Background
Like most organizations, we want the best — most secure — experience for our users. So, naturally, we’ve investigated leveraging Managed Apple IDs.
While Managed Apple IDs come with some significant limitations, my personal favorite has to be:
Allows browsing but not purchasing, paid or free in: App Store
However, the promise of a Shared iPad is quite alluring.
The Rub
I also suspect “the rub” for most organizations who wish to federate their domain is Apple’s unwillingness to inform the enterprise which of the enterprise’s users will be impacted before federation is enabled:
… but you can’t see their actual personal Apple ID.
Get notified about federated authentication user name conflicts, Item No. 7
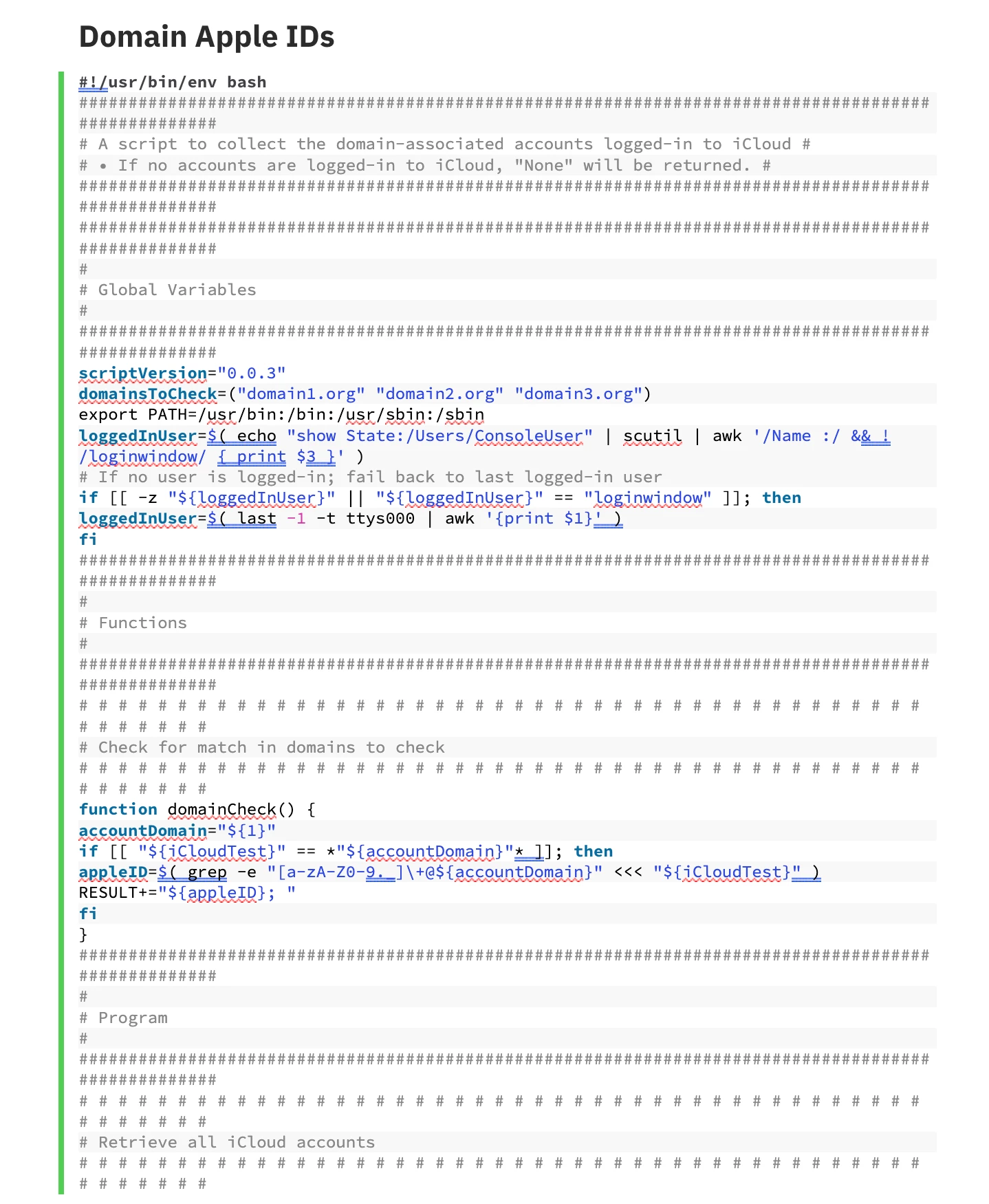
Script
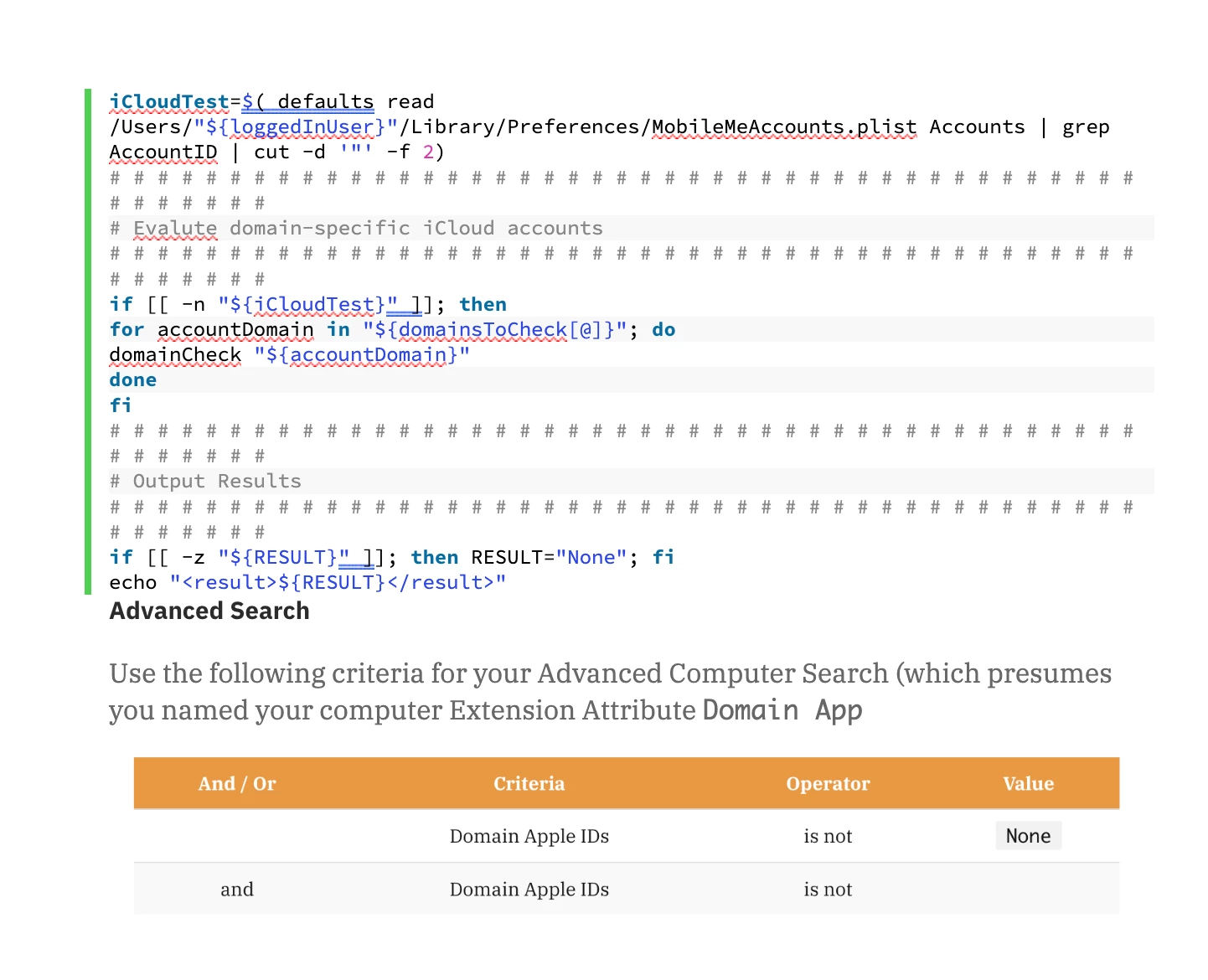
The following Domain Apple IDs Jamf Pro Computer Extension Attribute will inspect the current (or previous) logged-in user’s MobileMeAccounts.plist for Apple IDs associated with domains included in the domainsToCheck array and return a semicolon-delimited list.
Note: The presumption is that your Mac users have configured an organizationally associated Apple ID on a managed Mac; organizationally associated Apple IDs in-use on iOS / iPadOS devices won’t be caught by this net.