- Jamf Nation Community
- Products
- Jamf Pro
- Re: 802.1x Machine Authentication Pre Login
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
802.1x Machine Authentication Pre Login
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on
10-29-2018
09:18 AM
- last edited on
03-04-2025
07:38 AM
by
![]() kh-richa_mig
kh-richa_mig
Hello,
PROBLEM: most of our MBP pop solely use wireless network and are never getting alerted when PW is about to expire.
WHAT I HAVE FOUND: On a domain joined machine on our corp wired network, the machine is in a state where it is able to get to AD where it can poll password expiration for users. This is not the case when the device is on our corp wireless. The machine is not getting network access until AFTER a user logs in. I deliver an 802.1x configuration profile to the device with trusted certificates and I am to understand that this profile (which was built using Apple Configurator) installs using a "user" context rather than "system". If delivered in the "system" context, then the device can use the machine certificate for logon. Everything I have seen suggests you must hack the .mobileconfig file (shown here https://ntsystems.it/post/joining-wifi-before-login-on-mac-os-x-108). I tried this several times several ways and have had no luck getting the wireless network to connect at the OSX login screen. Has anyone tried this and had success? As shown in attachment, WiFi not connected with red dot.
- Labels:
-
Jamf Pro
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-29-2018 09:33 AM
We're also using 802.1x with trusted certs and I have the config profile set to Computer Level. it works just fine. One difference is that we are not on Mojave yet. But this configuration has been working in every version since Mavericks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-29-2018 11:50 AM
Thanks for the response. My profile is already set to computer level and my network payload is also delivered with our cert stack. I was unable to get the workflow the way I wanted it with the AD Cert since machine has to be domain bound before the AD cert would apply so I have it deployed separate. Do you mind me asking how your network payload is setup?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-29-2018 11:58 AM
I have the 802.1x config profile scoped to an AD-bound smart group. After the initial imaging/enrollment, I have it join active directory (while plugged into non-802.1x ethernet in our lab), then inventory is run to make sure AD membership puts the computer in the smart group. Then the 802.1x profile pushes out to it. It's not always instant, but it is fairly quick. Notice in my screenshot that I have the AD certificate payload included with network setup and all our other company certs (for completeness).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-30-2018 03:53 AM
Thanks AVmcclint,thanks for clarifying that. Do you mind sharing what your 802.1x network payload looks like? I'm wondering if you have an identity certificate selected in your profile. We were unable to get that to work correctly. It seems like the key to getting the machine to be present on the network pre-login is within that network payload and network authentication.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-30-2018 04:01 AM
I have the AD Certificate selected as the identity certificate since that's what our network requires. Your particular AD Certificate setup will depend on your server's requirements, but once you get that setup then everything else should fall into place. If your network requires a different cert then I would have to imagine you'd have to provide that in a different manner.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-30-2018 03:00 PM
@AVmcclint Thanks for sharing, if you don't mind may I ask why do you have 2 network payloads? I'm trying to get login window authentication working.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-30-2018 05:19 PM
@AVmcclint Thanks for the info, I setup a test configuration profile with our AD cert as the identity cert and will test this. I couldnt get it working during our jumpstart but worth another shot if you're saying it works for you. We use AnyConnect as our network authorization front-end with ISE backend and the MBPs are set to authenticate on the network using THAT AD cert so hopefully it works.
@j.tanudjaja Not to speak out of turn but I have seen people do this when delivering multiple WiFi profile to devices (like if they have different WAPs for different levels of a building etc) but @AVmcclint may be doing it for a different purpose. Good luck to getting your machines to connect to network at login window!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-31-2018 03:21 AM
@j.tanudjaja I have one payload for WiFi and one for Ethernet. @jbjahn is also right. If you have multiple WiFi networks that you need to configure for, you would need payloads for each one.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-01-2018 08:17 AM
@AVmcclint I'm unhappy to update that creating the dot1x profile with AD cert payload did not enable the machine to log onto the network at startup (pre login). The way it should work (the way it does on a wired network), it will reach out to our Identity Services Engine (ISE) for an authentication policy and get handed a default policy so it can authenticate. I don't see it even attempting to reach our ISE server for a policy so it's not even able to get to the network association point pre login.
Looks like I'll just be exploring the use of NoMAD to ensure users get notified of expiring passwords.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-23-2018 01:40 PM
@jbjahn are you sure, i use 802.1X certs on loginwindow without wired network. I can login with my ad account on my fresh installed machine (not connected to lan) via 802.1X Wifi
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-26-2019 09:13 AM
@AVmcclint do you find that you have to enter administrator credentials to connect to your WiFi network when you have Ethernet setup in the same profile?
My profile is setup exactly like yours where we have WiFi and Ethernet using the AD Certificate payload. The problem I'm running into is Ethernet connects just fine but in order to connect to WiFi you have to select the device certificate and enter admin credentials. It's almost like Ethernet takes the device certificate and WiFi is like "umm, what do I use?".
By the way I found that Ethernet works on the login screen but WiFi no longer works even if you establish a network connection by selecting the device certificate. I'm finding that the device certificate only works with one network connection. If you have both using the device certificate it seems to default to Ethernet.
Any help would be great, as I can't seem to figure out why this behavior is occurring.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-26-2019 09:46 AM
@stutz I've never heard of that kind of behavior. I have noticed that the exact behavior may depend on your particular 802.1x infrastructure. We recently changed from Juniper to Cisco with some 3rd party access control system (since my first reply on this thread). Even though the configurations on the computers has not changed, the user experience has changed. Under the Juniper setup, both Ethernet and Wifi just worked. Period. There was no prompting for certs or admin credentials once it was setup. Under this new system we have, if a computer is plugged into Ethernet at the time the user logs in, they will be prompted to pick a cert... they pick the correct cert.... then they are prompted again ad nauseum and it never seems to fully connect. If the user unplugs ethernet and waits a few seconds before plugging it back in, it will connect with no fuss. I've been telling users to wait until after they are logged in and at the desktop before connecting to ethernet.
I used to think 802.1x was 802.1x. This experience has opened my eyes to a whole new reality. Unfortunately I'm not knowledgeable enough about networking to fully understand what's at play. As long as you have your config profile set to AutoJoin, in theory, you should be OK. But I'm willing to bet there may be some settings on the 802.1x controller side that may need to be massaged to smooth things out.
The only other thing I can think of is to make sure your AD Cert payload is not set to prompt for credentials and do allow access to all applications. (checking the box for Automatic Renewal may also be a good idea. This was a recent addition but i've been handling it with a shell command)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-26-2019 10:39 AM
Thanks for the response. I checked the profile and those areas were already set to your suggestions. I'm thinking it has to do with our network settings as you also suggested because if I strip the Ethernet settings from the configuration profile I can connect to WiFi without having to enter admin credentials or select a device certificate and it works on the login screen.
Very strange.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-03-2019 11:50 AM
On your cert server, where the mac's go to get their machine certs, do you have a 'computer' template set up or a 'workstation' template? For whatever reason ours does not. This is a mainly pc shop, and I believe the pc's get their wifi certs through sccm/ad. Was going to create a 'computer' template (i can see the requests/denials on the CA server), but wasn't sure if that's how others have it set up. I'm going to work with our inf eng team to figure it out but wanted to ask in here as well.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-12-2023 06:57 AM
Hi Everyone,
I solved the 802.1x problem. You can contact me here to find out how to solve the problem.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-06-2023 03:00 PM
@husnudagidir How did you solve it?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-06-2023 02:59 PM
@husnudagidir How did you solve the problem?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-29-2023 02:43 PM
Hi,
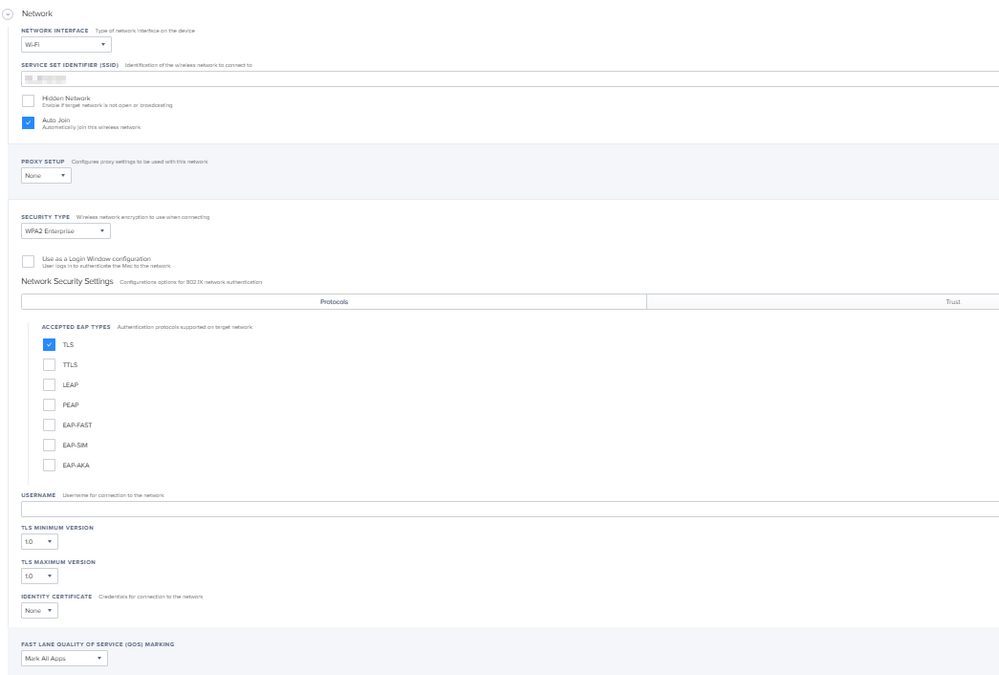
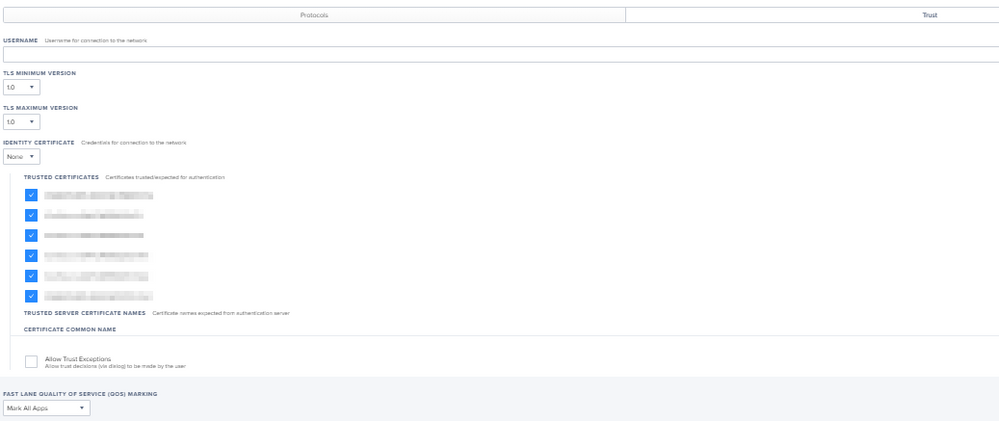
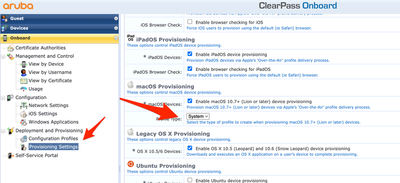
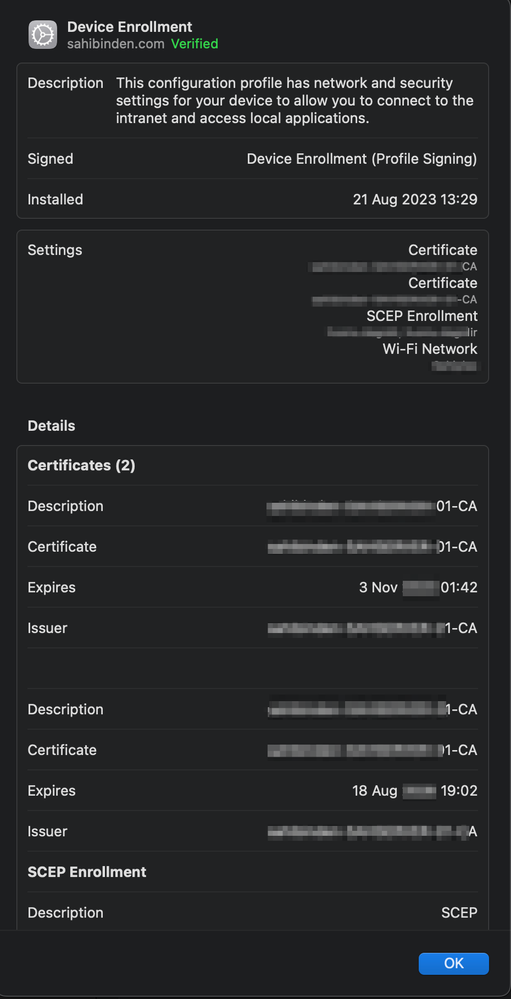
We use Aruba brand Access Points in our WIFI network. 802.1x is used to connect to the network through these products and we include users in the network by verifying with a certificate. At this stage, identity and certificate verification is done with an application called ClearPass. The ClearPass application also serves as an MDM server and SCEP server. When we connect to Access Points, the ClearPass application sends a profile file to users via a web interface. Actually the whole solution is contained in this profile file settings. We changed the part specified as "user" in the settings of this configuration profile file, sent to MacOS devices by the ClearPass application, to "system". Thus, as soon as our MacOS device was turned on, the user was able to connect to the network automatically without logging in. If the application you use is ClearPass, I support this article with screenshots. You can use the screenshot below. After making this change, you need to delete and reinstall the WIFI profile on the macOS device. After this step, the problem disappears.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-14-2023 03:37 PM
so you fixed it with a third party application... well that doesnt help most people.
for me, i can select the correct certificate, put in admin credentials and then it connects, every time. just cant get it working automatically yet.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-14-2023 11:49 PM
To connect automatically, you need to download a profile to your device. During the onboarding process, Clearpass should send you a configuration profile file and you should install it as well. Are you doing this? I am adding the contents of the profile file. By the way, Clearpass is supposed to work like a SCEP server. It would be easier to do this with a company from which you get consultancy regarding Aruba. In the posts I published above, I also explained what to do for the profile file.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-15-2023 08:16 AM
Need third party software "clearpass" so your advice is worthless sadly unless you have that.
No use posting really when you solved your problem with money, not skills. its applicable to no one else.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-12-2023 01:37 PM
Hi,
I proposed a solution within the scope of the benefits and supports of a product in the environment I work in. I did not purchase a third party product to solve this problem. I saw problems with the products in the environment I currently work in and wanted to help people using similar products. Additionally, Aruba's Clearpass product is an extremely powerful and useful product. If you really care about information security and want to create a strong security environment, you need to purchase some products. For some this may be difficult. You are only as strong and secure as the security investment you make. Jamf Pro is a product we use safely in this context :)