- Jamf Nation Community
- Products
- Jamf Pro
- Re: Chrome and Kerberos Single Sign On
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Chrome and Kerberos Single Sign On
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-21-2014 12:06 PM
Hello - I am configuring Chrome to use kerberos to single sign on to my workplace home page but it isn't working.
We do not want to use MCX due to previous issues using them in our environment.
I have set the whitelist domains using:
sudo defaults write /Library/Preferences/com.google.Chrome.plist AuthNegotiateDelegateWhitelist '.domain.intra'
sudo defaults write /Library/Preferences/com.google.Chrome.plist AuthServerWhitelist '.domain.intra'
However loading the homepage still requests credentials. In Firefox, everything works fine once I set the domains.
Any idea why it doesn't work? Am I missing a setting? Ive tried forcing certain authentications too but then the page will not load at all.
Thanks for any help..
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-21-2014 01:31 PM
@tegelaar, those settings need to be set at a user-level.. so if run as a policy at login this may work:
#!/bin/sh
sudo defaults write /Users/$3/Library/Preferences/com.google.Chrome.plist AuthNegotiateDelegateWhitelist '*.domain.intra'
sudo defaults write /Users/$3/Library/Preferences/com.google.Chrome.plist AuthServerWhitelist '*.domain.intra'But we successfully deploy this via Managed Preferences.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-22-2014 10:47 AM
Is this still working for you? We did the same thing through managed preferences and with the latest chrome it no longer works.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-22-2014 10:57 AM
Even if I set the policy manually and verify it is correct via chrome://policy/ it does not work. Firefox and Safari both work. I checked klist and I have a valid kerberos ticket too. Was hoping there was an additional setting I am missing. I am on Version 35.0.1916.114.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-22-2014 11:00 AM
not that I can help but how do you get it to work with Safari???
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-22-2014 11:05 AM
Version 35 is when it stopped working for me. I just reverted to the latest version of 34 and it works normally
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-22-2014 11:47 AM
@ooshnoo You don't need to configure Safari to do Kerberos. The server needs to be configured to do Kerberos (or Negotiate in IIS) authentication, the system needs to be bound, and the user needs to have a TGT (which he would get at login - check via klist).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-22-2014 12:37 PM
Thanks JP... Doesn't work for us here on Safari. Maybe IIS or AD isn't configured correctly.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-23-2014 09:23 AM
So after looking into it a little bit more, I noticed that most the managed preferences I have for Chrome work, but the "cloud print" ones that I have that are used to disable it are not working. Anyone else seeing this?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-11-2016 12:58 AM
Bump:
@bentoms I'm not sure what method to use Managed Preferences or Default Writes (haven't used Managed Prefs much) - Are the Chrome settings configured as Global Preference?
Also wondering if using the defaults write command, do the settings tend to 'stick' if upgrading Chrome at a later point etc.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-11-2016 07:15 AM
@dajackson Nowadays, I do this via a custom setting Config Profile.
You could write a plist out with the defaults commands above, & then upload to the JSS to create the profile.
They will then stick.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-11-2016 12:20 PM
This is great, thanks guys! Quick question... if you want to add more than one site, how would you do that?
<key>AuthNegotiateDelegateWhitelist</key>
<string>*.site.com *.site2.com</string>
<key>AuthServerWhitelist</key>
<string>*.site.com *.site2.com</string>That doesn't seem to work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-01-2016 09:11 AM
Haven't been able to find a solution to adding multiple domains. comma separated, space, etc...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-03-2016 11:37 AM
@tegelaar Hey there, I am doing this for my Org. Did you ever find success with this? FF works fine..... Chrome does not
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-03-2016 11:46 AM
@tegelaar We're using the following for Chrome
# Variables
loggedInUser=`/bin/ls -l /dev/console | /usr/bin/awk '{ print $3 }'`
loggedInUserHome=`dscl . -read /Users/$loggedInUser NFSHomeDirectory | awk '{print $NF}'`
tld="*.company.com"
# Google Chrome
/bin/echo "*** Enable single sign-on in Google Chrome for $loggedInUser ***"
/bin/echo "Quit all Chrome-related processes"
/usr/bin/pkill -l -U ${loggedInUser} Chrome
if [ -f "/Users/$loggedInUser/Library/Preferences/com.google.Chrome.plist" ]; then
# backup current file
/bin/cp "/Users/$loggedInUser/Library/Preferences/com.google.Chrome.plist" "/Users/$loggedInUser/Library/Preferences/com.google.Chrome.plist.backup"
/bin/echo "Preference archived as: /Users/$loggedInUser/Library/Preferences/com.google.Chrome.plist.backup"
/usr/bin/defaults write /Users/$loggedInUser/Library/Preferences/com.google.Chrome.plist AuthNegotiateDelegateWhitelist $tld
/bin/echo "AuthNegotiateDelegateWhitelist set to $tld for $loggedInUser"
/usr/bin/defaults write /Users/$loggedInUser/Library/Preferences/com.google.Chrome.plist AuthServerWhitelist $tld
/bin/echo "AuthServerWhitelist set to $tld for $loggedInUser"
/usr/sbin/chown $loggedInUser /Users/$loggedInUser/Library/Preferences/com.google.Chrome.plist
# Respawn cfprefsd to load new preferences
/usr/bin/killall cfprefsd
else
/bin/echo "Google preference not found for $loggedInUser"
fi- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-09-2017 11:35 AM
Anyone get this working? @dan.snelson - I ran the script, checked the pref file and the Okta tld is set for AuthNegotiateDelegateWhitelist and AuthServerWhitelist, but I'm still getting a request for credentials when I hit our test page.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-09-2017 03:07 PM
@smamdani What output do you get when you enter klist in Terminal?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-09-2017 03:30 PM
So I did finally get it working. The disconnect in my head was that you have to whitelist the internal server where you have the Okta agent running, while I was trying to whitelist *.okta.com.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-09-2017 03:36 PM
@smamdani Good deal. Take care.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-29-2018 10:48 PM
Hi there, works fine with one domain only, but did anybody get it to run with more than one domain?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-09-2018 06:51 AM
@andreassauer I have done some testing with the script posted above. It seems that if you just seperate the domains with commas it works.
I and stealing and reposting the script from above with the addition to reflect this. I cannot personally fully test this. However i have tested this to some degree by changing company1 and company3 around. If you dont mind sir let me know if you test this and it works.
# Variables
loggedInUser=`/bin/ls -l /dev/console | /usr/bin/awk '{ print $3 }'`
loggedInUserHome=`dscl . -read /Users/$loggedInUser NFSHomeDirectory | awk '{print $NF}'`
tld="*.company1.com,*.company2.com,*company3.com"
# Google Chrome
/bin/echo "*** Enable single sign-on in Google Chrome for $loggedInUser ***"
/bin/echo "Quit all Chrome-related processes"
/usr/bin/pkill -l -U ${loggedInUser} Chrome
if [ -f "/Users/$loggedInUser/Library/Preferences/com.google.Chrome.plist" ]; then
# backup current file
/bin/cp "/Users/$loggedInUser/Library/Preferences/com.google.Chrome.plist" "/Users/$loggedInUser/Library/Preferences/com.google.Chrome.plist.backup"
/bin/echo "Preference archived as: /Users/$loggedInUser/Library/Preferences/com.google.Chrome.plist.backup"
/usr/bin/defaults write /Users/$loggedInUser/Library/Preferences/com.google.Chrome.plist AuthNegotiateDelegateWhitelist $tld
/bin/echo "AuthNegotiateDelegateWhitelist set to $tld for $loggedInUser"
/usr/bin/defaults write /Users/$loggedInUser/Library/Preferences/com.google.Chrome.plist AuthServerWhitelist $tld
/bin/echo "AuthServerWhitelist set to $tld for $loggedInUser"
/usr/sbin/chown $loggedInUser /Users/$loggedInUser/Library/Preferences/com.google.Chrome.plist
# Respawn cfprefsd to load new preferences
/usr/bin/killall cfprefsd
else
/bin/echo "Google preference not found for $loggedInUser"
fi- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-05-2018 11:56 AM
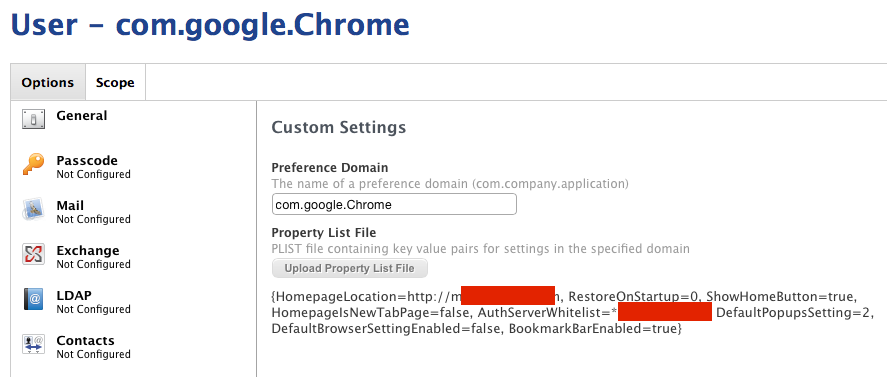
Was wondering if anybody might be able to post their plist that is working? Not having luck. Running High Sierra and Latest version of Chrome. With JAMF Pro 10.
This is what my plist is looking like. The *.company.com is being replaced with my companies domain.
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>AuthNegotiateDelegateWhitelist</key>
<string>.company.com</string>
<key>AuthServerWhitelist</key>
<string>.company.com</string>
<key>KeychainReauthorizeInAppSpring2017</key>
<integer>1</integer>
<key>KeychainReauthorizeInAppSpring2017Success</key>
<true/>
<key>LastRunAppBundlePath</key>
<string>/Applications/Google Chrome.app</string>
</dict>
</plist>
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-20-2018 07:27 AM
i have tried all steps it doesn't work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-20-2018 07:27 AM
i have tried all steps it doesn't work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-11-2018 07:19 AM
Has anyone got IWA to work on chrome using high sierra?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-08-2019 08:17 PM
@Mbooth IWA and Chrome works for us in High Sierra (10.13.6), but doesn't work on Mojave (10.14.2) Firefox and Safari seems to work okay.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-09-2019 10:01 AM
@bbot In a single test with macOS 10.14.2 (18C54) and Chrome 71.0.3578.98, it's working for me for a single domain.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-09-2019 10:03 AM
Thanks for the info @dan-snelson . I'm going to be reimage a new Mac with Mojave and try again without any of our company software on there..
Are you using a configuration profile or a one time script to configure the settings? We've been deploying it via config profile successfully up until 10.13.6.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-09-2019 10:25 AM
@bbot We're using a one-time script via Self Service.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-09-2019 03:25 PM
@dan-snelson what version of the IWA web app are you running?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-10-2019 09:17 AM
@bbot We don't use Okta IWA Web App for Desktop SSO.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-18-2019 10:44 AM
This may be a silly question, but once the changes to the WhiteLists are made and Chrome restarted, so long as a machine has a valid Kerberos ticket then SSO should work and just pass through correct? I've been trying for some time now and continue to get the prompts within Chrome when trying to access expected resources. Machine is bound, Kerberos ticket, 10.14.2 and latest Chrome.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-18-2019 10:46 AM
@andrew.nicholas I believe @bbot is running a similar setup; we no longer bind, using just Enterprise Connect, and Chrome is working for us with a single domain.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-18-2019 10:52 AM
@dan-snelson Thanks dan, we still bind for a myriad of reasons but the accounts are local with EC tie ins as well.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-07-2020 09:22 AM
@andrew.nicholas we're in the same boat, unable to get it to work on 10.14, 10.15, have you had success with this?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-06-2020 06:07 AM
Agentless DSSO for my OKTA Tenant now works with these preferences
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-28-2020 04:21 AM
This should work successfully when setting the config via a managed Plist, won't work from the terminal
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-27-2021 12:25 PM
I needed to add “AuthNegotiateDelegateByKdcPolicy” true
See: https://chromeenterprise.google/policies/#AuthNegotiateDelegateByKdcPolicy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-23-2022 04:35 PM
In case anyone else is looking at this thread in 2022, the current supported method (in my testing) is the configuration profile one, and the keys all use the term "allowlist" instead of "whitelist". Good documentation here: https://chromeenterprise.google/policies/#HTTPAuthentication
Here's my working config profile:
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>AuthNegotiateDelegateAllowlist</key>
<string>*.company.com</string>
<key>AuthServerAllowlist</key>
<string>*.company.com</string>
<key>AuthNegotiateDelegateByKdcPolicy</key>
<true/>
</dict>
</plist>
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-11-2023 05:27 AM
Thank you ncworster! This was exactly the fix we needed for our company. we changed the keys to "allowlist" and now sso is working properly for Google Chrome.