We've started to deploy Crowdstrike on Apple Silicon machines and are running into issues with the kernel extensions due to the machine security policy being set to "Full Security" by default. Right now our end-users are seeing a "system extension blocked" pop-up every 30 minutes.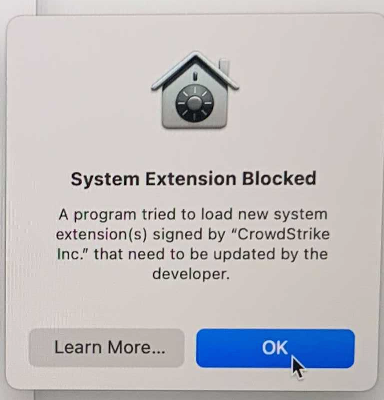
Apple's support page says if you have Automated Device Enrollment with an MDM then it can be automatically authorized upon contacting your MDM vendor. I can’t find any Jamf support articles that actually explain how to make this change.
How do we do this?
We're going to have a handful of existing machines where we'll need to force them into recoveryOS mode to change it manually and then I want ALL new machines going forward to have this handled automatically via the way Apple claims it can.



