even when a certificate is issued by a known CA and listed in the trusted root store on the device, it must also be trusted for a particular purpose.
- This is either done manually when joining an enterprise network as the user is prompted to trust the certificate for the connected Wi-Fi network, or in a configuration profile.
- Once the RADIUS server is authenticated to the supplicant, the supplicant then sends its own credentials based on the security type required by the RADIUS server.
- There are two basic types of 802.1x configurations used with macOS:
- User Mode: This mode, the simplest to configure, is used when a user joins the network from the Wi-Fi menu and authenticates when prompted. The user must accept the RADIUS server’s X.509 certificate and trust for the Wi-Fi connection.
- This is often not configured with Jamf Pro because admins want the user workflow to be as simple and painless as possible.
- System Mode: System Mode is used for computer authentication. Authentication using System Mode occurs before a user logs in to the computer. System Mode is commonly configured to provide authentication with the computer’s X.509 certificate (EAP-TLS) issued by a local certificate authority.
Common network and configuration profile terms
Some information provided from Apple Documentation: Connect Apple devices to 802.1X networks
- SSID = Service Set Identifier. Otherwise known as the name of a Wi-Fi network.
- Pre-Shared Key – A password or string of random characters which is known and distributed for authentication. Otherwise known as the Wi-Fi password you give to friends when they come over to your home to hang out.
- Hidden Network – A network which does not broadcast its SSID. You must know the name of the network and connect to it manually (or be provided with the network information via MDM).
- Security Type – Encryption used when connecting to wireless networks.
- WEP – Wired Equivalent Privacy. The oldest wireless security protocol. No longer recommended to be used as it provides weak security.
- WPA – Wi-Fi Protected Access. An older method of encrypting connections to wireless networks. Authentication typically happens on the router which broadcasts the wireless network
- WPA2 Personal – The 2nd version of WPA. A common encryption method used for small office and home wireless networks. More secure than WPA due to advances in security technology.
- WPA3 Personal – The 3rd and currently newest version of WPA which everyone will eventually migrate to. More secure than WPA2 due to advances in security technology.
- WPA/2/3 Enterprise – An implementation of WPA protocols which utilizes a RADIUS server for authentication rather than the router which broadcasts the network.
- Username – The username used to connect to the network. Only used with EAP-PEAP or similar user credential authentication protocols.
- Identity Certificate – The certificate used to identify the user or computer which is connecting to the network. This is the authentication credential which is passed on to the NPS/RADIUS server to evaluate the connection attempt.
- It’s not necessary to establish a chain of certificate trust in the same profile that contains the 802.1x configuration. For example, an administrator can choose to deploy an organization’s certificate of trust in a standalone profile and can put the 802.1x configuration in a separate profile. This way, modifications to either profile can be managed independently of one another.
- Trusted Certificates – If the RADIUS server’s leaf certificate is supplied in a Certificates payload in the same profile that contains the 802.1x configuration, the administrator can select it here. This configures the client supplicant to connect only to an 802.1x network with a RADIUS server presenting one of the certificates in this list.
- This field is commonly misconfigured by selecting certificate payloads included with the profile to establish the chain of trust for the identity certificate.
- This field should ONLY have a value to configure supplicants to connect to RADIUS server presenting the exact same certificate as what is selected here.
- Trusted Server Certificate Names - Use this field to configure the supplicant to connect only to RADIUS servers presenting certificates that match these names.
- This field is commonly misconfigured by entering the FQDN of CA’s or the CN of the identity certificate or its chain of trust.
- This field should ONLY have a value to configure the supplicants to only connect to a RADIUS server which presents a certificate with a CN which matches the value of this field.
How does an 802.1x profile connect a computer to a Wi-Fi network?
This is a simplified explanation to use as a high-level overview of the process. Connecting to 802.1x networks can be as simple or complex as a network administrator wants it to be.
- A configuration profile is created in Jamf Pro with a network payload.
- If using EAP-TLS for the security type it also includes at least one certificate payload for the identity certificate.
- Depending on the admins environment there may also be a SCEP payload.
- The profile is installed onto a target supplicant in its scope. This installs the necessary certificate to authenticate to the RADIUS server for an EAP-TLS network.
- If configured to auto-connect, the supplicant will then attempt to connect to the 802.1x network with the information provided in the profile.
- The supplicant contacts the wireless router and requests a connection. This connects the supplicant to a RADIUS server.
- When communicating with the RADIUS server, the supplicant will be presented a certificate identifying the RADIUS server.
- Depending on the profile configuration, either the certificate common name (CN) or the certificate itself must match to the configured Trusted Server Certificate Names or Trusted Certificates.
- Once the RADIUS server is authenticated to the supplicant, the supplicant then sends authentication credentials (username/password for EAP-PEAP or the identity certificate for EAP-TLS) to the RADIUS server.
- If this is a RADIUS server installed under NPS on a Windows Server, NPS evaluates the authentication credentials and security policies, then accepts or rejects the authentication attempt based on those security policies. The credentials should then be authenticated by the RADIUS server.
- If accepted, the RADIUS server communicates with the wireless router to accept the supplicant's credentials.
- The supplicant is now connected to the 802.1x network.
Due to the way the EAPOL client which handles 802.1x authentication on macOS devices is written, if a payload includes certain settings and the macOS computer cannot connect to the network due to a misconfiguration somewhere, strange things start happening on the computer.
If Trusted Certificates or Trusted Certificate Names are configured with the profile payload it prevents the computer from interacting with the user to connect to the 802.1x network. However, macOS computes will attempt the connection in a different way, often confusing users and admins to what exactly is broken.
That’s all for this series, thank you for reading!