- Jamf Nation Community
- Products
- Jamf Pro
- Re: Cisco Umbrella/openDNS on iOS
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Cisco Umbrella/openDNS on iOS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on
10-01-2020
09:21 AM
- last edited
a week ago
by
![]() kh-richa_mig
kh-richa_mig
Hello Everyone,
We are approximately six months into Distance Education at our K12 institution and are looking to push out a payload to route all student iPad traffic through Cisco Umbrella. We are currently using Umbrella district wide both for on-campus network filtering and also for all Chromebook traffic (including at home).
We have successfully linked Umbrella with JAMF, as you can see in the below screenshot.
The downside we are seeing is that in order for the DNS routing to work you must install the Cisco Security Connector. This is fine and all, but it also appears that this application must be opened prior to any data following through OpenDNS? Has anybody run into a similar scenario and found a solution?
It feels like our department can do everything on our end to get this ready to go but if the student doesn't open this app at least once they will be able to browse unfiltered internet.
Here is the link to the official documentation from Cisco on deployment.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-14-2021 11:09 AM
We have been using the Cisco Security Connector App on remote use iPads. We have not found that the user had to open the App or anything for it to work.
We had an issue getting the Configuration Profile to load successfully to make CSC fully functional - turned out we had another App that used Content Filter plug-in and the iPad can only leverage 1 at a time. In our case we could dump the other App in favor of CSC.
This is just a guess based on my 1 experience - but I am going to say that if you try the CSC App and follow Cisco's directions for the config profile, all will work.
FYI - there is a guy from Cisco posting helpful answers about Cisco AMP (a sister product) for Big Sur on the other board. Maybe a post over there will catch his eye.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-19-2021 07:19 AM
Hi Guys,
Question for you - and hoping you have encountered this now that you've probably supported both distance and return to on-premise.
iPads, Cisco Security Connector - deployed, and working for at-home students.
Return to on-premise, and we can't get identity info to apply the mobile device policy - only network policy applies.
What is the missing bit to supply identity to the VA's from on-premise iPads?
Chromebooks appear to the trusted network detection, and full computers have AD login events to watch for identity to local IP correlation. But what about IOS?
We don't have Clarity deployed/enabled - is that the missing bit?
Thanks in advance!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-19-2021 07:19 AM
Hello,
Hoping you can provide insight based on your experience. We too deployed the Cisco Security Connector App on our iPads and were successfully able to apply Umbrella policy to the devices when they were used at home. However, when those same devices are on-premise, they are subject to the more general network policy and do not appear to provide identity to the VA's. Our computers have a login event that is picked up by the AD script, providing correlation between the local private IP and login name. But not so with the iOS devices. Do you have any insight into how to successfully apply consistent Umbrella policy to the iOS devices, on and off premise? We do not have Cisco Clarity installed/enabled. Is that a necessary component for identity to be provided to the on-premise VAs (similar to what happens with Chromebooks using 'trusted network detection' and supplying identity). ? Thank you in advance!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-27-2021 05:22 AM
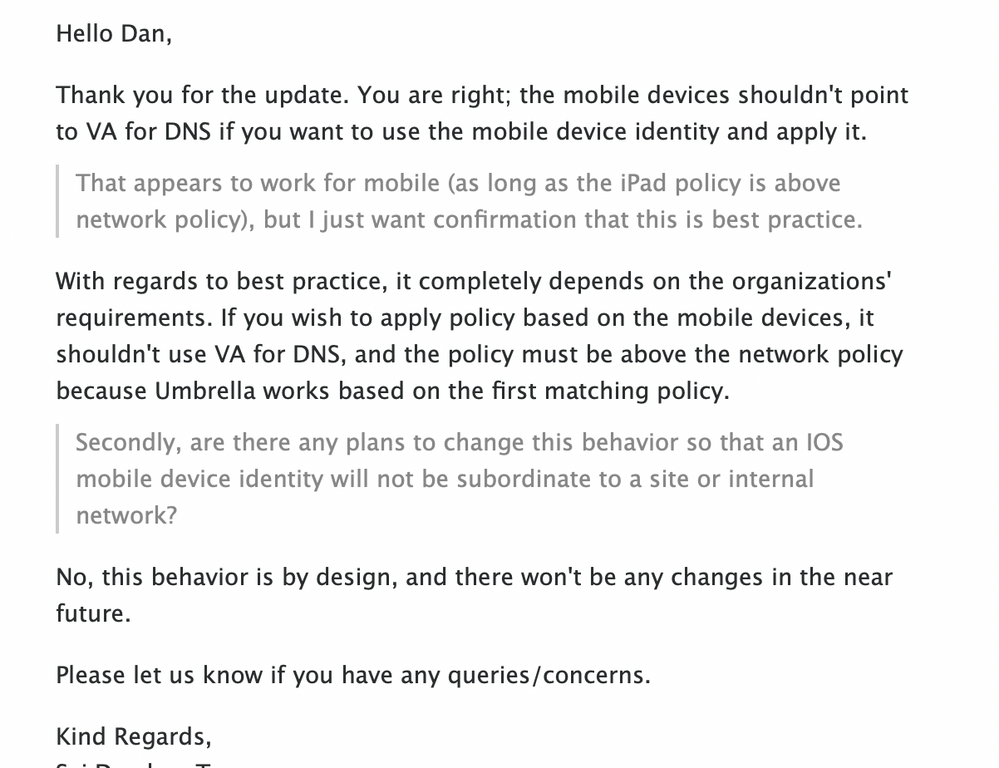
I found the answer on this, confirmed by cisco and testing - if you want the mobile device policy to continue to be applied while on-premise, the devices need to not use the on-premise Umbrella VA's for DNS resolution. Beyond that, because policies are applied in order from top to bottom, the mobile device policy needs to be above the default policy (which is applied to the site because of the trusted network egress IP).
So in our case, that means having the iPads join a subnet configured to supply our standard AD DNS servers in the DHCP response rather than the Umbrella VAs. Then we get our granular policy application from the mobile identity (and roaming client identities) same as off-premise, but with the default policy being catch-all for any device egressing from the site that doesn't have the Connector App or roaming client. Another option would have been grouping the iPads on unique internal subnet (via separate SSID, VLAN derivation, etc.) and applying a unique policy to that internal network. But that seems harder to do for grade-level specific grouping.
Secondly, I had been hoping that WPA2 Enterprise network auth against our Microsoft NPS RADIUS (and AD) would produce a login event (Event 4624) that the Cisco Umbrella AD connector would see/use to correlate username with local IP, as it does for roaming clients. But, although username is present in Windows Event 4624, local IP is not present, so this information is not correlated by Umbrella and AD username or AD group can't be used for Umbrella policy for iOS devices.
Also, a colleague confirmed the the Cisco Clarity component has nothing to do with identity as I was first wondering - it is strictly supplying info to Cisco AMP.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-16-2024 07:48 AM
Following up on this with update in case anyone hits it looking for guidance. As of 2022 and with the current ios and MacOS clients:
- Cisco Security Connector for iOS—version 1.6.3 or later.
- Cisco Secure Client for MacOS (replaced Umbrella Roaming Client)
You can use AD identity for policy enforcement with MacOS and IOS by setting the UPN attribute (set to the user's e-mail address typically) in your Jamf deployment. Once that is set, the user's identity is available to Umbrella and you can build your policies, apply to different AD groups, and manage by moving users in and out of your AD groups in AD.
To activate:
MacOS:
Place com.cisco.umbrella.client.plist in
/Library/Managed Preferences
..with single key for <UPN>
https://docs.umbrella.com/deployment-umbrella/docs/macos-mobile-device-management
iOS:
MobileDevice distribution from MDM. Download and modify the mobileconfig file modifying key:
<dict>
...
<key>userPrincipalName</key>
<string>{{EmailAddress}}</string>
...
</dict>
https://docs.umbrella.com/deployment-umbrella/docs/add-user-identity-for-cisco-security-connector
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-24-2024 02:34 PM
I have been using a proof of concept policy to push out the DNS proxy without any app installed and it's worked great. Eventually a decision will be made for a fully featured endpoint protection solution, but for now, this is providing the DNS filtering at least. I have a profile that pushed out the Cisco root certificate, and once that was out there, a second profile that configured the secure DNS URL and the IP addresses of the resolvers. Most endpoint protection solutions appear to be a DNS proxy, a mobile app, and a central console for monitoring and reporting. What I have in place is a no cost configuration profile for the DNS proxy, no mobile app to manage, but no console either.