- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Jamf Protect
- Threat Prevention
- Analytics
- Unified Logs
- Telemetry
- Device Controls
Jamf Protect Telemetry
<record version="11" event="AUE_ssauthorize" modifier="0" time="Tue Feb 14 22:14:04 2023" msec=" + 143 msec" >
<subject audit-uid="allen.golbig" uid="allen.golbig" gid="staff" ruid="allen.golbig" rgid="staff" pid="2578" sid="100013" tid="6357 0.0.0.0" />
<text>system.print.admin</text>
<text>client /System/Library/Frameworks/ApplicationServices.framework/Versions/A/Frameworks/PrintCore.framework/Versions/A/printtool</text>
<text>creator /System/Library/Frameworks/ApplicationServices.framework/Versions/A/Frameworks/PrintCore.framework/Versions/A/printtool</text>
<return errval="success" retval="0" />
<identity signer-type="1" signing-id="com.apple.authd" signing-id-truncated="no" team-id="" team-id-truncated="no" cdhash="0x1cb1be1d7de2da830093598ce3361797ce861fe3" />
</record>Unified Logs
Jamf Protect Analytics
- ESFPlayground (https://themittenmac.com/the-esf-playground/)
- ProcessMonitor (https://objective-see.org/products/utilities.html)
- Crescendo (https://github.com/SuprHackerSteve/Crescendo)
- eslogger (macOS Ventura)
{
"event" : "ES_EVENT_TYPE_NOTIFY_EXEC",
"process" : {
"session_id" : 70982,
"ruid" : 0,
"uid" : 0,
"euid" : 0,
"tty" : "None",
"ppid" : 70982,
"path" : "/usr/libexec/cups/backend/socket",
"responsible_pid" : 70982,
"username" : "root",
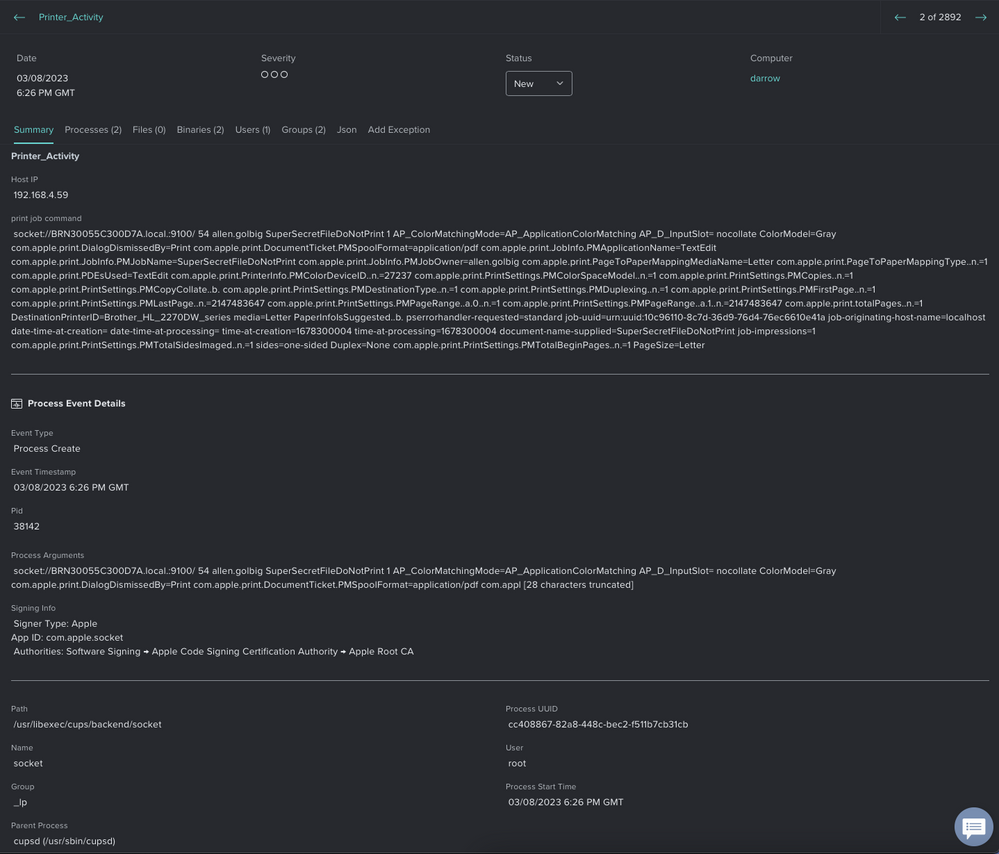
"command" : " socket://BRN30055C300D7A.local.:9100/ 150 allen.golbig test 1 AP_ColorMatchingMode=AP_ApplicationColorMatching AP_D_InputSlot= nocollate ColorModel=Gray com.apple.print.DialogDismissedBy=Print com.apple.print.DocumentTicket.PMSpoolFormat=application/pdf com.apple.print.JobInfo.PMApplicationName=TextEdit com.apple.print.JobInfo.PMJobName=test com.apple.print.JobInfo.PMJobOwner=allen.golbig com.apple.print.PageToPaperMappingMediaName=Letter com.apple.print.PageToPaperMappingType..n.=1 com.apple.print.PDEsUsed=TextEdit com.apple.print.PrinterInfo.PMColorDeviceID..n.=27237 com.apple.print.PrintSettings.PMColorSpaceModel..n.=1 com.apple.print.PrintSettings.PMCopies..n.=1 com.apple.print.PrintSettings.PMCopyCollate..b. com.apple.print.PrintSettings.PMDestinationType..n.=1 com.apple.print.PrintSettings.PMDuplexing..n.=1 com.apple.print.PrintSettings.PMFirstPage..n.=1 com.apple.print.PrintSettings.PMLastPage..n.=2147483647 com.apple.print.PrintSettings.PMPageRange..a.0..n.=1 com.apple.print.PrintSettings.PMPageRange..a.1..n.=2147483647 com.apple.print.totalPages..n.=1 DestinationPrinterID=Brother_HL_2270DW_series media=Letter PaperInfoIsSuggested..b. pserrorhandler-requested=standard job-uuid=urn:uuid:0cb6a68a-5fbb-3a19-7522-64b9aef4b512 job-originating-host-name=localhost date-time-at-creation= date-time-at-processing= time-at-creation=1676433636 time-at-processing=1676433636 document-name-supplied=test job-impressions=1 com.apple.print.PrintSettings.PMTotalSidesImaged..n.=1 sides=one-sided Duplex=None com.apple.print.PrintSettings.PMTotalBeginPages..n.=1 PageSize=Letter",
"team_id" : "",
"pid" : 71070,
"original_ppid" : 70982,
"pgid" : 71070
},
"timestamp" : "2023-02-14 23:00:37"
}I’ll need the signing info for both the process and parent_process now. Running codesign -dv /usr/libexec/cups/backend/socket, I get the following:
Executable=/usr/libexec/cups/backend/socket
Identifier=com.apple.socket
Format=Mach-O universal (x86_64 arm64e)
CodeDirectory v=20400 size=713 flags=0x0(none) hashes=17+2 location=embedded
Platform identifier=14
Signature size=4442
Signed Time=Feb 10, 2023 at 12:51:37 PM
Info.plist=not bound
TeamIdentifier=not set
Sealed Resources=none
Internal requirements count=1 size=64Because this is a printing process, cupsd is the obvious parent_process, running pgrep cupsd outputs 70982, which matches the ppid in the ESFPlaygound output above. Let’s grab the codesign info from /usr/sbin/cupsd.
Executable=/usr/sbin/cupsd
Identifier=com.apple.cupsd
Format=Mach-O universal (x86_64 arm64e)
CodeDirectory v=20400 size=3560 flags=0x0(none) hashes=106+2 location=embedded
Platform identifier=14
Signature size=4442
Signed Time=Dec 17, 2022 at 2:38:11 AM
Info.plist=not bound
TeamIdentifier=not set
Sealed Resources=none
Internal requirements count=1 size=64/System/Library/LaunchDaemons/org.cups.cupsd.plist
/usr/sbin/cupsd 70982$event.type == 1 AND
$event.process.signingInfo.appid == "com.apple.socket"
$event.process.responsible.signingInfo.appid == "com.apple.cupsd"One last thing before checking alerts in Jamf Protect. In the ESFPlayground output, under process_command there was a very long string of text. This is the command line output that the socket binary passes when sending a print job. There will be a lot of useful data contained in that string and that’s where Context Items come into play. Context Items are optional values in Analytics which help define additional conditions that an analytic can evaluate.
Name: print job command
Type: String
Expression: event.process.commandLineNot Everyone Uses a Brother Printer?
- Internet Printing Protocol (IPP)
- Line Printer Daemon (LPD)
- HP Jetdirect - Socket
- AirPrint (combination of IPP and printer discovery)
- USB
# Switch to root
sudo -s
# Run for loop to grab identifiers
for i in /usr/libexec/cups/backend/*; do codesign -dv $i 2>&1 | awk -F'=' '/^Identifier/ {print $2}'; done
com.apple.bluetooth
com.apple.dnssd
com.apple.ipp
com.apple.ipp
com.apple.ipp
com.apple.ipp
com.apple.dnssd
com.apple.lpd
com.apple.dnssd
com.apple.riousbprint
com.apple.smb
com.apple.snmp
com.apple.socket
com.apple.usb- com.apple.socket
- com.apple.ipp
- com.apple.lpd
- com.apple.usb
$event.type == 1 AND
$event.process.signingInfo.appid IN {'com.apple.socket', 'com.apple.ipp', 'com.apple.lpd', 'com.apple.usb'} AND
$event.process.responsible.signingInfo.appid == "com.apple.cupsd"
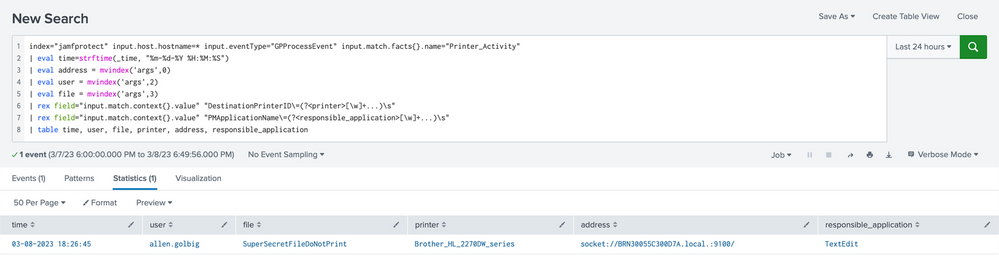
SIEM Example
index="jamfprotect" input.host.hostname=* input.eventType="GPProcessEvent" input.match.facts{}.name="Printer_Activity"
| eval time=strftime(_time, "%m-%d-%Y %H:%M:%S")
| eval address = mvindex('args',0)
| eval user = mvindex('args',2)
| eval file = mvindex('args',3)
| rex field="input.match.context{}.value" "DestinationPrinterID\=(?<printer>[\w]+...)\s"
| rex field="input.match.context{}.value" "PMApplicationName\=(?<responsible_application>[\w]+...)\s"
| table time, user, file, printer, address, responsible_applicationGitHub Repo
- Custom Analytics
- Unified Log Filters
- Jamf Protect API Scripts
- SOAR Playbooks
- Third Party Integrations
- Jamf Pro Extension Attributes
Happy printing!