- Jamf Nation Community
- Products
- Jamf Pro
- Re: AD CS integration with Jamf Pro
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
AD CS integration with Jamf Pro
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on
08-05-2018
11:51 PM
- last edited on
03-04-2025
07:41 AM
by
![]() kh-richa_mig
kh-richa_mig
Hi all,
Can I please confirm that by integrating my AD CA to Jamf Pro, does it mean that i can push AD Cert to computers via Config Profile eventhough the computer doesnt have connection to the domain?
We are about to deploy .1x WiFi Profile to use AD cert for EAP-TLS and do have a concern with computers that are not on the network to receive the AD machine Cert.
Thanks
Update
Just to sum it up for other people's reference.
On your Certificate Authority
1. Right click Certificate Template - Manage Template
2. Select Workstation Authentication and Right Click - Duplicate Template
3. Type in the Template Display Name and Template Name
4. Click Security tab - Add Proxy Server computer and set Read, Enroll and Autoenroll permissions (as advised by Jamf)
5. Click Subject Name - Click "Supply in the request" option
6. Close Certificate Template Console - Right Click Certificate Template - New - Certificate Template to Issue - Select your Certificate Template
On your Jamf Config Profile
1. Add Certificate Payload
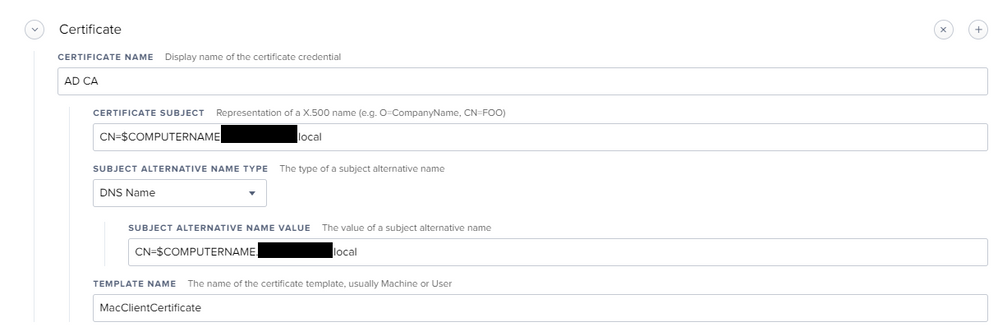
2. Give it a name, and set your Certificate Subject to "CN=$COMPUTERNAME.my.domain"
3. As a particular application in my environment requires Subject Alternative Name - i set it to DNS name with a value of "CN=$COMPUTERNAME.my.domain"
4. Template Name - as the one you created with the process above.
5. Depending on your CA structure, dont forget to add your intermediate and root certificate payloads so the certificate chain is valid.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-06-2018 09:00 AM
Yes, the setup for this is pretty lame. I can help if you need any. I have tested on iOS and Mac and it works great.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-06-2018 12:44 PM
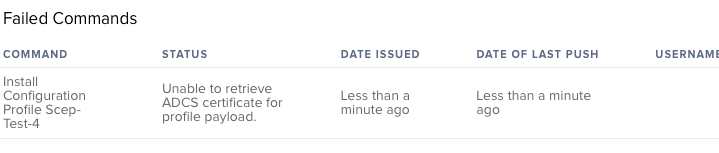
@kericson I'd appreciate your help, if you don't mind. I installed the proxy OK and added it to PKI. I got the device profile setup with the cert payload, but the profile fails to install. In the server logs, I see repeated entries of "[WARN ] [ina-exec-43] [Credentials ] - We don't want to return an X509 Cert from a PKCS12 data blob"
In the management commands view of the device, I see "Unable to retrieve ADCS certificate for profile payload."
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-06-2018 01:20 PM
I'm working on getting some screenshots together for you.
Quick steps:
1. Copy a workstation template in your root ca and make sure it set to supply in the request
2. Install the ADCS connector make sure to use the Public DNS name
3. Add the ADCS connector inside of JAMF
4. Create a profile with these certs Root CA, Issuing CA, and the ADCS payload
5. For the Subject, I did $username@mydomain.com
Maybe tomorrow I can add the screenshots.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-06-2018 01:48 PM
@kerickson thanks for the quick response.
1. I'm not sure how the CA is setup, but it is generating certs for devices managed by AirWatch, so I copied the template and server name from the airwatch settings. I don't have direct access to the CA.
2. ADCS connector was installed using public DNS name
3. ADCS connector was added inside of Jamf
4. I added all 3 payloads you suggested
5. For subject, I did CN=$USERNAME$SERIALNUMBER as that is what we have working in AirWatch today.
Tested, and still failed. I noticed a few things that may be "non-standard" with my environment.
First, the AD CS connector is behind an F5 load balancer. Its the F5 that hosts the server certificate, and it uses a wildcard cert for all the websites behind it. If I visit the AD CS connector URL from a device, I see the wildcard cert used for the site, not the cert generated during install. I tested using the server cert generated by the AD CS connector install and I tested with the wildcard cert but both failed.
Second, I noticed AirWatch is configured to supply user name and pw for a service account when submitting the cert requests, but Jamf doesn't seem to have the option. I checked the cert template and noticed that only specific accounts have rights to enroll with it. I asked our PKI team to grant the AD CS Connector server system account the rights to enroll that template and will test again once they set it up.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-06-2018 05:05 PM
2. Install the ADCS connector make sure to use the Public DNS name
Pardon my ignorance, are you referring to the public-facing DNS name of the Jamf Pro server?
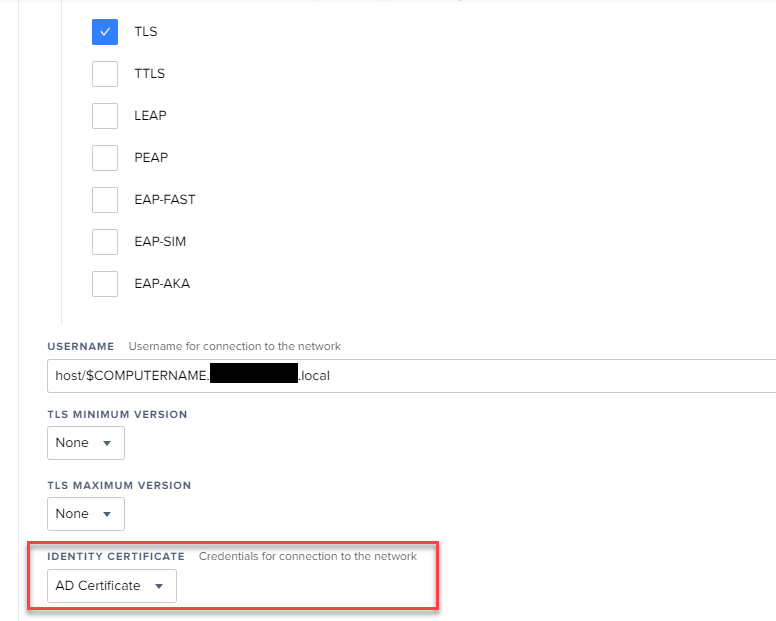
Just to confirm, so my Wifi .1x profile needs to have AD CS, network, and AD certificate payload?
The reason i asked is that at the moment I have deployed machine cert by running a script to a mobileconfig. However, in order for .1x WiFi profile to work, i need to specify on the profile which AD cert to be used for authentication.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-06-2018 07:09 PM
No need for the AD cert payload. You use the ADCS as a issuing cert in the cert payload. The public DNS name is for the server with the ADCS connector installed on. I have JAMF Pro in the cloud so I have a on prem server where the ADCS connector is installed on with a public dns name.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-07-2018 06:13 AM
@khey See if this helps ADCS Guide
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-13-2018 07:19 AM
@kericson thanks for sharing that ADCS guide. It looks like you granted domain computers permission to the certificate template, do you know what happens if the Macs are not joined to the domain?
I am using NoMAD to keep computers unbound to the domain. I was hoping we could create an Active Directory service account that we grant permission to the certificate template, but I don't see a place in JAMF to enter the service account credentials.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-13-2018 07:25 AM
The permissions are for the ADCS server to request the cert, not the computer. You can set the permissions just for the ADCS server I just did domain computers.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-14-2018 07:52 AM
For some reason I cant seem to get this to work. My config profile sits as pending..not sure why.....
I too was hoping to have a User Certificate downloaded, but I can also use a computer certificate. not sure what has to happen though if my Macs are not bound to active directory.
anyone know if there are any logs to look at to help determine why its pending.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-14-2018 09:37 AM
made a few changes and got the same as above..
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-14-2018 11:39 PM
Hi guys,
Am using $COMPUTERNAME in the certificate payload hoping that JAMF Pro will actually query the computername and then pass on the information to the Proxy and then the CA to issue the machine certificate. It seems that the certificate that is generated is using the proxy computer name instead of the workstation.
Any pointer?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-15-2018 11:53 PM
Hi @jimderlatka,
I would check the following:
- You can connect to your proxy over HTTPS 443 from your Jamf Pro (use telnet to test).
- You proxy server can connect to your AD CA? check if the required ports are opened Jamf AD CP
- Check the Security of your certificate template, make sure the Domain User or Domain Computer have read and enroll access.
- Is your test machine joined to the domain and kerberos is active? if not, are you using NoMAD or EnterpriseConnect to have the kerberos active?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-22-2018 05:37 AM
sorry just getting back from vacation
non-domain joined... using enterprise connect.
I did have a port blocked which is corrected now, and I am seeing a cert shuttled to the MacBook now.. but its not formed correctly. the details section with common name and email address basically have the server name that the AD CS service is running on... not sure why yet.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-22-2018 08:11 AM
@jimderlatka I believe that means your cert template requires an AD machine account to be present in AD. Ask your CA admins to remove that requirement, or create a new template that doesn't include that. Sorry I don't know what the name of the checkbox(es) would be since I also have someone else handle that stuff. But I know I have two cert templates that I've used, one requires the machine account, the other doesn't. When I use the former, it also uses the ADCS server name.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-22-2018 09:52 AM
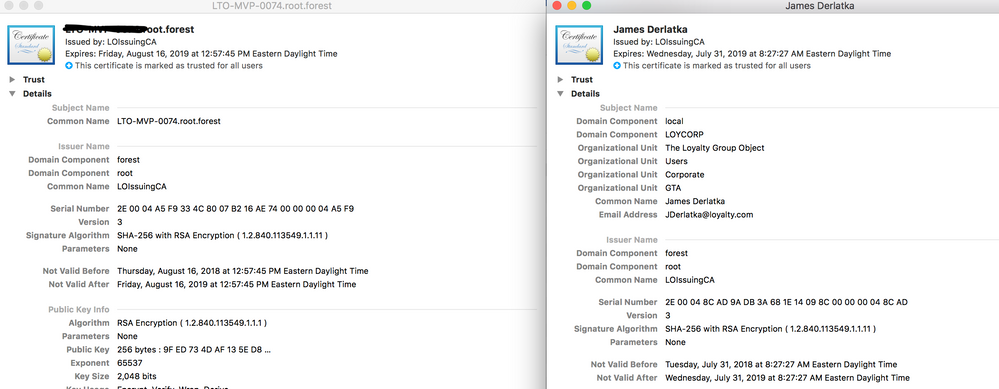
I think I finally got everything I need... I was able to issue the certificate now just like it looks in windows
had to add this to my subject line
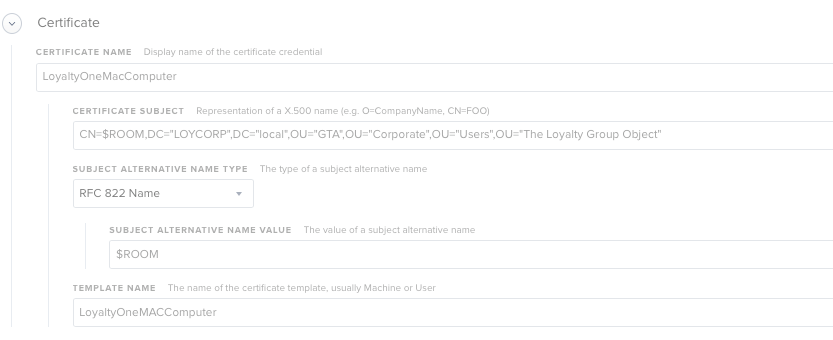
CN=$FULLNAME,EMAIL=$USERNAME@Loyalty.com,DC="LOYCORP",DC="local",OU="GTA",OU="Corporate",OU="Users",OU="The Loyalty Group Object"
This basically configured all the details part of the certificate so it looks pretty now.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-23-2018 08:52 PM
@jimderlatka tried your fix for my machine based certificate and its still showing the name of the proxy server.....
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-24-2018 04:50 AM
Make sure your template is a computer template not a user template. In my testing user template didn’t work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-24-2018 08:54 AM
You also need to make sure you're not using a template that requires a computer account in AD.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-26-2018 10:57 PM
@jimderlatka i did use $COMPUTERNAME instead of %USERNAME on the payload.
@patgmac could find that option in my certificate template. Do you mean in Security Settings? to allow everyone read and enroll access?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-27-2018 08:49 AM
@khey I'm not sure honestly. We have 2 templates that I've used here, one worked with ADCS, the other didn't. When I asked my cert guy what the difference was, he said the one that wasn't working required an AD machine object.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-27-2018 10:33 PM
@patgmac I think its the Certificate Template Subject Name option "Supply in the request" instead of "Build from this Active Directory Information"
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-28-2018 05:33 AM
Ok. tried everything.. I can get a Computer Template to deploy no problem, but for connecting to wifi eap tls the certificate is missing an nt principal name... I believe I need a user certificate template....
but I cant seem to get a user certificate to work at all....... Has anyone had any luck getting a user certificate template to install......I've tried everything and nothing seems to work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-28-2018 08:17 AM
@jimderlatka Did you try using your variable like computername@yourdomain.com? This will create a cert with a UPN name. My example is $username@acemfg.com
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-28-2018 08:20 AM
Has anyone tried using this solution to deliver user based (Login Keychain) certs with no user intervention?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-28-2018 08:27 AM
@jimderlatka I had to change my LDAP mapping to store LDAP property "UserPrincipalName" as the $ROOM variable. Then in the certificate payload, I set subject to CN=$ROOM. This puts the UPN in the certificate subject and allows my NPS/RADIUS to look-up and authenticate the user for wifi connection.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-28-2018 09:43 AM
@ocla&&09 Yes, I have the same profile settings in a user-based profile in addition to the device-level profile so that a cert is put into the login and system keychains. This way, if the user has to manually select the wifi network, it doesn't have to prompt to create the identity in the login keychain (manually selecting the network will not use the existing system identity).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-28-2018 08:50 PM
@jimderlatka I managed to get it working with Computer cert.
This is what i have for my Certificate Subject Name and SAN "CN=$COMPUTERNAME.domain"
Do you include your Root and Intermediate certs in your Certificate payload? you dont have to do this on the same profile but the certificate chain has to be valid. Other thing is whether you have selected DNS Name as the Subject Alternate Name?
What are you using as the radius? Windows NPS, ClearPass etc? check the error log there?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-29-2018 08:15 AM
AD CS can't do user certs yet:
https://www.jamf.com/jamf-nation/feature-requests/7633/add-support-for-user-certificates-in-the-ad-c...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-29-2018 03:51 PM
For anyone having difficulties with the setup of AD CS proxy, please review this YouTube video: ADCS Install. Daniel does a great job of pointing out some common gotchas during the install.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-31-2018 05:35 AM
so I've finally got mine to work 100% the way I need it to... I'm using a computer cert that is fully populated with all the details as in our user certs. This deploys properly with adcs. We have our windows 10 computers authenticating using a computer certificate and our Macs with a user certificate....
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-10-2018 11:21 AM
Any thoughts on how to troubleshoot connectivity to the PKI servers? (Ensuring that the AD CS Connector server can find the certificate templates from AD CS)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-19-2018 09:38 AM
Does anyone know if this works with computer certificates and Mac's that are not bound to an AD domain?
I was able to get the AD CS Connector setup and pushed certificates to my laptops and it works fine if they are bound to AD but when I remove them from AD i get an error in NPS "Reason 8 - The specified user account does not exist". I have tried everything i can think of but i cannot seem to get it to work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-19-2018 10:12 AM
yes to computer certificates and yes to not bound to AD Domain.... that being said if I configure the cert with all the details for a user type of cert it works, but when I try to authenticate to my radius as a computer named cert it does not... I have a case with Microsoft open right now that I'm going to get some movement on tomorrow with the tech....
right now I'm authenticating with a Computer/User Certificate Identity for Radius and it is working perfecting.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-20-2018 12:28 PM
When i try to make a computer certificate and set the Subject as CN=$USERNAME (username is my email which is the same as my UPN) and the SAN to $COMPUTERNAME.domain.com I get an error in NPS - Reason code 16 "Authentication failed due to a user credentials mismatch. Either the user name provided so not map to an existing user account or the password was incorrect". If i make a computer certificate and use $COMPUTERNAME.domain.com for both the Subject and SAN i get the error code 8 i mentioned above.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-21-2018 09:51 AM
take a look at my cert setup.... these fields match my user based certificate...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-21-2018 01:55 PM
Thanks for the assistance I was able to get it work but there are a few things i am not sure on.
If you are taking a Computer template and populating it with user attributes ($ROOM in your case) aren't you just making a user certificate since the only difference between a Computer and User template is the default Key Usage ( Extensions). When you populate it with computer details ($COMPUTERNAME.domain.com) you are making a computer cert and you will not be able to authenticate because it is not binded to a domain (as far as i can tell you have to be connected to a domain for a machine certificate to work).
From my testing it seems like OSX does not requires a computer certificate for pre-logon authentication and seems to work fine with a user certificate? On Windows i think it had to be a machine certificate.
I got mine to work with out a Subject Alternate Name which seems to contradict the NPS requirements (https://docs.microsoft.com/en-us/windows-server/networking/technologies/nps/nps-manage-cert-requirements) so im not really sure how is working but it is.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-21-2018 11:14 AM
Hi Guys,
I've followed these steps which are pretty much identical to this youtube video, https://www.youtube.com/watch?v=oRkpkN1Z3aI. But I am still unable to get this to work. I keep getting "Unable to retrieve ADCS certificate from certificate payload" errors. I've made sure all the information is correct, double checked the ports are open but still can't get this to work. Any suggestions?
Thanks so much
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-26-2018 05:50 AM
The Server where the ADCS connector is installed I suppose must been registered in public DNS , as Jamf through Internet will reach out for it - or is it something i miss?