- Jamf Nation Community
- Products
- Jamf Pro
- Re: Adobe PCD Permissions
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Adobe PCD Permissions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-28-2015 07:40 AM
Hello all,
Just have a quick question about the Adobe PCD folder in CS installations:
Has anyone found a way to make this folder not writable to users, but still allow Adobe products to open without error? Unfortunately, the students somehow found this folder and it is in '/S/L/AppSupp/Adobe/Adobe PCD' with full read/write to be able to work correctly. I have tried all sorts of permission variations with no success. Either the user cannot write and Adobe products will fail to open or the user can write and they can open. This link says that read only will work as long as system has read write, that has proven to be very incorrect in my test environment.
Perhaps I am going about this the wrong way though. I was thinking of making it execute a permissions script on each opening of Adobe and put it back to no access after the program successfully opens, but I have no idea if it continuously checks in with that PCD folder.
If anyone has any ideas or thoughts on the matter, please let me know. This folder allows them to copy in games and other unapproved apps, and as you can imagine that is undesirable.
Thank you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-29-2015 11:35 AM
@GSquared are the "wanted" contents of the folder static?
If so, maybe just run a script periodically that empties all but the "wanted" content from the folder?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-04-2015 05:54 AM
@bentoms the contents are a cache file, and also a randomly generated temp cache file that gets generated and deleted on open of Adobe apps.
Perhaps since that file gets deleted and only the main cache file stays, that method will work ok. Thanks for the idea, I'll give it a go!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-25-2015 12:16 PM
@GSquared We are working through a similar issue right now. For some reason we have to give full permissions to the /Lib/AppSupp/Adobe for it to work at all, we get the error 16 message otherwise.
Were you able to figure anything out with keeping these folders locked down? We have students that have figured it out at this point and are using it to run unauthorized applications.
We were thinking about laying down a clean copy of the Adobe folder in a hidden folder and then copying it back to replace one that could potentially have something it's not supposed to. (using a daemon)
Any ideas are appreciated.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-25-2015 12:25 PM
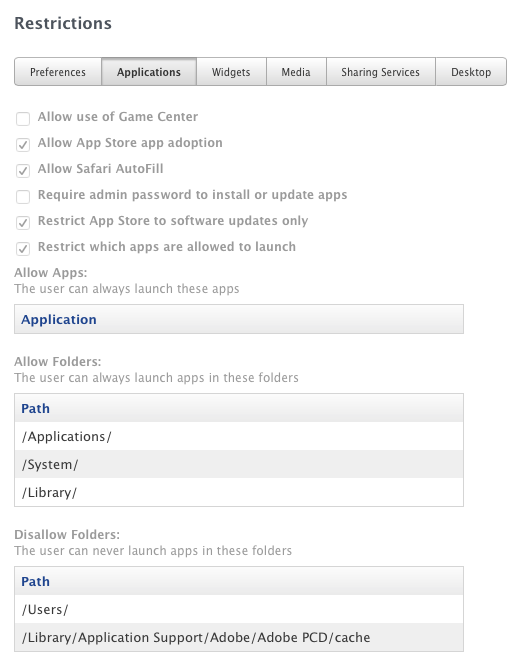
@brushj We have done it successfully I believe. I went through and made a whole new security policy with a Configuration Profile for this year swapping over from MCX. Inside this profile I have in the Application Restrictions specific folders that are black/whitelisted. I put this Adobe PCD folder inside the blacklist and it has not affected the opening of the Adobe apps at all thankfully, but still works in blocking the apps that the students copied to this folder. The thing with this is that it specifically blocks apps from running in there and what Adobe does in that folder is just create a new cache file when the Adobe apps run, so it doesn't affect it.
My question is how in the world did these students come across this random folder? There must be something online that they found.
If you need any assistance with this just @ mention me again and I'll try to help you out!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-29-2015 05:54 AM
@GSquared Thanks for the confirmation, just wanted to let you know that we tested this out in our environment and have been successful as well. Thanks for the idea.