- Jamf Nation Community
- Products
- Jamf Pro
- Re: Big Sur M1 Mac + Filevailt 2 - Admin user = Bi...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Big Sur M1 Mac + Filevailt 2 - Admin user = Big problems
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-02-2020 11:42 AM
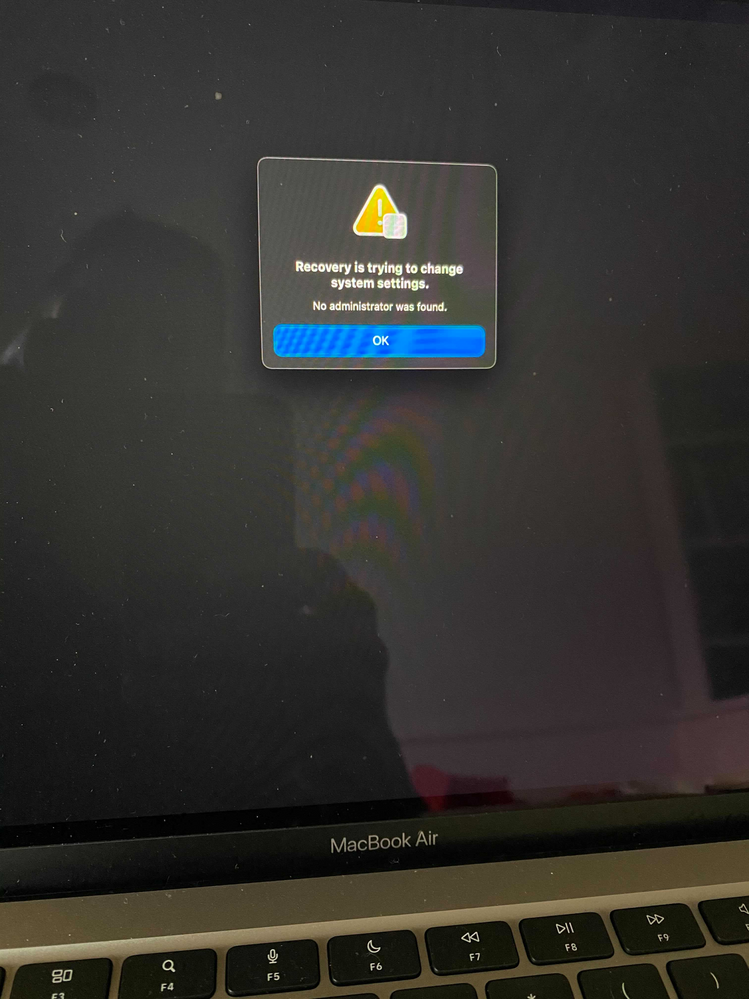
After configuring our first M1 machine we ended up with the attached error. "Recovery is trying to change system setting. No Administrator was found."
This happened after a reboot in which some system and kernel extensions were installed by policy and approved via config profile. Our machines have local admin accounts, but only the user account is FV2 capable and they are not an admin. That appears to be the crux of the issue.
Sadly I can't troubleshoot further because once you get this error, the only option is to erase/restore. And I was getting this error: https://support.apple.com/en-us/HT211983
and while I was able to restore it via the configurator approach yesterday, I cannot today because the boot key command will no longer get the machine into revive mode and recognized by configurator. Apple support is stumped and is just sending me a new machine... they believe this one is just bricked. I restored it probably 4-5 times yesterday. today it's a paperweight that can't install an os.
So... has anyone else seen this "No Admin" error? Any solutions I should attempt once I get my replacement M! machine? Need to look into reworking our workflow so our admin account is also a FV2 user?
Mostly I want to direct attention to both this "no admin" error's existence and just how absurdly easy it is to brick these M1s apparently. Tread carefully, but also be aware Apple is swapping these out pretty readily if you do.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-01-2021 02:11 AM
@matthias.bretz Yes, that's what I'm talking about. If you got any packages that installs kext extensions then you will get these prompts. And since the package contains a kext it will fail.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-22-2021 12:06 PM
I have gotten the same error on only 4 of the 100 new M1s that we got. They were all onboarded the same way. Hopefully it doesn't happen to all 100 because we are starting to check them out to our students today.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-15-2021 07:41 AM
@Tophernad Are you aware of the minor/patch versions of macOS 11 the failed Macs were on? I'm not seeing this issue on 11.2.3 and it would be interesting to see if Apple have fixed this issue in the more recent versions of macOS.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-03-2021 08:40 AM
This is ridiculous that this is still happening. I've got a Securetoken enabled account, which is an administrator (the only administrator account on the machine) and when trying to re-install the OS, get the recovery error message. And I'm trying to do this, following Apple's recommendation, since I have had 2 users report that after upgrading to 11.4, their machines freeze at progress bar after entering their password. Only thing they were able to do is hard shut down the machine, and then they were able to log in.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-23-2021 11:11 AM
I was able to overcome this error by disabling Filevault disk encryption and booting to recovery. I then adjust the security to reduced security and rebooted to OS. Then turned back on disk encryption.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-26-2022 10:55 AM
Hi,
Sorry I know it's been almost a year since this thread was active but does anyone know if this issue was resolved with any update to Mac OS?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-26-2022 11:01 AM
Not as of late, but here is the solution that I am using to work out the error:
User received an M1 from Apple with macOS 12 preloaded. To prep for CheckPoint E85.30 that is macOS12 supported, I did the following:
ACTIONS:
- Booting to recovery produced "no admin error"; To bypass the "no admin error", we booted back to OS and turned off Filevault disk encryption. From terminal:
- su $ADMIN
#(or other filevault2 user found under Jamf - Computers - Computername - Disk Encryption) - sudo fdesetup disable
- su $ADMIN
- sudo sysadminctl -adminUser $ADMIN -adminPassword - -secureTokenOn $USER -password -
#(where $ADMIN = filevault2 user & $USER = username)
- sudo sysadminctl -adminUser $ADMIN -adminPassword - -secureTokenOn $USER -password -
- sudo fdesetup enable
- sudo diskutil apfs updatePreboot /
- Added admin users as secure token users and re-enabled disk encryption using command above
sudo sysadminctl -adminUser $ADMIN -adminPassword - -secureTokenOn $OTHER -password - - Booted to recovery and reduced security to allow 3rd party extension
- Allow user management of kernel extensions from identified developers
- Allow remote management of kernel extensions and automatic software updates