- Jamf Nation Community
- Products
- Jamf Pro
- Re: Addressing macOS High Sierra Vulnerability
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Addressing macOS High Sierra Vulnerability
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on
11-29-2017
10:32 AM
- last edited on
03-04-2025
07:50 AM
by
![]() kh-richa_mig
kh-richa_mig
Apple has released a Security Update for High Sierra (HT208315), and Jamf recommends anyone with High Sierra run it as soon as possible. For a full description of the security update visit: https://support.apple.com/en-us/HT208315.
This particular security vulnerability allows a user or attacker to gain access to a Mac with default settings sans a password. In addition, this issue also allows standard users to gain elevated privileges in System Preferences, access via a script, and most importantly at the Login Window.
Why does this matter? All Mac devices have what’s known as a root account, or a super-user account that has access to the internals of any Unix or BSD-based operating system. The issue is made possible by the fact that the root account has a blank password and can login prior to the update being run. This issue requires physical access to a device or remote access via a tool like Apple Remote Desktop.
- In general, the root account should not be enabled unless it’s being used. To disable this manually, use https://support.apple.com/en-us/HT204012.
- There is a Jamf Nation community discussion addressing this, available at: https://www.jamf.com/jamf-nation/discussions/26290/vulnerability-10-13-root
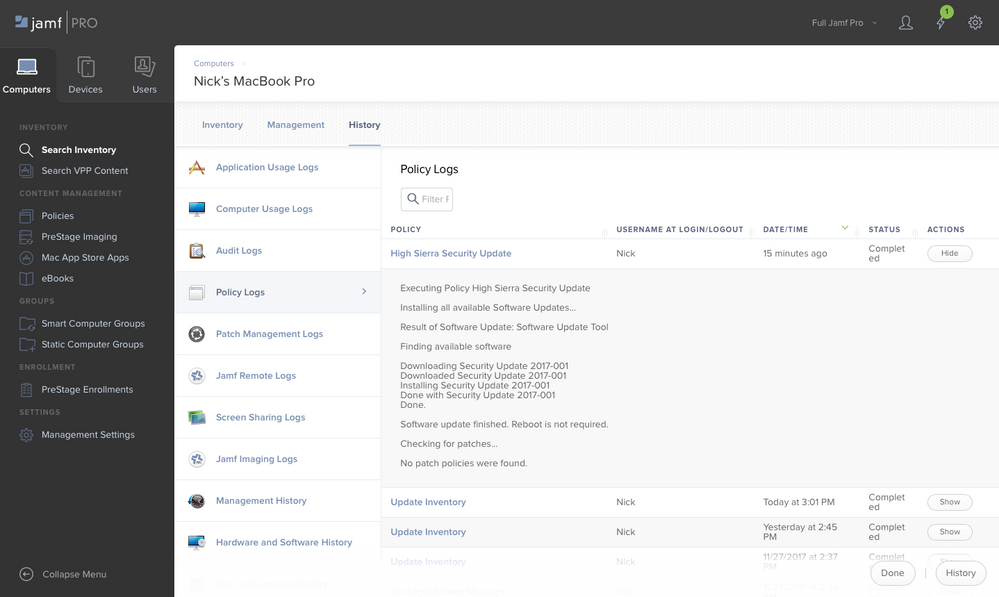
Screenshot of Jamf Pro with patch applied.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-29-2017 10:57 AM
Thanks Jake!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-29-2017 11:00 AM
Are you doing anything to force this update?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-29-2017 11:04 AM
From apple's official comments spreading, it also sounds like they're going to be forcing this update.
When our security engineers became aware of the issue Tuesday afternoon, we immediately began working on an update that closes the security hole. This morning, as of 8 a.m., the update is available for download, and starting later today it will be automatically installed on all systems running the latest version (10.13.1) of macOS High Sierra.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-29-2017 06:12 PM
Also of note, if you see issues mounting SMB shares after applying this gem, you may need to run this fix:
Repair file sharing after Security Update 2017-001 for macOS High Sierra 10.13.1
sudo /usr/libexec/configureLocalKDC- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-29-2017 06:32 PM
Just discovered this as well:
After applying the patch and sudo /usr/libexec/configureLocalKDC command, I am unable to create a new user from admin acct. This is on two different Macs running 10.13.1. Have to check what else seems busted now...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-29-2017 06:40 PM
Awesome post @jake, thanks!
https://donmontalvo.com
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-01-2017 09:02 AM
"starting later today it will be automatically installed on all systems running the latest version (10.13.1) of macOS High Sierra."
does this mean apple will automatically apply it or does the end user have to install updates?
Is it easier in JAMF to apply the patch or just disable root or change root password?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-01-2017 09:24 AM
Yep it means that apple forced it upon your machines.. and then re-force dit when they had a 2nd patch to fix an error on the first patch. It also includes 10.13 machines.
Beta's are still unpatched... which goes without saying don't run a beta in production ;)
at this point i don't feel you'd have to do anything in jamf
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-01-2017 09:34 AM
Seems the beta feeds are down anyway. So much for testing provisioning today!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-01-2017 03:24 PM
Not sure build number is the right way to go..Apple article HT208315 says to use "project version" of opendirectoryd (what /usr/libexec/opendirectoryd), so we set up an EA to pull the version and go from there:
#!/bin/sh
odVersion=$( what /usr/libexec/opendirectoryd | awk '{ print $2 }' | cut -f2 -d "-" | tr -d "
" )
echo "<result>${odVersion}</result>"https://donmontalvo.com
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-05-2017 04:19 PM
This EA will also work as a very temporary solution until Apple releases a new version. The above EA from @donmontalvo is much better. I was just playing around with this EA and it more or less does the job.
#!/bin/sh
# If Security Update 2017-001 was installed successfully, you will see one of these project version numbers:
# opendirectoryd-483.1.5 on macOS High Sierra 10.13
# opendirectoryd-483.20.7 on macOS High Sierra 10.13.1
# https://support.apple.com/en-us/HT208315
# Get the version
version=$(what /usr/libexec/opendirectoryd | grep PROJECT | cut -d: -f3)
if [[ "$version" == opendirectoryd-483.20.7 ]] || [[ opendirectoryd-483.1.5 ]]
then
echo "<result>Compliant</result>"
else
echo "<result>Not Compliant</result>"
fi- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-05-2018 09:35 AM
Sorry for my ignorance, but where do I go to find the results?
Also- how do I customize this EA to find out if Security Update 2017-002 has been updated on Sierra OS's? We currently don't have users using High Sierra yet.
Ideally, I would like to be able to force this update on everybody.
https://support.apple.com/en-us/HT208331
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-05-2018 10:19 AM
A
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-05-2018 10:58 AM
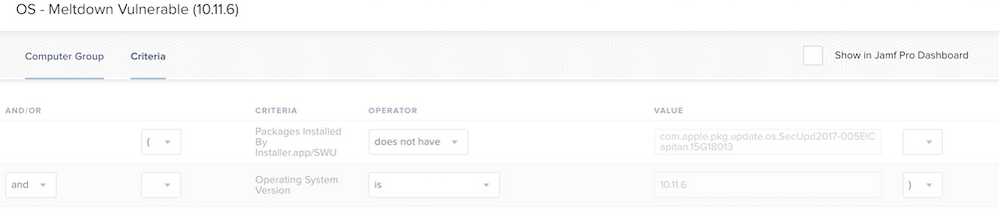
@ryan.er - I saw this on Slack today regarding this.
Not my setup, but one that was shown as being used.
does not have com.apple.pkg.update.os.SecUpd2017-002Sierra.16G1114 and/or does not have com.apple.pkg.update.os.SecUpd2017-005ElCapitan.15G18013