Creating a WebContentFilter Payload for Cisco AMP
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-02-2020 10:05 AM
Hi all,
I'm following Cisco documentation to prepare for deploying a new AMP connector that is compatible with Big Sur.
I'm aware of where/how to add & configure payloads for allowed system extensions, system policy kernel extensions, and full disk access... But I'm stuck on configuring the web content filter payload. I can't find any equivalent spot in configuration profiles to set these.
https://www.cisco.com/c/en/us/support/docs/security/amp-endpoints/216089-advisory-for-amp-for-endpoi...
I tried searching around on my own, but "web content filter" just gets me hits on folks blocking web URLs, essentially.
Where/how is this payload configured?
Thanks in advance!
- Labels:
-
Configuration Profiles
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-04-2020 06:32 PM
Maybe in the console for AMP?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-04-2020 06:37 PM
@dlondon The image of settings are shown to be a payload to push through one's MDM of choice. (See fixed link for more details, I screwed up the URL before) This is not anything in the AMP console.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-04-2020 11:26 PM
The WebContentFilter payload is not yet supported.
https://www.jamf.com/jamf-nation/feature-requests/9670/configuration-profiles-add-web-content-filter...
You can create the profile manually or using ProfileCreator and sign/upload it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-21-2020 11:39 AM
@ajc196 did you manage to get the System Extension approved for Cisco AnyConnect on Big Sur?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-10-2020 04:59 AM
+1
Having the same issue here for AMP. Also can't shake the visual Sys. Ext. warning windows either, even after following Cisco's advisory docs :-(
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-12-2020 11:39 AM
@tsylwest I think you hit the same problem as me. I found the problem.
ProfileCreater 0.3.2 does not support the com.apple.system-extension-policy System Extension payload. When you load a profile with that payload it will show you the raw xml but in read only form. What ProfileCreater doesn't tell you is that when you export the profile it strips out the com.apple.system-extension-policy System Extension payload. So the mobilconfig file you signed and uploaded to Jamf doesn't actually have the System Extension payload in it! Hence your problem. Once I worked this out I opened the mobileconfig file in a text editor and copied the dict back in before signing it.
Here is the full working xml for the Cisco advisory in the OP above. Save this xml as CiscoAmp.mobileconfig and use the instructions in this excellent post to sign the config file https://www.amsys.co.uk/sign-configuration-profile/:
You can import the file into ProfileCreator to verify the xml. Just don't export it as it will string out the System Extensions!
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>PayloadContent</key>
<array>
<dict>
<key>AllowUserOverrides</key>
<true/>
<key>AllowedSystemExtensionTypes</key>
<dict>
<key>DE8Y96K9QP</key>
<array>
<string>EndpointSecurityExtension</string>
<string>NetworkExtension</string>
</array>
</dict>
<key>AllowedSystemExtensions</key>
<dict>
<key>DE8Y96K9QP</key>
<array>
<string>com.cisco.endpoint.svc.securityextension</string>
<string>com.cisco.endpoint.svc.networkextension</string>
</array>
</dict>
<key>PayloadDescription</key>
<string></string>
<key>PayloadDisplayName</key>
<string>System Extensions</string>
<key>PayloadIdentifier</key>
<string>EB2A2110-BCA3-4EFD-AEE8-EB18B0FE57C5</string>
<key>PayloadOrganization</key>
<string>YOUR COMPANY HERE</string>
<key>PayloadType</key>
<string>com.apple.system-extension-policy</string>
<key>PayloadUUID</key>
<string>7B2A2110-BCA3-4EFD-AEE8-EB18B0FE57C5</string>
<key>PayloadVersion</key>
<integer>1</integer>
</dict>
<dict>
<key>FilterBrowsers</key>
<false/>
<key>FilterDataProviderBundleIdentifier</key>
<string>com.cisco.endpoint.svc.networkextension</string>
<key>FilterDataProviderDesignatedRequirement</key>
<string>anchor apple generic and identifier "com.cisco.endpoint.svc.networkextension" and (certificate leaf[field.1.2.840.113635.100.6.1.9] /* exists */ or certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = DE8Y96K9QP)</string>
<key>FilterGrade</key>
<string>firewall</string>
<key>FilterPackets</key>
<false/>
<key>FilterSockets</key>
<true/>
<key>FilterType</key>
<string>Plugin</string>
<key>PayloadDescription</key>
<string>Adds a Web Content Filter</string>
<key>PayloadDisplayName</key>
<string>Web Content Filter</string>
<key>PayloadIdentifier</key>
<string>19DE21F8-35AE-45B4-B8EE-3AC2A1F2B8B5.com.apple.webcontent-filter.BF054105-5232-49DB-ADA2-F334BFAFE7EA</string>
<key>PayloadOrganization</key>
<string></string>
<key>PayloadType</key>
<string>com.apple.webcontent-filter</string>
<key>PayloadUUID</key>
<string>7F054105-5232-49DB-ADA2-F334BFAFE7EA</string>
<key>PayloadVersion</key>
<integer>1</integer>
<key>PluginBundleID</key>
<string>com.cisco.endpoint.svc</string>
<key>UserDefinedName</key>
<string>AMP Network Extension</string>
</dict>
<dict>
<key>PayloadDescription</key>
<string>Configures Privacy Preferences Policy Control settings</string>
<key>PayloadDisplayName</key>
<string>Privacy Preferences Policy Control</string>
<key>PayloadIdentifier</key>
<string>6FB36903-B1BD-4670-B489-377AD3666415</string>
<key>PayloadOrganization</key>
<string>YOUR COMPANY HERE</string>
<key>PayloadType</key>
<string>com.apple.TCC.configuration-profile-policy</string>
<key>PayloadUUID</key>
<string>7FB36903-B1BD-4670-B489-377AD3666415</string>
<key>PayloadVersion</key>
<integer>1</integer>
<key>Services</key>
<dict>
<key>SystemPolicyAllFiles</key>
<array>
<dict>
<key>Allowed</key>
<integer>1</integer>
<key>CodeRequirement</key>
<string>anchor apple generic and identifier "com.cisco.endpoint.svc" and (certificate leaf[field.1.2.840.113635.100.6.1.9] /* exists */ or certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = DE8Y96K9QP)</string>
<key>Comment</key>
<string></string>
<key>Identifier</key>
<string>com.cisco.endpoint.svc</string>
<key>IdentifierType</key>
<string>bundleID</string>
<key>StaticCode</key>
<integer>1</integer>
</dict>
<dict>
<key>Allowed</key>
<integer>1</integer>
<key>CodeRequirement</key>
<string>anchor apple generic and identifier "com.cisco.endpoint.svc.securityextension" and (certificate leaf[field.1.2.840.113635.100.6.1.9] /* exists */ or certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = DE8Y96K9QP)</string>
<key>Comment</key>
<string></string>
<key>Identifier</key>
<string>com.cisco.endpoint.svc.securityextension</string>
<key>IdentifierType</key>
<string>bundleID</string>
<key>StaticCode</key>
<integer>1</integer>
</dict>
</array>
</dict>
</dict>
<dict>
<key>AllowUserOverrides</key>
<true/>
<key>AllowedKernelExtensions</key>
<dict>
<key>TDNYQP7VRK</key>
<array>
<string>com.cisco.amp.nke</string>
<string>com.cisco.amp.fileop</string>
</array>
</dict>
<key>PayloadDescription</key>
<string>Configures Kernel Extension Policy settings</string>
<key>PayloadDisplayName</key>
<string>Approved Kernel Extensions</string>
<key>PayloadIdentifier</key>
<string>902AECE7-6188-4B53-889F-9A9AE856D1FB</string>
<key>PayloadOrganization</key>
<string>YOUR COMPANY HERE</string>
<key>PayloadType</key>
<string>com.apple.syspolicy.kernel-extension-policy</string>
<key>PayloadUUID</key>
<string>702AECE7-6188-4B53-889F-9A9AE856D1FB</string>
<key>PayloadVersion</key>
<integer>1</integer>
</dict>
</array>
<key>PayloadDescription</key>
<string>Allow AMP system and policy extensions and full disk access</string>
<key>PayloadDisplayName</key>
<string>Cisco AMP 1.14.0 BigSur Ready</string>
<key>PayloadIdentifier</key>
<string>19DE21F8-35AE-45B4-B8EE-3AC2A1F2B8B5</string>
<key>PayloadOrganization</key>
<string>YOUR COMPANY HERE</string>
<key>PayloadScope</key>
<string>System</string>
<key>PayloadType</key>
<string>Configuration</string>
<key>PayloadUUID</key>
<string>79DE21F8-35AE-45B4-B8EE-3AC2A1F2B8B5</string>
<key>PayloadVersion</key>
<integer>1</integer>
</dict>
</plist>- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-12-2020 12:42 PM
@tsylwest You’re not alone. I similarly can’t get the System/Kernel Extension to approve without user intervention. But the Full Disk Access settings via PPPC seem to work fine.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-13-2020 09:26 AM
@user-kcfmSAoXyV and @tsylwest I hit your problem today during testing.
Problem: I deployed the Jamf payload and then successfully installed AMP 1.14.x while on Catalina without any user intervention. I then upgraded that machine to Big Sur and on reboot was prompted in the UI to allow the 2 system extensions (com.cisco.endpoint.svc.securityextension, com.cisco.endpoint.svc.networkextension).
I did manage to install AMP on Big Sur without user intervention, but had to uninstall AMP, remove the jamf payload, re apply the jamf payload and then reinstall AMP!
Another user upgraded to Big Sur and then applied the jamf payload and then upgraded to AMP v1.14 successfully without user intervention.
So it looks like the upgrade to Big Sur invalidates the Jamf payload's system extensions.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-13-2020 09:58 AM
Interestingly, its the Full Disk Access portion that DOESN'T appear to be working for me!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-16-2020 02:47 AM
Has anyone been able to push a working WebContentProfile? Mine pushes, but it looks empty, also if I navigate to the com.apple.webcontent-filter.plist file.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-16-2020 08:08 AM
@richard.wadsworth funnily enough, I have tested your solution with the scenario you described just now (catalina, upgrade Amp to 1.14, upgrade to big sur, rebooted a couple of times to make sure) and all seems to be good with the world :-| didn't get asked to approve anything...
However, this is all on our test/dev instance of jamfcloud with just AMP installed on the test macs, and will now need to run a few tests in production to confirm it works, but I wanted to thank you for your help so far, it's been very positive.
@EmilDIT have you tried Richard's solution higher up in this post? it contains all the settings from the Cisco advisory doc and it works for me here.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-17-2020 03:30 AM
@tsylwest the empty payload caught me off guard thanks a bunch!! We're rocking now on 10.15.17 on 1.14. Time to update to Big Sur and see what happens!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-17-2020 06:00 AM
Guys, for the life of me I've tried following the instructions (@richard.wadsworth) as mentioned above, but nothing seems to work. Every time I try to upload the mobileconfig profile and save it, my system errors out. Any further guidance would be much appreciated.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-17-2020 06:08 AM
@schultz Have you tried signing the profile before uploading it? Jamf can make changes to an unsigned profile when uploading it. It is much better to upload a fully signed profile. Check out this blog post:
Signing Packages and Profiles using Jamf Pros CA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-17-2020 07:14 AM
Tried signing it this time, and although I do not get the error, the System Extensions payload only has "Allow users to approve system extensions" enabled, but there is no Team Identifier, nor any system extensions defined.
Out of curiosity - are you all simply doing fresh installs of AMP? If I do that, there are no problems, even with my previous method of not bothering with the WebContentFilter. My problem seems to stem from an AMP 1.12 to 1.14 upgrade handled by the AMP Console. IF you have updated your endpoint to 1.14 and then update a JAMF MDM to the latest Cisco profile recommendations, the extension approval will fail. If you apply the MDM policy ahead of the 1.14 upgrade, it works as expected. If you uninstall and then install 1.14 client on a broken/updated MDM policy, it now works.
Delving a little deeper, I cannot even run the AMP uninstaller without manual admin intervention to remove the two extensions in question. I suspect this is why Apple is considering use of systemextensionsctl to address issues such as I am having. However, running the systemextensionsctl uninstall command requires System Integrity Protection (SIP) to be disabled and this limitation is supposed to be removed by Apple at some point in the very near future...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-19-2020 01:54 PM
I'm experiencing issue similar to yours schultz! Existing user base running 1.12 - I pushed the 1.14 update to them via the AMP admin console and then pushed the Configuration Profile using the XML provided above by Richard (my mistake for doing that AFTER the push). I'm currently trying to remotely uninstall the 1.14 client via Jamf and am struggling to get it to work reliably.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-20-2020 05:15 AM
ChrisJScott-work: If you are running 15.5 or higher on your Macs, you simply cannot automate the uninstall any longer. This is because the uninstall app that AMP provides calls two commands:
/Applications/Cisco AMP for Endpoints/AMP for Endpoints Service.app/Contents/MacOS/AMP for Endpoints Service deactivate endpoint_security
/Applications/Cisco AMP for Endpoints/AMP for Endpoints Service.app/Contents/MacOS/AMP for Endpoints Service deactivate content_filter
Both of these REQUIRE a GUI based admin authentication to deactivate these two extensions. You can thank Apple for that. Until Apple enables systemextensionsctl uninstall, we admins are going to have some difficulties with the Cisco AMP product.
Currently we're down to about 100 remaining Macs where we remote in, uninstall, and then reinstall AMP. Thankfully we have Bomgar to reach all our remote/offsite users.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-24-2020 08:26 AM
Hi.
Just seen that Jamf Pro 10.26.0 supports the Content Filter (New Payload) to provide compatibility with macOS Big Sur 11 so hopefully all the nonsense in this thread goes away.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-24-2020 08:38 AM
@schultz,
Did you follow the instructions here to sign you profile locally before uploading to Jamf?
Also, after much testing I realised the Kernel Extension dict in the profile was causing Big Sur to prompt the end user to accept those extensions. Frustratingly, the Big Sur message talked about System Extensions even though it meant Kernel Extensions! The fix is to remove the Kernel Extension dict from the above profile.
So my 100% successful upgrade path looks like this:
0. Starting position: AMP installed and working on MacOS (AMP version < 1.14) using "pre1-14.mobileconfig" that relies on Kernel Extensions
1. Get the device updated to Mac OS 10.15.7
2. Deploy the signed mobileconfig (from this thread but without the Kernel Extension dict) side by side with the existing pre1-14.mobileconfig
3. Upgrade (install) Amp 1.14 over whatever version was there before. I did not uninstall first.
4. Remove the pre1-14.mobileconfig
5. AMP is now running successfully on 10.15.7 using System Extensions only
6. Upgrade to Big Sur.
After much testing I realised the
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-30-2020 10:30 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-30-2020 01:11 PM
I tried making a Config Profile with the WebContentFilter for AMP (and another for AnyConnect), and pushed it to a 10.15.7 system. It shows applied in the System Preferences > Profiles section however the OS still prompts for an AMP WebContent Filter with approve or deny. I selected Deny, then rebooted, the AMP icon no longer complains about needing the Filter but this is quite clunky, you would like to it auto approve the Filter so the end user wouldn't see any popups. Does anyone have any ideas about this?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-03-2020 04:49 AM
Anyone had luck in getting AMP installing nicely on an Apple Silicon Mac yet? I removed the kext part of the current CP we had working, but I still get 2 System Extensions wanting some 'manual' attention.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
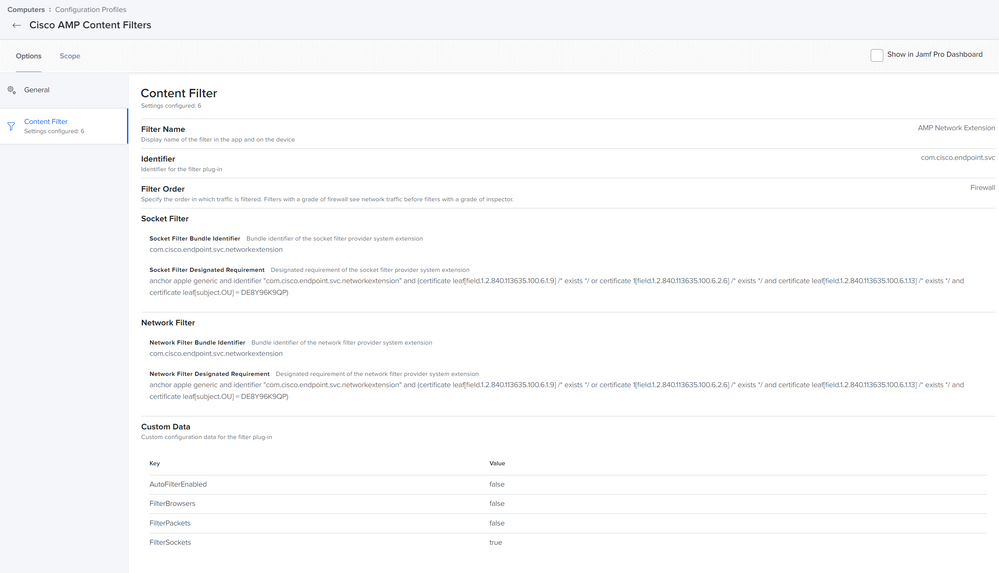
Posted on 12-09-2020 10:13 AM
We just got 10.26 and I'm working on the AMP WebContentFilter. Anyone have that working yet in their Config profile? I'm not sure I'm setting it right by the Cisco doc - https://www.cisco.com/c/en/us/support/docs/security/amp-endpoints/216089-advisory-for-amp-for-endpoints-mac-conne.html
Here is what my setting looks like:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-09-2020 12:27 PM
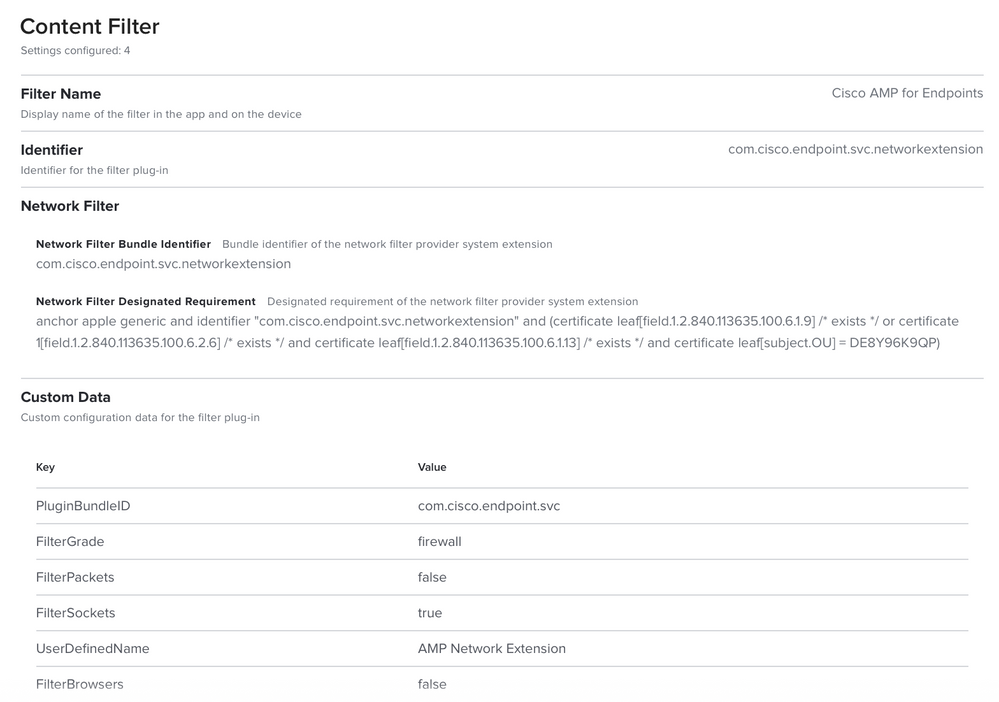
@ccliff I created my config profile the other day and just tested on a freshly installed/enrolled Big Sur 11.0.1 machine. AMP 1.14 installed fine with no prompts and no faults. Attached is what my config profile looks like. I believe either the socket or network filter I set might be redundant or unneeded, but it works so I'm leaving it be and not tempting fate. :P
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
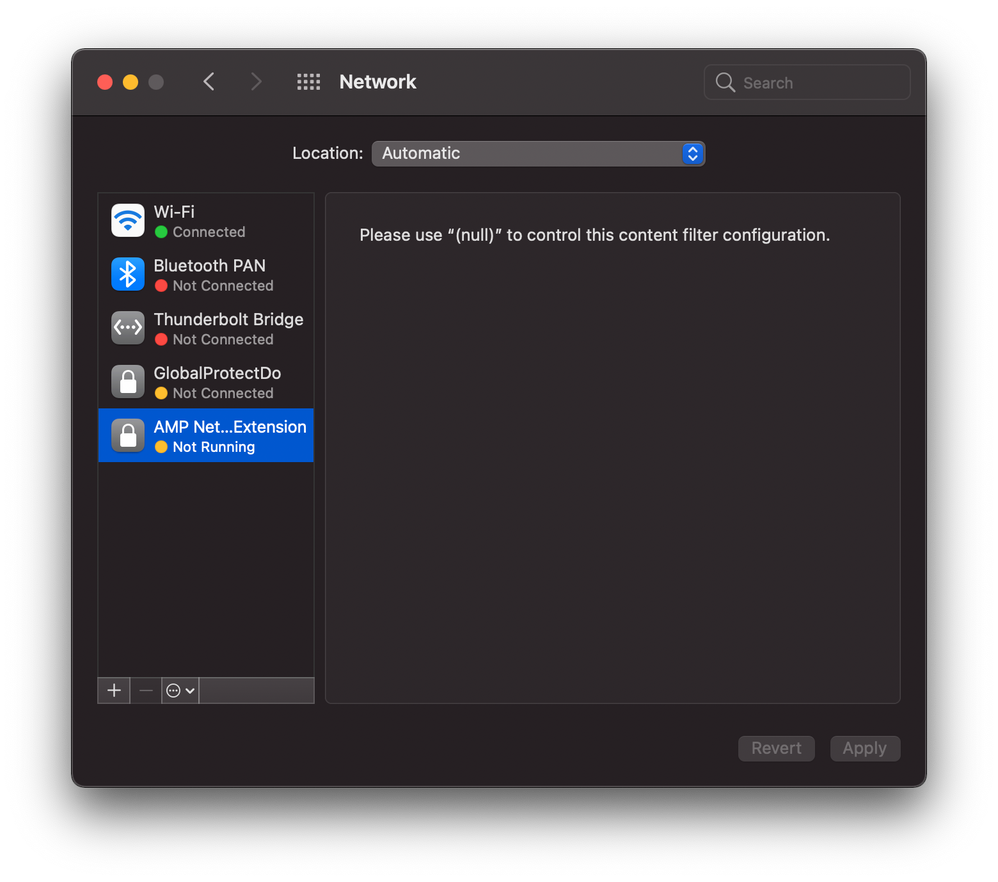
Posted on 12-10-2020 08:58 PM
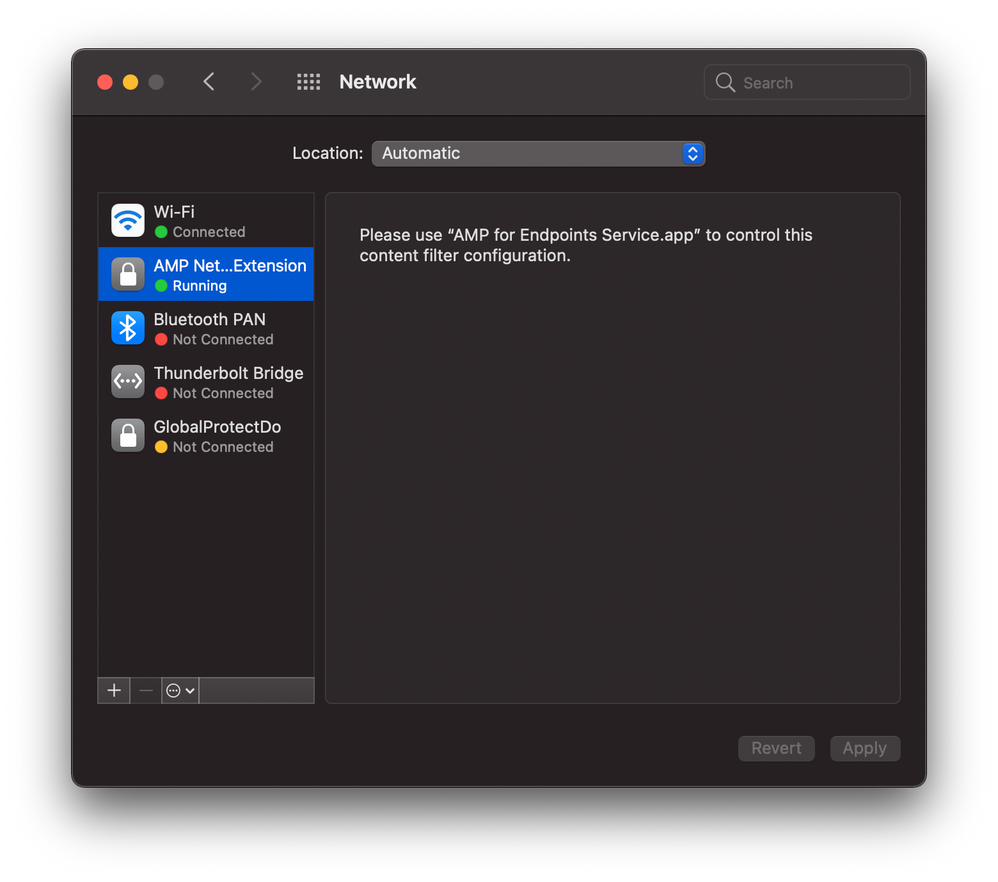
@ajc196 Thanks for that help. I missed the FilterOrder so and I had a few things not typed in correctly. I can now get the install to go without that web filter prompt which is good but I noticed that the filter is inactive in my network settings - see the screen shot I'm attaching to this post. Also on a system without the web filter in the config profile where I had to click on the Allow, the web filter entry is green and the text is not "null" but says "AMP for Endpoints Service". Is the web filter entry in your Network settings showing it's active?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-10-2020 09:08 PM
@ajc196 Did a reboot and now it's green and the text is there. Rebooting fixes this as well. One thing to note that since this is enforced through a config profile, you can't remove it. (The minus sign is greyed out.) New screenshot. Now I'll go on to the next problem. Thanks for the help.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
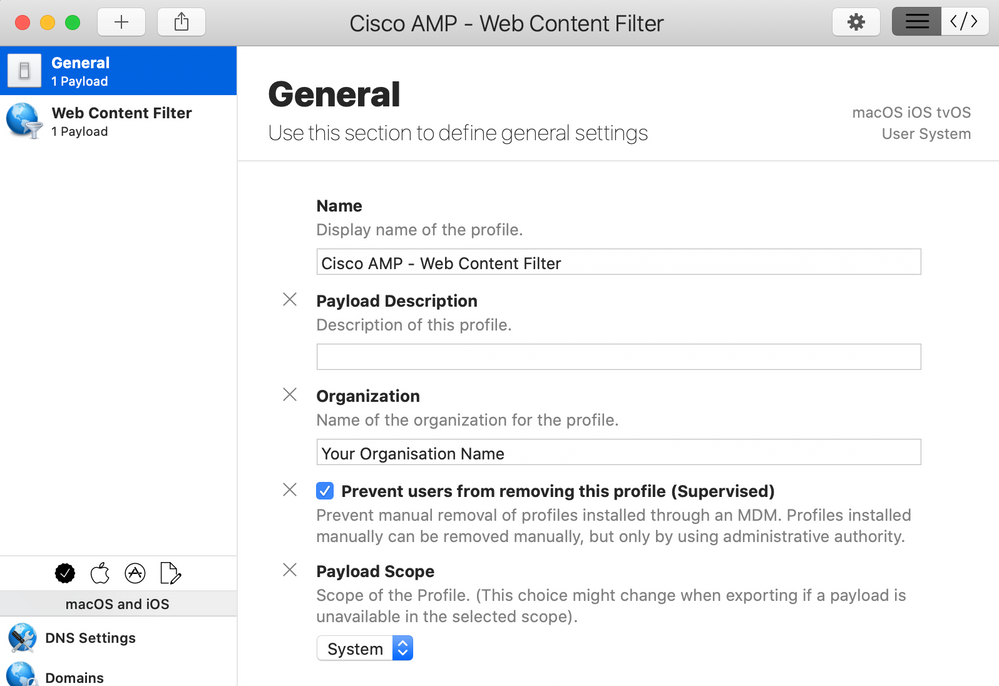
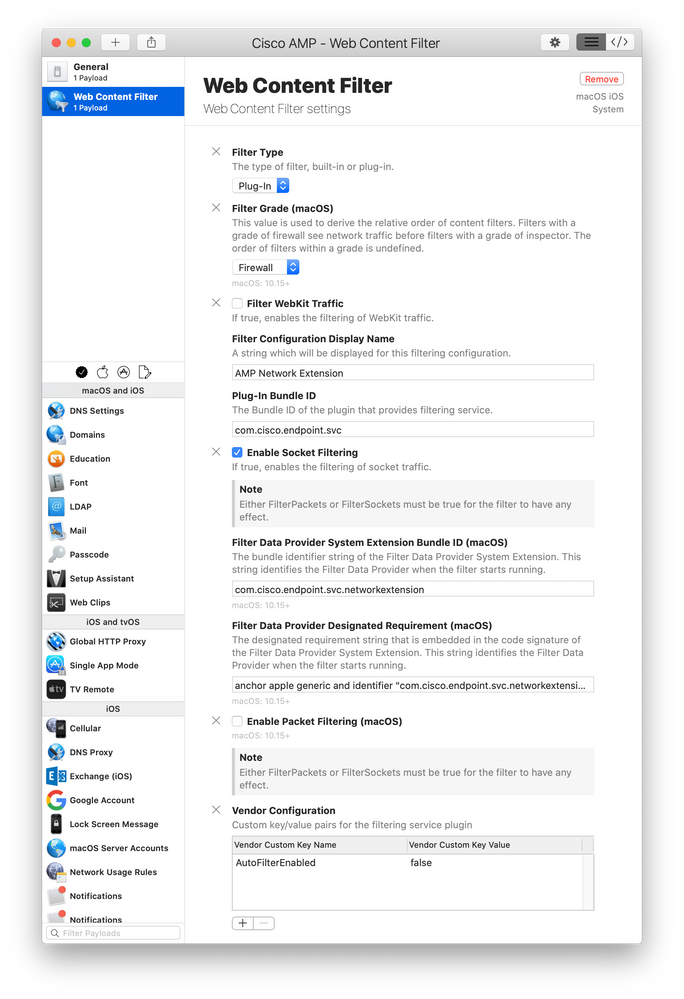
Posted on 12-16-2020 12:19 AM
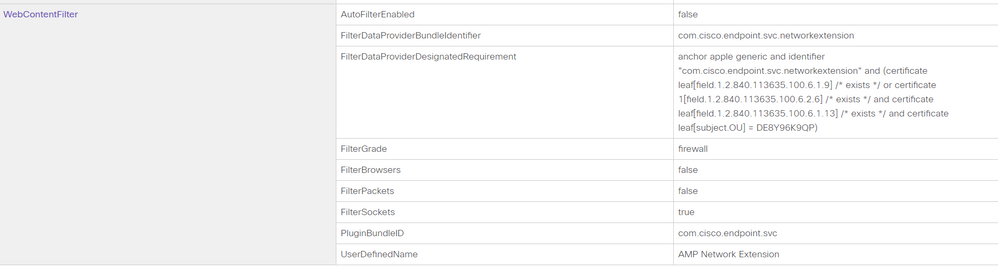
We are not yet on Jamf Pro 10.26 and I needed to fix this quickly so I used Profile Creator. I worried about the Custom Data fields shown by @ccliff and @ajc196 as according to https://developer.apple.com/documentation/devicemanagement/webcontentfilter the fields they had as custom are just part of the spec. However, even for Profile Creator, the field AutoFilterEnabled was not listed so I put it in the VendorConfig area but I suspect that's wrong. The default value for AutoFilterEnabled is true so even though we set it to false, I wonder if the value of AutoFilterEnabled is actually true. Also, why would you set it to false? Surely you want it on?
Here's screenshots if anyone else needs to make the Configuration Profile outside of Jamf Pro. I signed it using my Apple Developer signing certificate so it wouldn't get messed with and then uploaded it into the Jamf pro
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-06-2021 11:55 AM
@ccliff There's been a bunch of updates on here but are you able to post a few screenshots of your configuration that you have working? I've been trying to get it configured but the Web Content Filtering is definitely throwing me for a loop. Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-23-2021 02:11 AM
Hey guys,
the profile seems to be failing on the new M1 MacBooks as they handle kernel extensions differently. Does anyone have a new working profile for M1 devices?