- Jamf Nation Community
- Products
- Jamf Pro
- Re: Bitdefender - anyone using it?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Bitdefender - anyone using it?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-13-2017 05:13 AM
Is anyone out there using Bitdefender (BD) for AV within their environment? I'm about to trial it and was wondering if anyone had any experience setting it up within their environment.
I don't see a lot of discussion about BD but I see a lot of good reviews online and their client seems to be pretty minimal on using system resources. Seems like there is a good way to deploy this from their web interface but was wondering if people have been able to deploy packages within JAMF?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-13-2017 06:52 AM
we're using it..is there much more I can say at the moment. unfortunately not, hopefully soon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-13-2017 10:07 AM
we're using it..is there much more I can say at the moment. unfortunately not, hopefully soon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-14-2018 03:04 PM
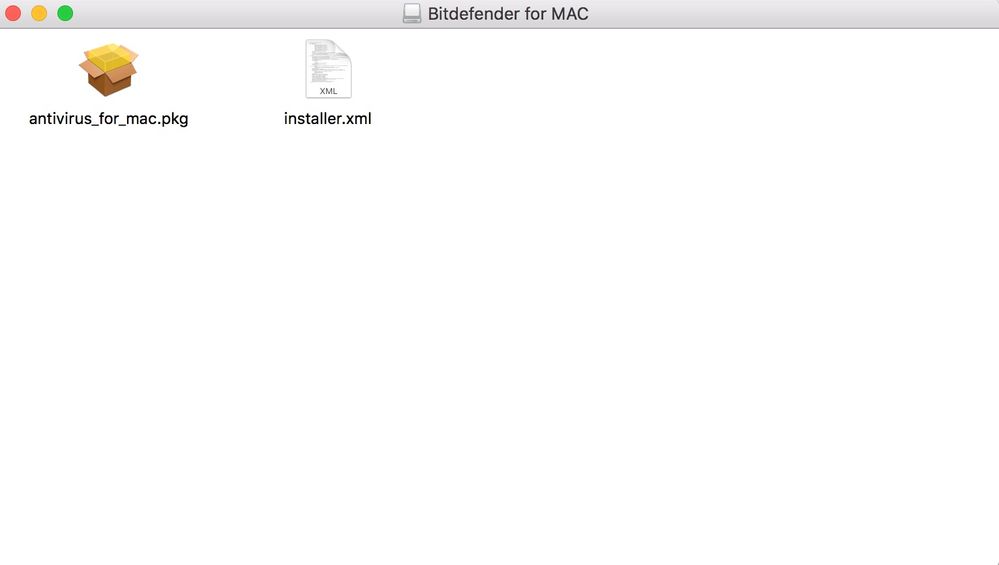
We're also using it for our fleet of Macbooks. It's ok, the Cloud console takes a bit of time to get accustomed to. Currently have an odd problem of some computers unmanaged by BitDefender's Cloud Console. BitDefender Support examined logs of affected computers and stated the PKG file needs to be in the same directory as installer.xml.
Anyone have any advice on which Composer method should be used to create this package.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-18-2018 03:14 AM
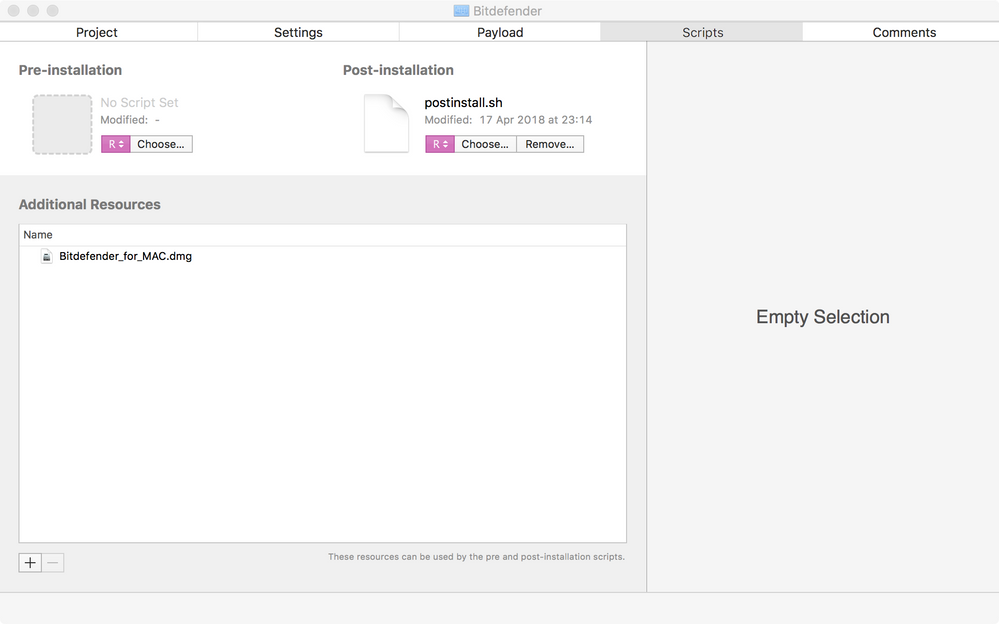
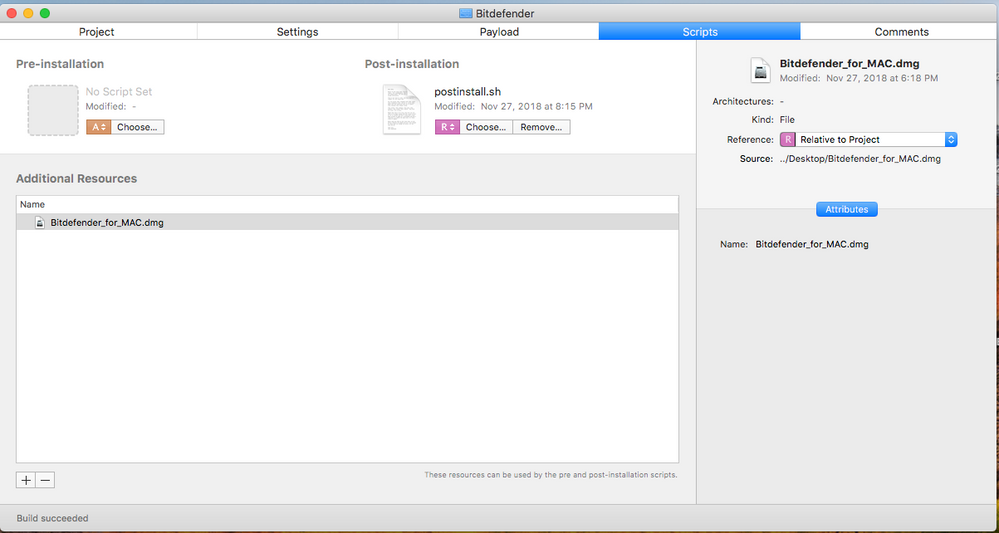
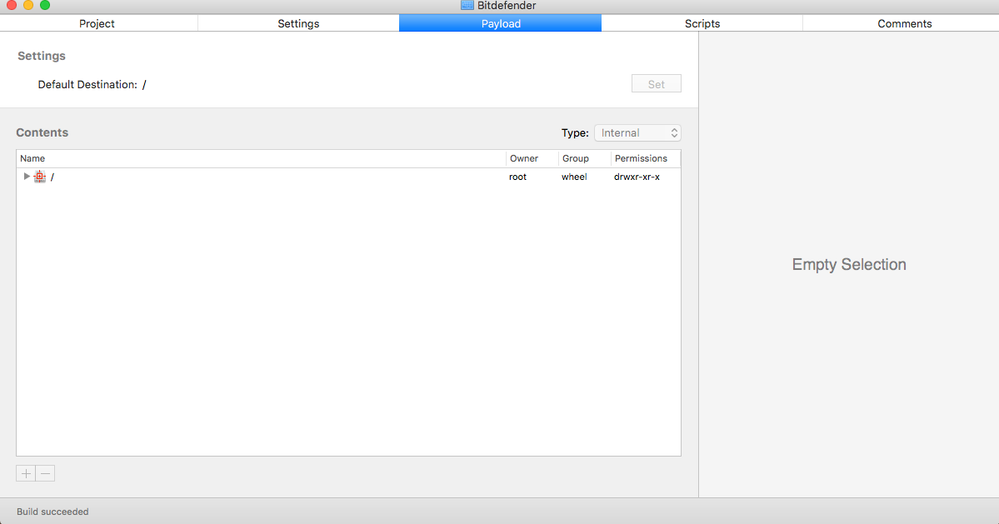
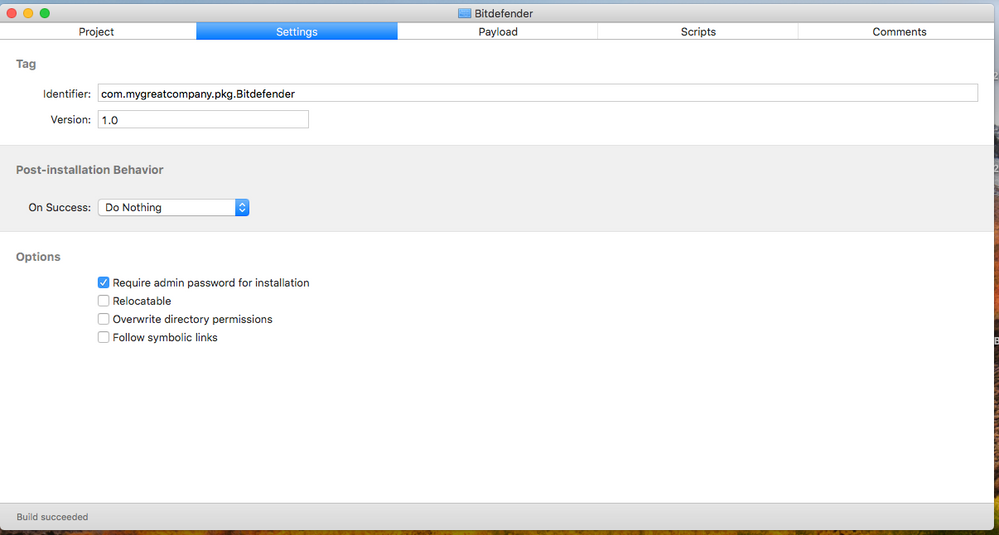
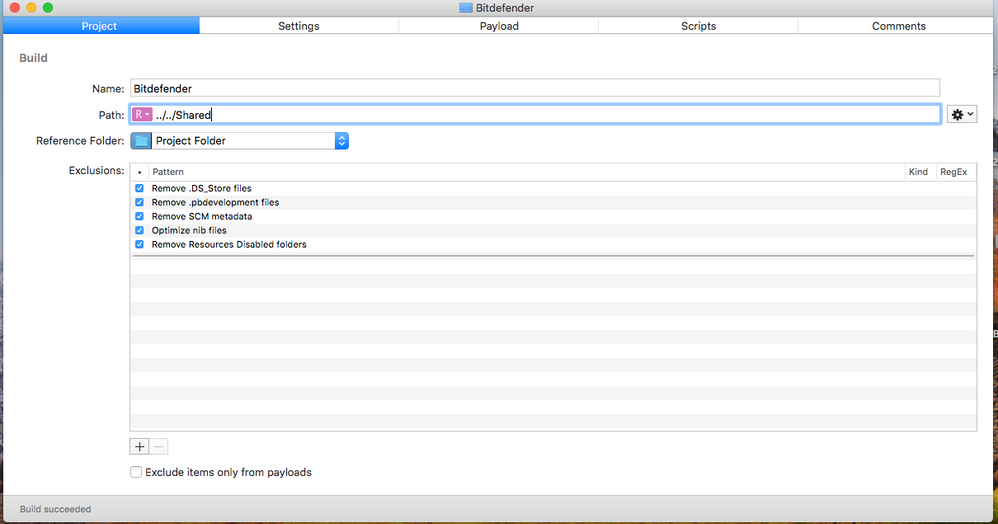
You don't use Composer. I use Packages, put the entire dmg into a project with a postinstall script that I reworked from @rtrouton .
#!/bin/bash
# Determine working directory
install_dir=`dirname $0`
# Specify location of the Junos Pulse disk image
diskimage=$install_dir/"Bitdefender_for_MAC.dmg"
# Specify a /tmp/junospulse.XXXX mountpoint for the disk image
tmpmount=`/usr/bin/mktemp -d /private/tmp/bitdefender.XXXX`
# Mount the disk image to the /tmp mountpoint
hdiutil attach "$diskimage" -mountpoint "$tmpmount" -nobrowse -noverify -noautoopen
# Install Bitdefender
/usr/sbin/installer -dumplog -verbose -pkg "$(/usr/bin/find $tmpmount -maxdepth 1 ( -iname *.pkg -o -iname *.mpkg ))" -target "$3"
# Unmount the disk image
/usr/bin/hdiutil detach "$tmpmount"
# Remove the /tmp mountpoint
/bin/rm -rf "$tmpmount"
exit~[upload](d89cb861151043599020941bd13b060a)- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-18-2018 03:15 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-13-2018 03:15 PM
https://www.bitdefender.com/support/how-to-install-bitdefender-endpoint-security-for-mac-through-jamf-pro-10-x-2243.html
https://www.bitdefender.com/support/How-to-whitelist-Bitdefender-Endpoint-Security-for-Mac-Kernel-Extensions-using-Jamf-Pro-10-x-2242.html
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-27-2018 07:02 PM
@ProFX So the directions seem a little sketchy.
- "Click Scripts and configure the Files and Processes payload. Enter the following Execute Command: installer –pkg /Users/Shared/antivirus_for_mac.pkg –target /" * This part doesn't make any sense and the screenshot doesn't match. Is this a script or is this an execute command?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-27-2018 08:29 PM
@franton Can you share more details with your project in packages. I was able to create a package, but the GUI said there was a error and I'm afraid that JAMF will not like that. The software seems to have installed find though.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-28-2018 03:06 PM
@kericson Yeah, that part of the instructions were a bit wonky. I used the "Execute Command" field under "Files and Processes". Also, the command I used was this:
/usr/sbin/installer -pkg "/Library/Application Support/Bitdefender/antivirus_for_mac.pkg" -target /
I was having issues with the original command shown in the instructions on the Bitdefender site and JAMF support had me modify it to the above. Note that I changed the location of the installer file as well.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-29-2018 12:55 AM
We have switched from McAfee to Bitdefender at our site. The overall feedback from users has been positive however our developers have been less than enthusiastic. The reason for this is that we didn't get our whitelist correct on rollout for Antimalware settings which caused longer compile times when using Xcode.
Which seem strange seeing that we migrated all the setting from McAfee then we found out why. Bitdefender do not allow you to use ~ to reference users home folders or wildcards for folder paths. This means if you need to whitelist ~/Library/Developer and ~/Documents/ from on access scans you will need to put the full path of every user into the policy. We now have 1000 entries in the whitelist which we need to manually mange per user. We have raised this as an issue and asked for the feature to be included in a future release after all you can do this for PC users.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-29-2018 12:17 PM
@kerickson Yeah I put the installer command in the "Execute Command" section. It needs that to actually install the package as root once it downloads the bitdefender package from Jamf. I also noticed that you can't copy and paste it because of something with the text encoding used on their website; the dashes aren't actual dashes and the command will fail. So just type the command yourself in the necessary field and it should work. It's been working like a charm for me in High Sierra. Now Mojave security just messed up everything again smh. For my computers on Mojave I have to go to each machine and enable Full Disk control manually for my modules to work. Hope this helps!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-21-2019 01:46 PM
@ProFX Do you know if there is a way to get around enabling Full Disk Control for Bitdefender? I thought that was what TCC or PPPC was for?
(EDIT:) Nevermind, this was answered here:
From that post - Yes, there are TCC/PPPC profiles that still have to be created to prevent admins/users from manually allowing full disk access. Wish it or examples were supplied by Bitdefender. I guess I have to figure this out this week.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-22-2019 12:51 AM
Hi Folks,
This might be a little late, but if anyone is still interested, here is a script I wrote that downloads the latest pkg from your GravityZone appliance and installs it. First download the DMG package from your server and copy the content of the included XML manually.
I would also recommend once you have finished tweaking the script, package it using Packages or Composer as a postintall script and sign it, to avoid issues with Mojave. Make sure to allow Full Disk Access using PPPC in Jamf Pro.
#!/bin/bash
# Global variables
bd_tmp="/tmp/bd_tmp_folder"
bd_xml="${bd_tmp}/installer.xml"
bd_url="https://bitdefender.example.com/Packages/MAC/0/antivirus_for_mac.pkg"
bd_pkg="${bd_tmp}/bitdefender.pkg"
# check for previously installed app
echo "Checking for previously installed app..."
if [[ -d "/Library/Bitdefender/AVP/Uninstaller/BitdefenderforMacUninstaller.app" ]]; then
echo "Found previous installation.."
echo "Removing previous installation..."
find "/Library/Bitdefender/AVP/Uninstaller/BitdefenderforMacUninstaller.app" -type f -name "*uninstall.scpt*" -exec osascript {} ;
# ##this can be flaky, as sometimes it won't work silently###
###you can choose to remove this whole section if you are installing on new computers###
echo "Previous installation removed..."
echo "Staring new installation process..."
else
echo "No installation found..."
echo "Staring installation process..."
fi
# create temp working folder
if [[ -d "${bd_tmp}" ]]; then
echo "Found old temp folder..."
echo "Deleting old temp folder now..."
rm -rf "${bd_tmp}"
echo "Creating new BitDefender temp folder..."
mkdir -p "${bd_tmp}"
else
echo "Creating BitDefender temp folder..."
mkdir -p "${bd_tmp}"
fi
# create bd installer xml
# replace below XML with yours
echo "Creating BitDefender installer xml file..."
echo '<?xml version="1.0" encoding="utf-8"?>
<config version="1.0">
<features>
<feature name="FileScan" action="1" />
<feature name="UserControl" action="0" />
<feature name="Antiphishing" action="0" />
<feature name="Firewall" action="0" />
<feature name="UpdateServer" action="0" />
<feature name="BehavioralScan" action="0" />
<feature name="TrafficScan" action="0" />
<feature name="MailServers" action="0" />
<feature name="DataLossPrevention" action="0" />
<feature name="PowerUser" action="0" />
<feature name="VolumeEncryption" action="0" />
<feature name="EventCorrelator" action="0"/>
</features>
<epagConfig>
<authToken strVar="EpagToken">{INSTALL_TOKEN}</authToken>
</epagConfig>
<serverAddress strVar="EpagServer">https://BDcommunication.example.com:8443/hydra</serverAddress>
<customerId strVar="EpagCustId">########################</customerId>
<connTime strVar="EpagConnTime">1800</connTime>
<userId strVar="EpagUserId">########################</userId>
<downloadUrl strVar="DownloadUrl"><![CDATA[https://BDcommunication.example.com:8443/Packages/MAC/0]]></downloadUrl>
<installPath strVar="InstallDir"><![CDATA[%PROGRAMFILES%]]></installPath>
<localization strVar="localization">en-US</localization>
<arrakisUpdateServer strVar="ArrakisUpdateServer">192.168.1.1:7074</arrakisUpdateServer>
<rebootIfNeeded var="RebootIfNeeded">0</rebootIfNeeded>
<forceResumeAfterReboot var="ForceResumeAfterReboot">0</forceResumeAfterReboot>
<disableScanBeforeInstall var="DisableScanBeforeInstall">1</disableScanBeforeInstall>
<encryptedPass></encryptedPass>
<remoteScanSettings>
<servers>
</servers>
<enableRemoteScan>0</enableRemoteScan>
</remoteScanSettings>
<scanType strVar="ScanType">full</scanType>
<scanTypeDetection>
<detectEC2 scanType="full" enableRemoteScan="0" detectEC2Url="http://169.254.169.254/latest/meta-data/instance-id">0</detectEC2>
<detectVM scanType="remote" enableRemoteScan="1">1</detectVM>
<detectSlowMachine scanType="light" enableRemoteScan="1">1</detectSlowMachine>
</scanTypeDetection>
<appId var="AppIdProduct">61</appId>
<productName strVar="ProductName"><![CDATA[Bitdefender Endpoint Security Tools]]></productName>
<ArrakisProductName strVar="ArrakisProductName"><![CDATA[Endpoint Update Server]]></ArrakisProductName>
<trackingInfo>
<key>########################</key>
<partnerId>84</partnerId>
<productId>2733</productId>
</trackingInfo>
<keepSettings var="KeepSettings">1</keepSettings>
<keepFeatures var="KeepFeatures">0</keepFeatures>
<proxyServer strVar="ProxyServer"></proxyServer>
<proxyPort strVar="ProxyPort"></proxyPort>
<proxyUser strVar="ProxyUser"></proxyUser>
<proxyPass strVar="ProxyPass"></proxyPass>
<installLink strVar="InstallLink"></installLink>
<rebootAfterEachRemovedProduct var="RebootAfterEachRemovedProduct">0</rebootAfterEachRemovedProduct>
<epagCustomField strVar="EpagCustomField"><![CDATA[[]]]></epagCustomField>
<submitDumps var="SubmitDumps">1</submitDumps>
<submitQuar var="SubmitQuar">1</submitQuar>
<submitQuarInterval var="SubmitQuarInterval">86400</submitQuarInterval>
<submitSuspicious var="SubmitSuspicious">1</submitSuspicious>
</config>
' > "${bd_xml}"
# download the BitDefender Installer
echo "Downloading BitDefender Installer..."
curl -o "${bd_pkg}" "${bd_url}" --progress --retry 5
# install the application
echo "Installing BitDefender package..."
installer -allowUntrusted -pkg "${bd_pkg}" -target /
echo "Deleting temp folder now..."
rm -rf "${bd_tmp}"
# run the application updates
echo "Installing BitDefender updates..."
/Library/Bitdefender/AVP/BDLDaemon >/dev/null 2>&1
echo "Done."
exit 0Hope this helps, best regards,
Kamal
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-22-2019 08:23 PM
@DFree I used the PPPC-Utility (https://github.com/jamf/PPPC-Utility) to drag and drop the applicable Bitdefender files (/Library/Bitdefender/AVP/BDLDaemon and /Library/Bitdefender/AVP/EndpointSecurityforMac.app) for Full Disk Access (SystemPolicyAllFiles) to create the configuration profile. In addition to adding the KEXT it's completely silent. Also set the script to remove /Applications/Bitdefender directory (don't need anyone to see the uninstall). Pretty easy!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-23-2019 09:43 AM
What about performance? My threat management team is moving off McAfee and using Windows Defender - Advance Threat Protection (ATP) - They chose this because it integrates into ATP...
My concern is - in previous deployments - this becomes both a CPU hog - and the real-time protection doesn't pick up things - MacWorld even confirmed this
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-23-2019 03:01 PM
@cturcich Thanks again.
Yes, dragging and dropping on there was easy after all with the PPPC Utility. We can even upload it to jamfcloud automatically, wow.
The KEXT whitelist was easy, just had to add the Team ID GUNFMW623Y.
I also took your suggestion to add to the script to delete the /Applications/Bitdefender folder too. It just contains an alias to the real uninstaller that lives in a folder in the same /Library/Bitdefender/AVP path.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-03-2019 08:31 AM
Hi guys, has anyone worked out how to uninstall Bitdefender without user interaction?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-18-2019 04:52 AM
@Sanchi You should be able to push the uninstall from "Tasks" in the BD Admin Console and the end user won't have to do anything.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-18-2019 04:48 AM
@atticushamp Thanks thats correct. I had a word with the Security guys and had them uninstall from the console which worked well.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-16-2019 01:13 PM
@greatkemo Are you still using this for Catalina?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-16-2019 11:58 PM
@Garci4 yes we do, and working fine, the only thing that is added is a notification profile so that the user does not get prompted to allow or disallow notifications
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-11-2020 11:57 AM
@greatkemo sorry to revive this thread but how did you create the notification profile?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-11-2020 01:15 PM
@MadMacs you use ProfileCreator (google it, it’s free) to create notifications profiles and upload it to Jamf pro.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-13-2020 05:08 AM
@greatkemo Thanks, I'm trying that but the interface is a bit small.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-13-2020 05:49 AM
We recently switched from AirWatch and BitDefender over to Jamf and Jamf Protect. We ran the trial for awhile and it seems ok and had no issues.