- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-24-2021 11:27 PM
Hello,
Today, We found out the Jamf Connect login is not working when connected to our corporate WiFI network which is basically EAP/TLS machine level cert auth with auto-join configured through Configuration Profile.
Does anyone has any solution for this issue ? OR does anyone come across this issue ?
Note: Jamf Connect Login works perfectly fine on home network / mobile hotspot.
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-03-2022 07:11 AM - edited 01-03-2022 07:12 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-27-2021 12:04 PM
We have the same issue with Jamf Connect and our enterprise network, we are using PEAP user level cert with auto join. Our users cannot join our WPA2 Enterprise network at the Jamf Connect login screen even when they are passing their district credentials. Once they're logged into the machine the user can then enter and connect using their credentials. Right now we have a SSID that we are passing the password for via profile to machines so they can authenticate through to login and get to the Home Screen. Which when they get to the home screen they can use their district credentials to log into the Wifi.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-19-2021 10:32 PM
Wifi connection at JAMF Connect login screen is not capable of connecting to networks which depends on Radius Server for user authentication.
Refer to Network requirements section for more infomration.
General Requirements - Jamf Connect Administrator's Guide | Jamf
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-21-2021 05:27 AM
Thanks for that link. There's a section which says "If you are using an 802.1x RADIUS server for certificate-based authentication on your organization's network, you must make sure to distribute 802.1x settings at the computer-level" but gives no indication of how to set it up. Does anyone know what I need to do? Is there some kind of profile or policy that I need to implement to get the 802.1x settings in place?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-03-2022 07:11 AM - edited 01-03-2022 07:12 AM

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-26-2024 11:51 AM
Possible to see what your SCEP payload looks like here?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-03-2022 09:07 PM
i have done all these settings but i m unable to connect wifi at login screen. it is asking credentials to connect but on the same wifi i am able to connect post login via certificate authetication.
Pls advise
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-11-2023 10:52 AM
Hi,
Has anyone been able to resolve this issue? In our company, user-based authentication is done, not device-based to connect to the WIFI network.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-12-2023 06:56 AM
Hi Everyone,
I solved the 802.1x problem. You can contact me here to find out how to solve the problem.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-01-2023 02:24 AM
Hello husnudagidir
What was your solution ?
We have exactly the same problem. Please post your solution here for the benefit to everyone.
Regards
Rolf
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-08-2023 12:51 PM
Hi,
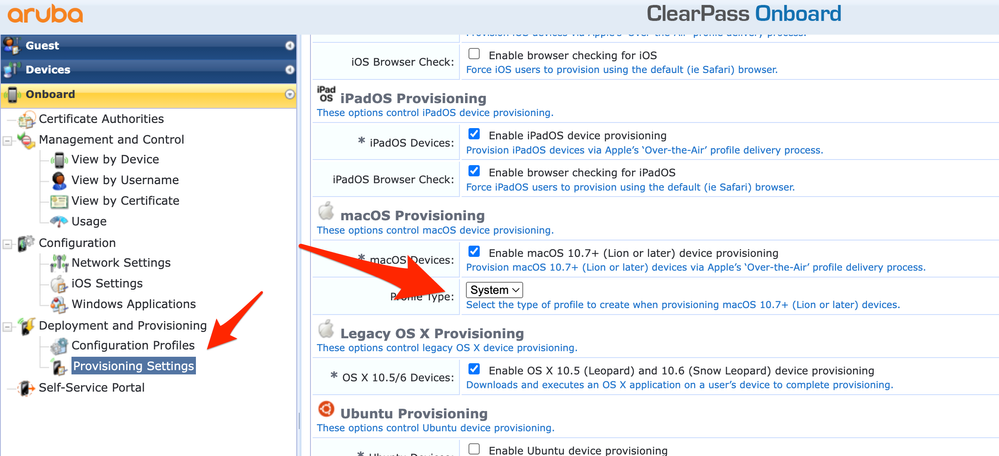
We use Aruba brand Access Points in our WIFI network. 802.1x is used to connect to the network through these products and we include users in the network by verifying with a certificate. At this stage, identity and certificate verification is done with an application called ClearPass. The ClearPass application also serves as an MDM server and SCEP server. When we connect to Access Points, the ClearPass application sends a profile file to users via a web interface. Actually the whole solution is contained in this profile file settings. We changed the part specified as "user" in the settings of this configuration profile file, sent to MacOS devices by the ClearPass application, to "system". Thus, as soon as our MacOS device was turned on, the user was able to connect to the network automatically without logging in. If the application you use is ClearPass, I can support this article with screenshots.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-08-2023 01:03 PM
Hi rolfk,
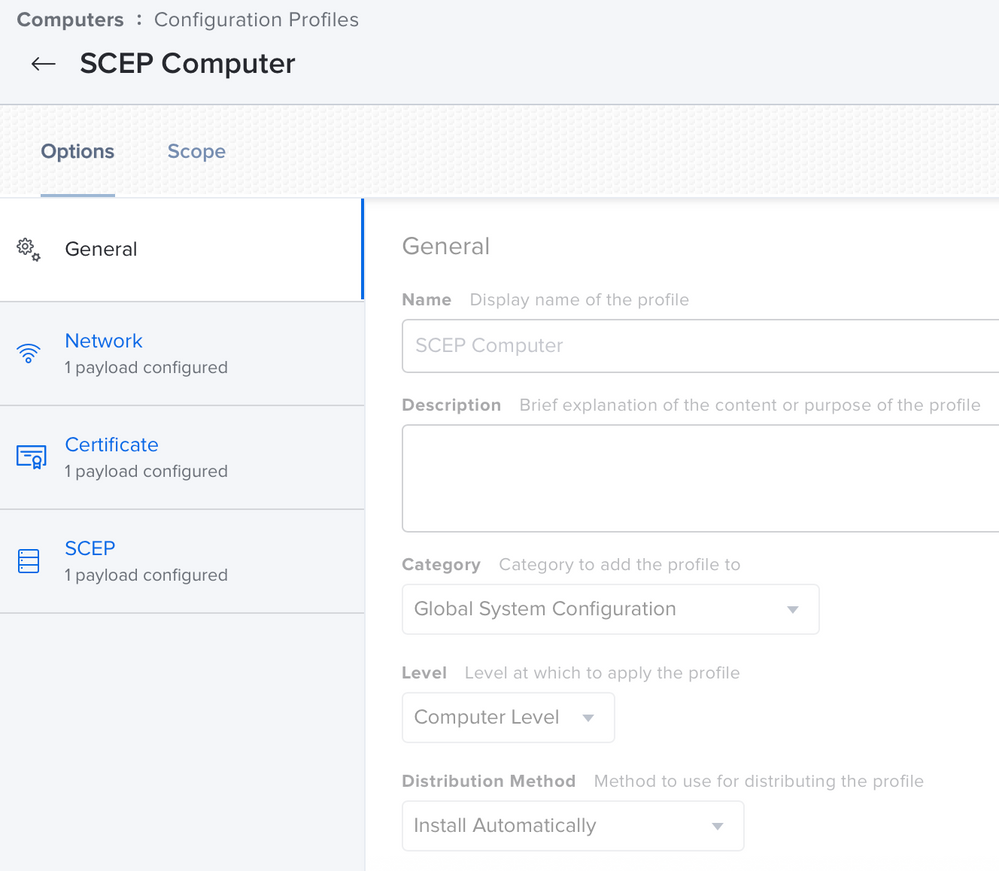
We use Aruba brand Access Points in our WIFI network. 802.1x is used to connect to the network through these products and we include users in the network by verifying with a certificate. At this stage, identity and certificate verification is done with an application called ClearPass. The ClearPass application also serves as an MDM server and SCEP server. When we connect to Access Points, the ClearPass application sends a profile file to users via a web interface. Actually the whole solution is contained in this profile file settings. We changed the part specified as "user" in the settings of this configuration profile file, sent to MacOS devices by the ClearPass application, to "system". Thus, as soon as our MacOS device was turned on, the user was able to connect to the network automatically without logging in. If the application you use is ClearPass, I support this article with screenshots. You can use the screenshot below. After making this change, you need to delete and reinstall the WIFI profile on the macOS device. After this step, the problem disappears.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-18-2024 07:09 AM
Would you mind sharing your service profile that allows for the authentication of i-devices to your network??
I have to set up something similar for ipads to connect to our corporate network using certificates pushed from JAMF using device authentication. They don't want users to have to enter a password.
I appreciate it!!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-01-2023 02:32 AM
u have to enroll machine base certificate to get authenticate wifi and it supports only EAP-TLS authentication but PEAP(user authentication ) so it works only with machine base authentication
and map root CA in your wifi radius server for validation
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-09-2023 06:39 AM
Yes. Already the full solution to this problem is to do machine-based authentication. Because when devices enter the environment, they must be connected to the internet without being dependent on user authentication. Otherwise Jamf Connect will not work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-21-2023 03:50 PM
This is not a solution, but a workaround. Not all enterprises allow or want to allow device based authentication. This has been on the known issues list for a while now. I will create another support case on this. We had a ticket in a while back, but just got the standard device based workaround answer. I don’t see how this is a technical limitation, user based authentication works just fine in macOS. If it is a limitation by Apple, we should put some pressure in that direction as well.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-12-2023 01:29 PM
Hi,
For us, this is not a temporary solution. Since device-based verification occurs after verification and approval by IT teams, it does not pose a risk to information security as all necessary protocols are implemented. It is not possible for an external device to join the network in any way. It is safe because it uses 802.1x and certificates and works with the profile support sent to this device by ClearPass.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-05-2024 02:00 PM
Hi, would you be able to explain this a bit more? I am new to Jamf and running into this as well. We user ClearPass.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-20-2024 09:56 PM
Hi,
Can you tell me exactly what you want to do and what your goal is? I think I can help you. We also use Clearpass in our environment. I would be happy to share my experiences and solutions.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-21-2024 06:26 AM
My current problem is that when we're in our corporate WIFI and do a fresh restart/reboot, we cannot login as we get a blank window at our SSO login screen. If I am hardwired, I have no issues, but if I am on wifi I have to turn wifi off and use the Local login. This isn't a great user experience, so I am trying to figure out what I am missing to get this working correctly while on WIFI, I am just too new to Jamf that I am not sure what I am missing. We currently push our Corp WIFI profile via Jamf and there are no issues once our Users log into the machine, there's no issues if the laptop wakes up from sleep mode, wifi connects fine. This happens on a fresh start-up at the initial SSO login. Appreciate any guidance. Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-29-2025 12:43 AM
Your problem is that the certificate is in the user, not the system. Therefore, you cannot connect without logging in as a user. The certificate field should also appear as system in the WIFI profile you sent with Jamf.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-29-2025 08:09 AM
The certificate is pushed to the system, its applied at a computer level vs. a user level.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-30-2025 05:45 AM
Is the autojoin option active in the network profile?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-30-2025 06:15 AM
Yes, we have that optioned checked.