Hi all,
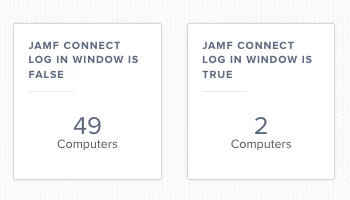
as 12.3 is out just couple hours I went and gave it a try on my lab machines. At first I was surprised taht JAMF Connect (2.10.0) was not shown at user login screen and instead I was presented with native system login.
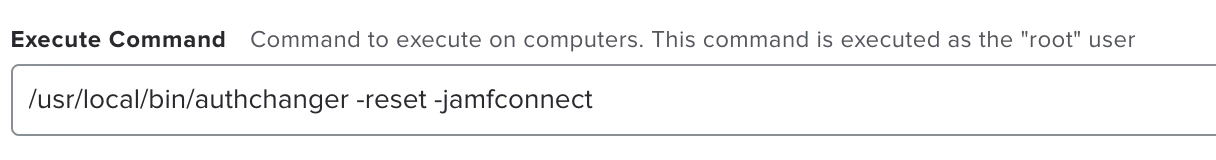
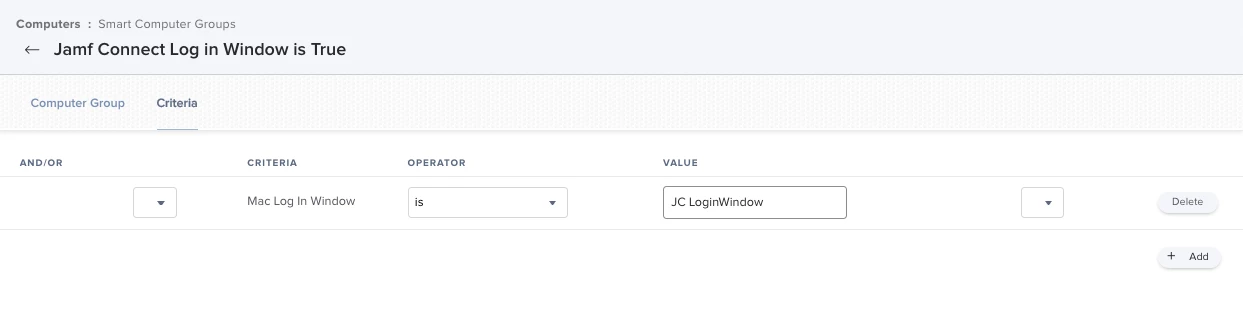
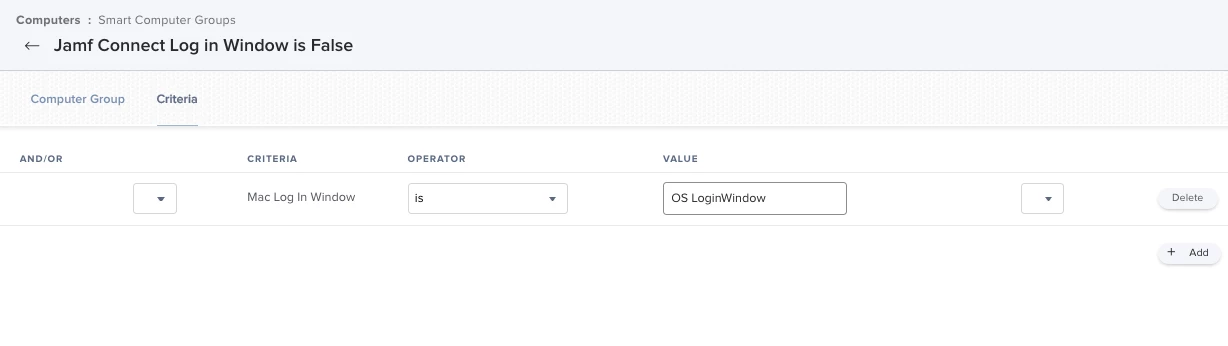
I have discovered that 12.3 is reseting login database and therefore to revert to JAMF Connect login screen there is a need to re-apply authchnager command. In my case I created smart group for all machines installed 12. and scoped policy which only has file and process payload defined with following command "/usr/local/bin/authchanger -reset -jamfconnect" to the smart group earlier created.
Big thanks and creds to TTG and his guide: https://travellingtechguy.blog/re-enable-jamf-connect-login-window-after-major-macos-upgrade-monterey/