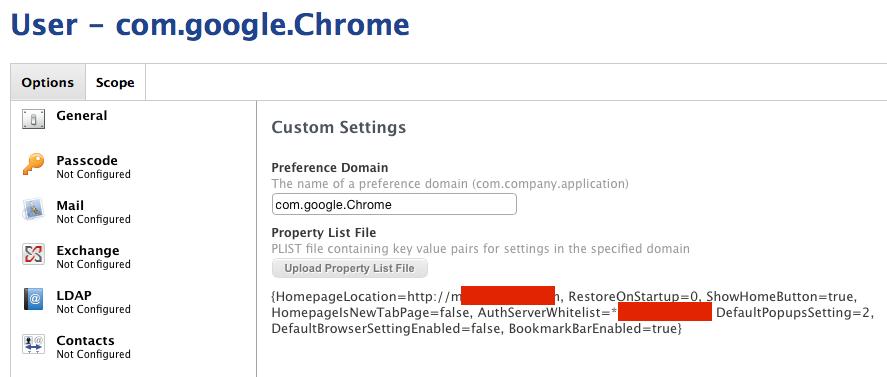
Hello - I am configuring Chrome to use kerberos to single sign on to my workplace home page but it isn't working.
We do not want to use MCX due to previous issues using them in our environment.
I have set the whitelist domains using:
sudo defaults write /Library/Preferences/com.google.Chrome.plist AuthNegotiateDelegateWhitelist '.domain.intra'
sudo defaults write /Library/Preferences/com.google.Chrome.plist AuthServerWhitelist '.domain.intra'
However loading the homepage still requests credentials. In Firefox, everything works fine once I set the domains.
Any idea why it doesn't work? Am I missing a setting? Ive tried forcing certain authentications too but then the page will not load at all.
Thanks for any help..