I'm out of time and ideas. If you have any input regarding HOW I can achieve the end goal, please chime in! Beers for everyone!
Goal: During enrollment of computers we want the end user to be able to log into the machine with their AD credentials after they complete the setup assistant.
Issue: The computer fails to bind to AD; therefore leaving the end user unable to log into the computer. We skip the "create local account" in Prestage.
Failure: The failure occurs with the Configuration Profile to bind to AD. I receive an error message: The server ‘DIRECTORYSERVER.ABC.org’ either couldn’t be found, or was not responding.
Workaround: Deleting the failed command to bind to AD, excluding the machine from the scope of the profile, sending a blank push, then rescoping the machine to the bind to AD profile successfully delivers the config profile. This is NOT an ideal workflow and this process can't be babysat.
Components to achieve this goal:
Environment: Jamf Pro v10.5
Enrollment Method: DEP/Prestage
Config Profiles: Bind to AD
Scope: All Managed Computers
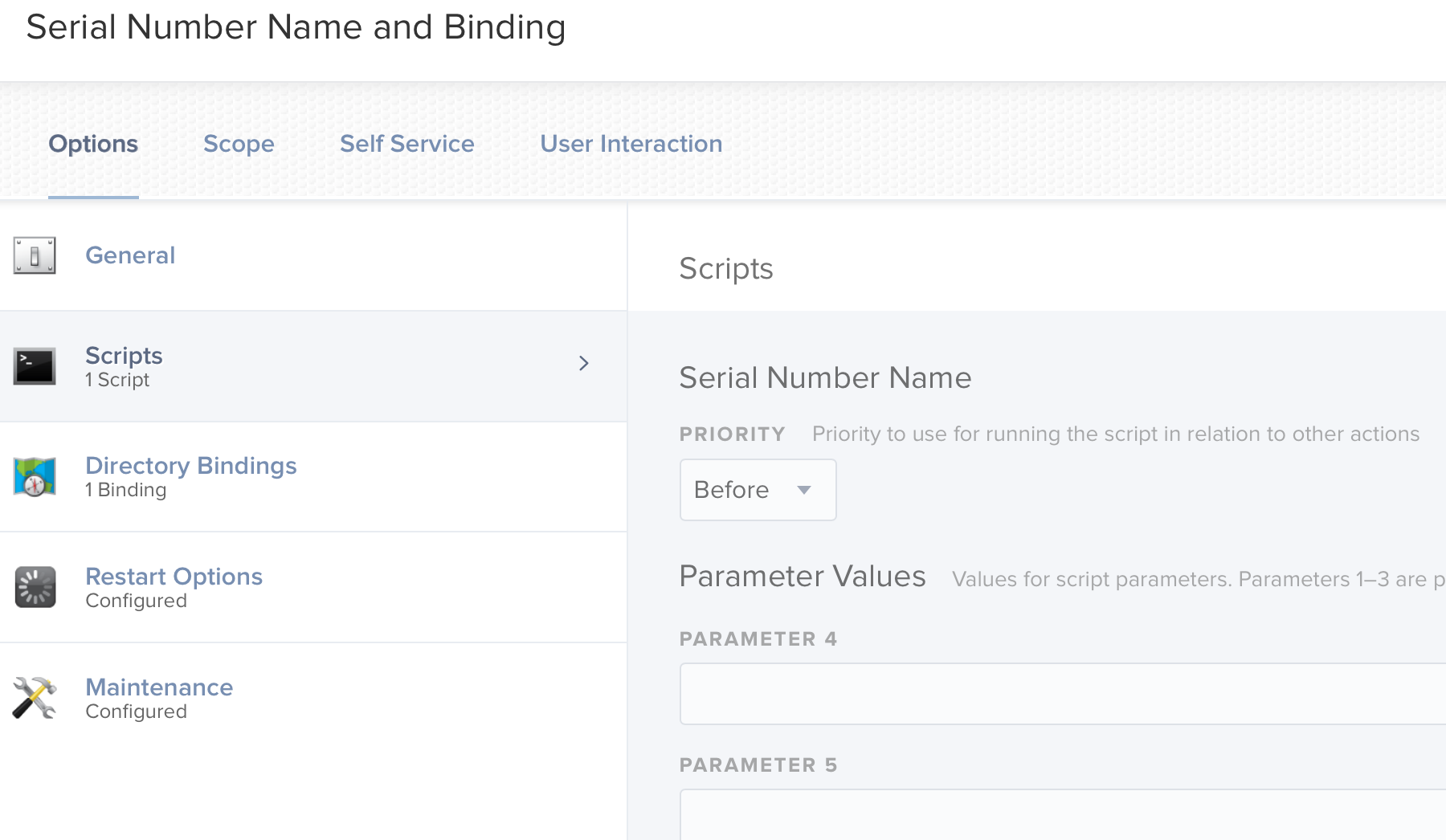
Policies: Computer Name Change Script:
Trigger: Once per computer after Enrollment is Complete
#!/usr/bin/env bash
# Get the Serial Number of the Machine
sn=$(system_profiler SPHardwareDataType | awk '/Serial/ {print $4}')
# Set the ComputerName, HostName and LocalHostName
scutil --set ComputerName $sn
scutil --set HostName $sn
scutil --set LocalHostName $snI've tried using the IP address and the host name of the directory server and they both initially fail.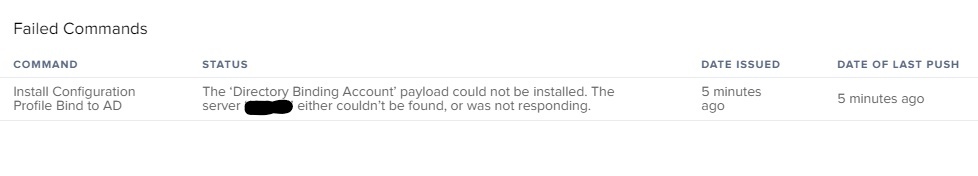
Theory: Is it possible that the machine is trying to bind to AD before the name change? There was a thought to create a smartgroup based on a name change and then scope the bind to AD profile to that smartgroup. However, I don't fully trust smartgroups.