Hi All,
I've been doing a lot of research on 802.1X certificates as we are looking to move away from AD-binding and move to a software such as JAMF Connect in the very near future. This has brought many challenges while researching, and I think I've just made myself more confused in the process. I'm a novice with networking, so please bear with me on that.
Here is essentially what I need to do: I need to have some way to authenticate with the network at the login window on non-bound machines. I've read that using a machine-based certificate with distribution via SCEP is the way-to-go in this scenario, which is fine at the logon window.
Our security policies require that we have user-based authentication when a person is actively using a machine. So if John Smith logs in, John Smith's credentials need to be used to authenticate against the network, not the machine-certificate used at the logon window.
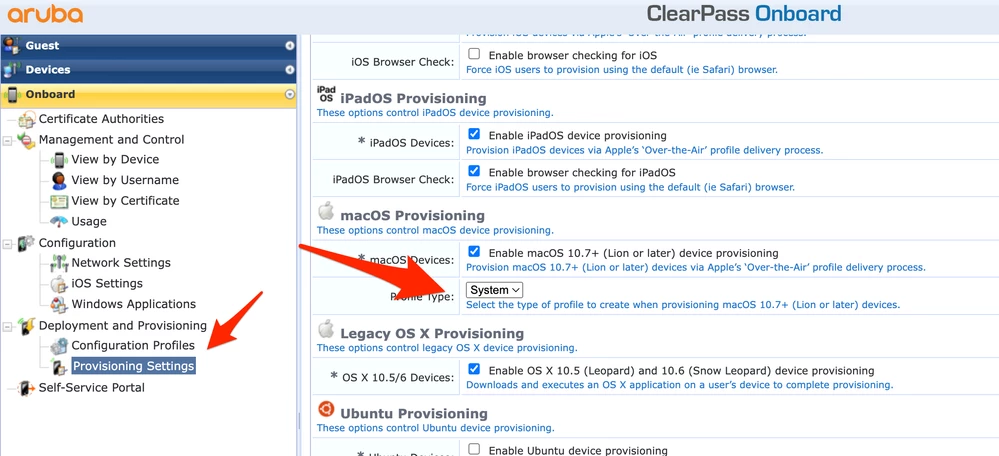
I read in Apple's documentation that you can use a System+User mode for 802.1X authentication, which is exactly what I need to do, but I can't find much documentation in how to create such a configuration. Essentially, I'm looking for guidance on how to configure network authentication per the requirements mentioned above.
We are currently bound to AD and authentication is done when the user logs in and authenticates against AD. We are not actively deploying any certificates, only creating a trust exception for the certificate that is passed when the machine joins the network. The distributed profile is only applied to the login window at the system level.
Any assistance is greatly appreciated!