- Jamf Nation Community
- Community & Events
- Jamf Nation
- Cisco Secure Client 5.1.0.136 - System Certificate...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-21-2023 03:48 PM
The adventures of deploying Cisco's Secure Client continue... After going through Cisco's documentation, the HCS technology group guide, and building a PKG, changing the choices XML, and creating the config profile , I have hit another snag. When deploying through a policy, the install fails:
Script result: installer: Package name is Cisco Secure Client
installer: choices changes file '/private/tmp/csc_choices.xml' applied installer: Installing at base path / installer: The install failed. (The Installer encountered an error that caused the installation to fail. Contact the software manufacturer for assistance. An error occurred while running scripts from the package “Cisco Secure Client.pkg”.)
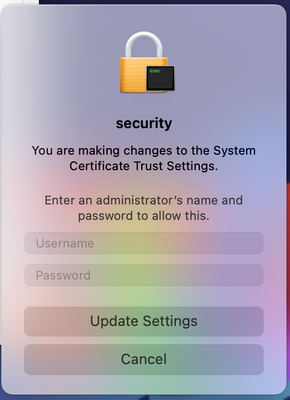
However, if I push the policy through sudo jamf policy , the installer will go through and this will appear:
If I click "cancel" the installation completes and everything seems to be in working order. I see the Umbrella Module appear and it is indeed active.
Admittedly, I am newish it jamf, so I am sure I've made a mistake somewhere along the billion steps that are necessary in getting this Secure Client deployed. Any ideas on where I could have screwed up?
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-12-2024 12:49 PM
SO, after hours of sleuthing, I found the issue. The Secure Client PKG I am using packages Duo Desktop along with it. The installation errors were occurring due to cert I didn't for DUO not the Secure Client... SUPER ANNOYING. And none of Cisco's documentation mentioned anything about needing a cert for DUO, which is hilarious because I don't even need DUO in the first place... Anyways, if anyone comes across this issue, follow the instructions here to create and push out the config for DUO before installing the Cisco Secure Client: https://help.duo.com/s/article/6403?language=en_US
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-22-2023 06:08 AM
@Jmardian That message implies that the install .pkg is attempting to add a certificate to your System keychain using a script, and that has not been allowed without admin user interaction since macOS Big Sur. If you know what that certificate is you could deploy it via a Certificate payload in a Configuration Profile.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-22-2023 09:09 AM
Thanks for the reply! I have the root certificate pushed out and I still get the message. I think the bigger concern I have is that the Secure Client PKG won't install unless I force the deployment through sudo jamf policy in Terminal. What would block the install from happening through cloud distribution, but allow it manually in Terminal?
Although its messy and I don't like it, simply clicking cancel on that message allows the package to install. If I can get the package to download through the policy cloud distribution, I'll cut my loses and have the users just click cancel to allow the download to happen.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-22-2023 01:37 PM
I don't have personal experience with Cisco Secure Client, so my suggestion would be to engage Cisco support and ask them if it is possible to do a non-interactive install, and if so exactly what is the process for that since their published docs aren't correct.
As to why it works when initiated via Terminal versus a policy running on checkin, it's probably that the policy was initiated via a user session for the former, while the latter would be running as root and I think the installer is smart enough to know it can't prompt from the root context.
A Self Service initiated install _might_ trigger the same behavior as you're seeing triggering the policy from Terminal, but I would not recommend using that approach.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-27-2023 04:05 AM
How to create custom Pkg of Cisco secure client from DMG file
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-27-2023 05:13 AM
How to create custom Pkg of Cisco secure client from DMG file
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-27-2023 07:52 AM
so I create a pkg of the certs using Composer and then run a script after it to install the pkg, install certs and trust, then remove the certs and temp directory I install them in. Looks like this and they do not get a popup.
#!/bin/bash
sudo security authorizationdb read com.apple.trust-settings.admin > /tmp/security.plist
sudo security authorizationdb write com.apple.trust-settings.admin allow
sudo security add-trusted-cert -d -r trustRoot -k /Library/Keychains/System.keychain "/path/to/cert/mycert.cer"
sudo security add-trusted-cert -d -r trustAsRoot -k /Library/Keychains/System.keychain "/path/to/cert/mycert.cer"
sudo security authorizationdb write com.apple.trust-settings.admin < /tmp/security.plist
sudo rm -rf srm /path/to/cert/mycert.cer
sudo rm -rf srm /path/to/cert/mycert.cer
sudo rm -rf srm /path/to/cert/
rm /tmp/security.plist
exit 0- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-12-2024 12:49 PM
SO, after hours of sleuthing, I found the issue. The Secure Client PKG I am using packages Duo Desktop along with it. The installation errors were occurring due to cert I didn't for DUO not the Secure Client... SUPER ANNOYING. And none of Cisco's documentation mentioned anything about needing a cert for DUO, which is hilarious because I don't even need DUO in the first place... Anyways, if anyone comes across this issue, follow the instructions here to create and push out the config for DUO before installing the Cisco Secure Client: https://help.duo.com/s/article/6403?language=en_US
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-21-2024 01:31 PM
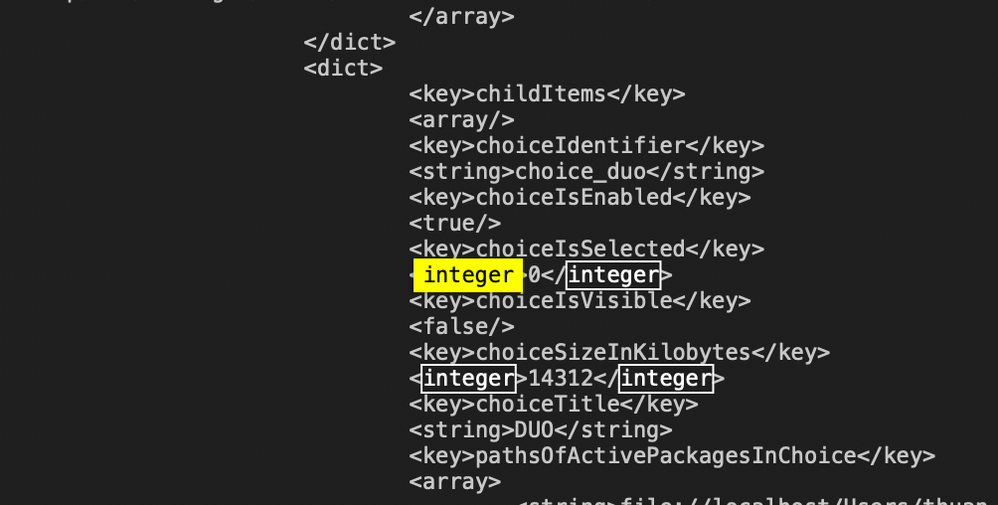
How annoying. Got it all to work, but Cisco Secure Client 5.1.2.42 package asks for Duo System Cert. Will try the .XML Choice path. I'd rather not have to add a config with a cert for a product we're not even using.
@Jmardian So you did the XML choice and excluded Duo? And still had to create and push a config for Duo?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-21-2024 02:17 PM
So, I work in a school environment and I was in a time crunch to get the Umbrella mobile client working. Once I got everything working I just stopped there despite it being a convoluted sequence of policies and configs. Basically, I am adding the DUO cert and then running the policy that downloads the secure client. Once everything is downloaded I have another policy that removes DUO. A very ugly way of doing it, I know, but it works for now. I will try the XML route over summer when I have access to the devices in a testing environment.
If anyone has been successful with the XML choice and removing DUO from it, I'd be grateful to see it. The XML choice that I pulled from JAMF didn't even have DUO as an option.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-22-2024 06:17 AM
I see the xml options for Duo and Thousand Eyes in Cisco Secure Client 5.1.2.42. Packaging and going to test it...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-22-2024 10:42 AM
Awesome, maybe I missed it in the 5.1.0.136 PKG. If you don't mind sharing your xml choice file once your done I'd greatly appreciate it!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-22-2024 11:35 AM
I spent a lot of time on the XML choice method. Didn't work for me, and it seemed to give others issues on other threads.
What worked was the pkgutil command to expand and flatten the Cisco Secure Client package. This link below worked nicely, and it was much easier. I did this on version 5.1.2.42.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-22-2024 11:51 AM
Good to know, and thanks for link. I'll give that method a go when it comes time to revisit this mess 😆 or when the secure client breaks, which I expect it will at some point...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-22-2024 12:03 PM
If it helps, here's a script to remove a bunch of the software that comes bundled, including Duo and ThousandEyes agent. Can just tailor to what you need.
#!/bin/bash
/opt/cisco/secureclient/bin/amp_uninstall.sh
/opt/cisco/secureclient/bin/dart_uninstall.sh
/opt/cisco/secureclient/bin/iseposture_uninstall.sh
/opt/cisco/secureclient/NVM/bin/nvm_uninstall.sh
/opt/cisco/secureclient/bin/umbrella_uninstall.sh
/opt/cisco/secureclient/bin/zta_uninstall.sh
### Uninstall Duo Desktop and Duo Device Health
/Applications/Duo\ Desktop.app/Contents/Library/LaunchServices/com.duosecurity.UninstallDuoDeviceHealth
/Applications/Duo\ Device\ Health.app/Contents/Library/LaunchServices/com.duosecurity.UninstallDuoDeviceHealth
### Uninstall ThousandEyes Agent
/Applications/Cisco/Cisco\ Secure\ Client\ -\ ThousandEyes\ Endpoint\ Agent.app/Contents/Resources/uninstall.sh
exit 0
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-21-2024 07:54 AM
this was fantastic! great job!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-14-2024 12:50 PM
Hey everyone,
I just ran into this same issue with the new Secure Client VPN 5.1.2.42 with the extra "garbage" that it installs. It seems like many others are also having this issue so going to post what I created to help out. I was able to create a choice XML file that turns it all off so only the VPN agent is installed. Feel free to tweak for your needs.
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<array>
<dict>
<key>attributeSetting</key>
<true/>
<key>choiceAttribute</key>
<string>visible</string>
<key>choiceIdentifier</key>
<string>choice_anyconnect_vpn</string>
</dict>
<dict>
<key>attributeSetting</key>
<false/>
<key>choiceAttribute</key>
<string>enabled</string>
<key>choiceIdentifier</key>
<string>choice_anyconnect_vpn</string>
</dict>
<dict>
<key>attributeSetting</key>
<integer>1</integer>
<key>choiceAttribute</key>
<string>selected</string>
<key>choiceIdentifier</key>
<string>choice_anyconnect_vpn</string>
</dict>
<dict>
<key>attributeSetting</key>
<true/>
<key>choiceAttribute</key>
<string>visible</string>
<key>choiceIdentifier</key>
<string>choice_fireamp</string>
</dict>
<dict>
<key>attributeSetting</key>
<false/>
<key>choiceAttribute</key>
<string>enabled</string>
<key>choiceIdentifier</key>
<string>choice_fireamp</string>
</dict>
<dict>
<key>attributeSetting</key>
<integer>0</integer>
<key>choiceAttribute</key>
<string>selected</string>
<key>choiceIdentifier</key>
<string>choice_fireamp</string>
</dict>
<dict>
<key>attributeSetting</key>
<true/>
<key>choiceAttribute</key>
<string>visible</string>
<key>choiceIdentifier</key>
<string>choice_dart</string>
</dict>
<dict>
<key>attributeSetting</key>
<false/>
<key>choiceAttribute</key>
<string>enabled</string>
<key>choiceIdentifier</key>
<string>choice_dart</string>
</dict>
<dict>
<key>attributeSetting</key>
<integer>0</integer>
<key>choiceAttribute</key>
<string>selected</string>
<key>choiceIdentifier</key>
<string>choice_dart</string>
</dict>
<dict>
<key>attributeSetting</key>
<true/>
<key>choiceAttribute</key>
<string>visible</string>
<key>choiceIdentifier</key>
<string>choice_secure_firewall_posture</string>
</dict>
<dict>
<key>attributeSetting</key>
<false/>
<key>choiceAttribute</key>
<string>enabled</string>
<key>choiceIdentifier</key>
<string>choice_secure_firewall_posture</string>
</dict>
<dict>
<key>attributeSetting</key>
<integer>0</integer>
<key>choiceAttribute</key>
<string>selected</string>
<key>choiceIdentifier</key>
<string>choice_secure_firewall_posture</string>
</dict>
<dict>
<key>attributeSetting</key>
<true/>
<key>choiceAttribute</key>
<string>visible</string>
<key>choiceIdentifier</key>
<string>choice_iseposture</string>
</dict>
<dict>
<key>attributeSetting</key>
<false/>
<key>choiceAttribute</key>
<string>enabled</string>
<key>choiceIdentifier</key>
<string>choice_iseposture</string>
</dict>
<dict>
<key>attributeSetting</key>
<integer>0</integer>
<key>choiceAttribute</key>
<string>selected</string>
<key>choiceIdentifier</key>
<string>choice_iseposture</string>
</dict>
<dict>
<key>attributeSetting</key>
<true/>
<key>choiceAttribute</key>
<string>visible</string>
<key>choiceIdentifier</key>
<string>choice_nvm</string>
</dict>
<dict>
<key>attributeSetting</key>
<false/>
<key>choiceAttribute</key>
<string>enabled</string>
<key>choiceIdentifier</key>
<string>choice_nvm</string>
</dict>
<dict>
<key>attributeSetting</key>
<integer>0</integer>
<key>choiceAttribute</key>
<string>selected</string>
<key>choiceIdentifier</key>
<string>choice_nvm</string>
</dict>
<dict>
<key>attributeSetting</key>
<true/>
<key>choiceAttribute</key>
<string>visible</string>
<key>choiceIdentifier</key>
<string>choice_secure_umbrella</string>
</dict>
<dict>
<key>attributeSetting</key>
<false/>
<key>choiceAttribute</key>
<string>enabled</string>
<key>choiceIdentifier</key>
<string>choice_secure_umbrella</string>
</dict>
<dict>
<key>attributeSetting</key>
<integer>0</integer>
<key>choiceAttribute</key>
<string>selected</string>
<key>choiceIdentifier</key>
<string>choice_secure_umbrella</string>
</dict>
<dict>
<key>attributeSetting</key>
<true/>
<key>choiceAttribute</key>
<string>visible</string>
<key>choiceIdentifier</key>
<string>choice_duo</string>
</dict>
<dict>
<key>attributeSetting</key>
<false/>
<key>choiceAttribute</key>
<string>enabled</string>
<key>choiceIdentifier</key>
<string>choice_duo</string>
</dict>
<dict>
<key>attributeSetting</key>
<integer>0</integer>
<key>choiceAttribute</key>
<string>selected</string>
<key>choiceIdentifier</key>
<string>choice_duo</string>
</dict>
<dict>
<key>attributeSetting</key>
<true/>
<key>choiceAttribute</key>
<string>visible</string>
<key>choiceIdentifier</key>
<string>choice_thousandeyes</string>
</dict>
<dict>
<key>attributeSetting</key>
<false/>
<key>choiceAttribute</key>
<string>enabled</string>
<key>choiceIdentifier</key>
<string>choice_thousandeyes</string>
</dict>
<dict>
<key>attributeSetting</key>
<integer>0</integer>
<key>choiceAttribute</key>
<string>selected</string>
<key>choiceIdentifier</key>
<string>choice_thousandeyes</string>
</dict>
</array>
</plist>
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-21-2024 09:38 AM
I need help to create pkg from this choice xml