Deploying FortiClient
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-04-2020 03:43 PM
Has anyone had any experience in deploying Fortinet's FortiClient to computers? I get a DMG from our on-prem controller but that doesn't install when I use Jamf Pro to install onto client machines
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-05-2020 04:39 AM
You will need to repackage ALL of the installer files contained in the dmg and add a post install script that calls the pkg file provided so that it reads the config file correctly. You can just copy all to a folder in /tmp and then have the post install script use
installer to run the pkg and then mop up the installer files.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-11-2020 07:47 AM
@andrew.nicholas So what do you use to repackage all the installer files?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-11-2020 09:20 AM
There are multiple tools available but Composer has always been tried and true for me.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-24-2020 02:13 AM
I just opened the DMG and dragged the Install.mpkg to another folder.
Uploaded it to Jamf to create a package.
Next push it with a policy (together with a config package) to the clients
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-27-2020 12:29 AM
I just use a script which also works if you create a upgrade policy.
#!/bin/bash
cd /tmp/
curl -O https://ems_server:10443/installers/version/FortiClient_6.2.7.dmg
hdiutil attach FortiClient_6.2.7.dmg
cd /Volumes/FortiClient/
sudo installer -pkg Install.mpkg -target "/"
cd /tmp/
rm FortiClient_6.2.7.dmg
hdiutil detach /Volumes/FortiClient/- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-13-2021 12:09 PM
This worked with FortiClient 6.2.6, only issue is it doesn't seem to pick up the custom.conf and default.conf settings until after a reboot.
Anyone know what launchagent/launchdaemon to reload to get that to be picked up without a reboot? Or maybe some commandline on it's own to get it to reload the config? It loads up initially unconfigured and unlicensed.
Apparently this is normal as per the documentation. Fun.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-26-2021 07:15 AM
FortiClient 6.4.2 uses an app to download and launch the installer and there's no obvious way to get the .pkg file to use in a Jamf package. How do I go about deploying this? I can't find any help from the FortiClient site. The talk about silent installs via the command line but only for windows. No mention of the Mac.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-04-2021 03:24 PM
@dan.berlyoung I am working through this as well for 6.4.2. I've been working with Packages as we use School, but now the KB is updated to suggest Composer, which seems referenced far more (from Pro users) here in the forums. I sent a request for access to it and am waiting so I can try working with this instead of Packages. For single *.app deployments, Packages has worked well but for anything with like an mpkg linking to other stuff or data deployed to nested folders, plug ins, etc. we haven't had success. I'm hoping that a supported utility like Composer will allow us to break through some challenges with apps like Forticlient.
If you have Forticlient EMS, your EMS deployments should include a dmg when you build them. You can pull the pkg from this by mounting the dmg then just dragging or copying our the pkg. However, as mentioned, the .conf files need to be deployed another way. I don't know how to get the configurations for autoreg host, etc. installed along with the app yet. Will share once I've tested some!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-22-2021 10:55 AM
@MasterNovice I'm having trouble deploying Forticlient 6.4 as well. I made a snapshot of it so I can configure the app with the proper connection settings, but no matter which way I deploy it (.dmg or.pkg), once the app opens up it is just a blank screen. I tried taking a few snapshots to try to get it to work, but each time was the same issue. I also attempted to make the package via Drag and Drop (with no configured settings), but still got a blank screen on the app once it was deployed.
Any advice? Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-22-2021 11:14 AM
@jknopp Just out of curiosity, have you tried rebooting post-install? I've seen Forticlient be dumb and not work right until you reboot...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-22-2021 02:11 PM
@jknopp We've been experiencing that same behavior in lots of Macs recently. No pattern here in terms of operating system or any other software installed that might be interfering . You just open FortiClient (Either VPN or Full) edition and screen goes blank. Tried rebooting, reinstalling, clean installing, you name it, with no use. We are still waiting for Fortinet to introduce some update to the VPN clients.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-22-2021 03:08 PM
@rstasel yeah, I've tried every combination of the like. The process usually goes like: 1) take snapshot 2) install Forticlient, configure app, reboot 3) open Forticlient, confirm everything works 4) take post-install capture, then build the .pkg or .dmg. Any way I seem to do it no dice.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-22-2021 03:11 PM
Would definitely open a ticket with Fortinet. I know the 6.2.x series works fine.
According to their docs, you should just have to have your EMS admin create a custom installer (just like 6.2...)
https://docs.fortinet.com/document/forticlient/6.4.1/ems-administration-guide/757497/deploying-initial-installations-of-forticlient-macos
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-05-2021 09:32 AM
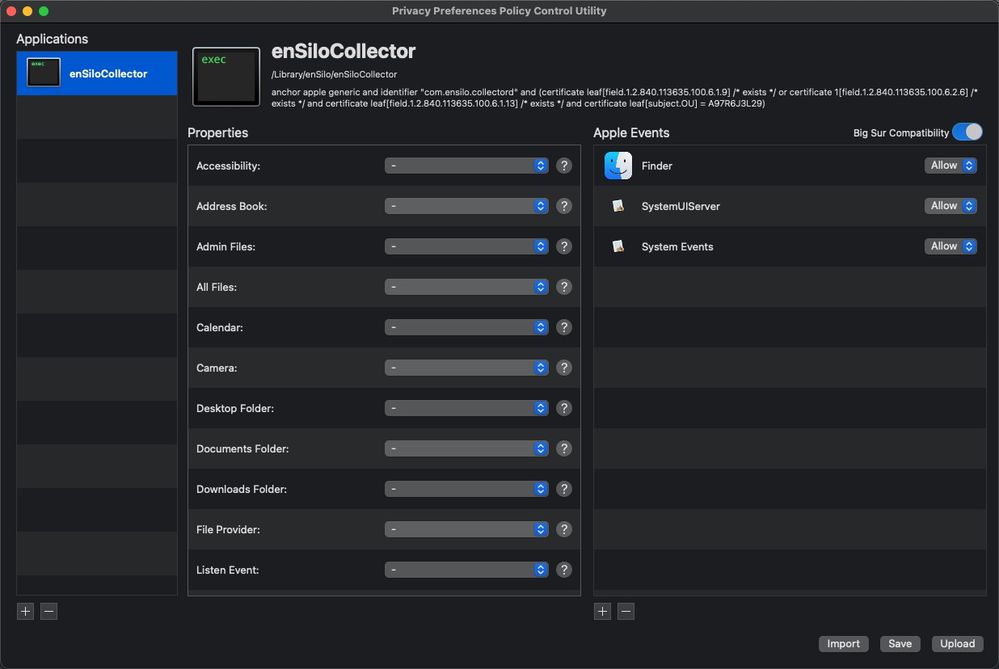
In my case the enSiloClient I am having issues with. I extracted the .pkg
enSiloInstallerOSX_3.1.0.201_FortiEDR_Connect_3.pkg
to my local downloads folder and then uploaded it to JAMF Pro for the install. At first glance it was refreshing seeing nothing pop up at me requesting permission for anything and it looked that it had installed as I saw the icon on my menu bar. When returning to the Admin console the machines state is "Degraded" with the following information.
Warnings: Please approve Fortinet Endpoint Protection and Response Platform Kernel extension in the device.So back to the drawing board when I run the uninstaller I notice that "enSiloCollector" wants access control to my system preferences and finder. And immediately following the uninstall I am hit with "Please Approve enSilo Kernel Extension in System Preferences and then Security Panel.
From this information I gathered I was able to locate "enSiloCollector" and attempted to create a Configuration Profile using the PPPC Utility.app (I have not been having much success with this app since Big Sur) Since I am on Big Sur I toggled the compatibility toggle and proceeded to add the required Privacy Settings
From the information gathered here I now know the following:
Identifier : com.ensilo.collectord
Bunde ID: A97R6J3L2
I deploy the configuration with no success and failure each time:
In the payload (UUID: BC074ED4-9CFA-47DE-BE63-10B973280A90), the key 'Authorization' has an invalid value.I reached out to their support but have not heard back yet anyone have any input that could possibly assist me on this. I would greatly appreciate it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-09-2021 12:56 AM
Is there any chance to make a pkg, drop the install files in a tmp folder an start a silent install?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-09-2021 02:46 PM
Just pinging back to say that @jeroenkahle solution to this helped move me forward with delivery and installation from Jamf school for Forticlient 6.4.2. For some reason I had to run curl with sudo or I'd get a permissions error. I also had to run installer with the -allowUntrusted, presumably because of something with the EMS host certificate I don't undertsand.
I did use the custom dmg created in and hosted on Forticlient EMS, however the install isn't propagating the configuration, specifically for the host management, so the app doesn't auto connect to management. This does not resolve with a reboot. The dmg includes a folder with two config files, custom.conf and default.conf; I verified that these files are configured with the expected data in the dmg that makes it to the client. The custom.conf data looks like it makes it to a custom.plist file used to reference those items, but the management server url and some startup settings are in the default.conf and don't appear to be making it where they should/modifying what they should.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-09-2021 03:02 PM
Ah yes, I have heard of this. I've also heard in Windows the EMS alters the installer msi and results in the cert being broken and not installing without overriding.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-10-2021 03:03 AM
I've been fighting much the same with the 6.4.3 installer. Repacking the installer works as expected but it is the configuration of the associated web filter that has been overly problematic. I've gotten a test config that is able to create a mirror of the config that is installed at the apps first run but always sits as "not running" and refers to the agent as null, where as the one post install without the profile lists as "running" as specifically cites FortiClientNetwork. FortiClient support has been less then helpful and we're also still seeing a random issue seemingly related to the webfilter that drops all network traffic until the agent or computer is killed/restarted which they stated 6.4.3 was supposed to resolve.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-08-2021 01:09 PM
Team does any one have an updated Extension Attribute to share for the new FortiEDR collector trying to collect as many FortiNet Extension Attributes as I can.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-13-2021 11:47 AM
Hi, I'm at the stage when i create a package with composer, and just install it (without jamfpro) on a test device, it started with just blank app. It seems to be installing just fine, but with no success. is there anything that i'm doing wrong? I'm not even trying to load custom settings, just want to remotely install forticlient alone.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-13-2021 11:49 AM
@Fevo I believe I've seen that before (not installing via Composer), have you tried a reboot after installing?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-14-2021 12:53 AM
@Fevo I simply took the install.mpkg and included it as a package in my Jamf policy. Works for me. If you want to include preferences in the installation, I created a PKG with all preferences files and included them in the policy. It is recommended to install the preferences first and then the install.mpkg. Looks like the picture.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-21-2021 01:03 PM
@mickl089 How did you get the preference files to create that pkg? I'm having a hard time finding where the forticlient stores those files. Did you just use Composer and do a before/after snapshot while configuring the app?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-21-2021 11:33 PM
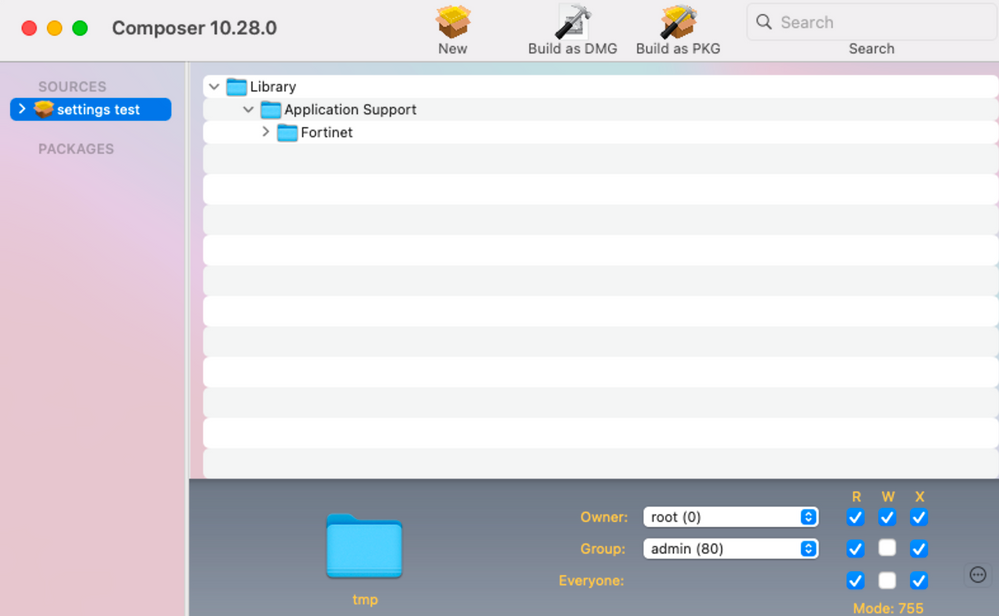
@JonWVC Yes, you´ve got it! I used the composer, with before/after snapshot, so i could find out where the files are located.
Hopefully you can also find the files here: Library / Application Support / Fortinet. I have transferred the complete fortinet folder into the package. Attention: make sure that the settings are also installed first. Afterwards the FortiClient is installed via the install.mpkg, so the client also takes the settings and you don't even need a reboot of the system.
I just remembered that I wrote a tutorial.
Deploy FortiClient
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-22-2021 10:29 AM
@mickl089 Exactly what I was looking for. Thank you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-22-2021 11:23 PM
@JonWVC You´re welcome. Just let me know, if it worked for you. I´ve also created a solution for future updates of FortiClient - to deploy it to users who already have Forti installed. The client blocks repeated installation. If you also need this, I start the translation of the instructions :-)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-25-2021 07:14 AM
@mickl089, I would like that. Hopefully it will set the configuration right for the already deployed machines.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-26-2021 07:20 AM
@jeroenkahle If a kill process script is placed in front of it, this should work even for FortiClients that have already been rolled out.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-26-2021 07:30 AM
Step by Step:
The packaging basically consists of two parts. On the one hand there is an install.mpkg in the DMG file of the manufacturer, this can be pulled separately and uploaded unprocessed in Jamf.
This works either with the tool "Jamf Admin", which is available for download in the Jamf Nation with a registered account, or directly via the Jamf interface in the settings under "Computer Management" and then "Packages".
Basically, the FortiClient policies are now configured so that the settings are installed in a first step. Otherwise the smooth connect will not work.
The packaging for this is best done in a test environment by installing the FortiClient including settings from the DMG and then separating the settings via Jamf Composer (with the snapshot function before and after).
For this purpose, the following files and folders must be packed into a PKG: Picture 1
Updating the client
If a new version of the client is announced, one takes the DMG file, opens this and pulls out the "install.mpkg".
This file is then uploaded to the Jamf server using the method described above and overwrites the old installer.
The policy now looks like this:
Please note that the settings are in the first place, otherwise the login with the client in the VPN does not work, because the config is not loaded.
Jamf now overwrites all policies that included the "install.mpkg" by itself, you don't have to update the policies by hand anymore.
Differences between the different FortiClient policies
For a correct update via Self Service to work, it must be ensured that the FortiClient is not running at the time of the update.
For this purpose, a policy was written that is similar to the normal installation, but still loads a script in advance that kills all Forti processes. Otherwise, the update would throw errors, which would then be acknowledged in Self Service.
The normal FortiClient installer in Self Service, which all users will see who have not yet installed FortiClient on their computer. This will then also serve the AutoDeploy (automatic computer installation via Jamf).
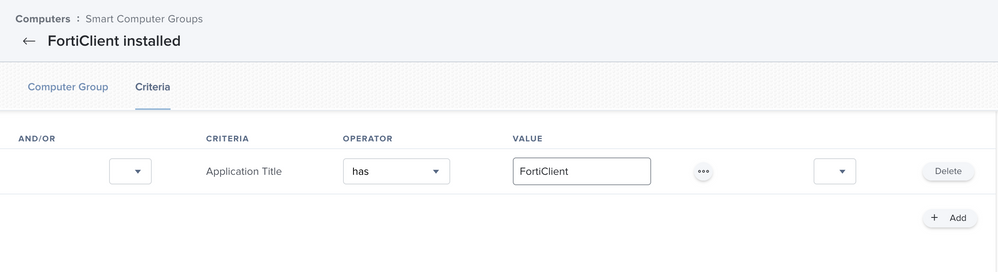
In advance, a Smart Comupter Group was created for this purpose, which contains all computers that do not have FortiClient installed. The scope for this policy was set to this computer group as exclusion. This means that the computer group "FortiClient installed" was defined as an exclusion.
The update variant that is only seen by users listed in the "FortiClient installed" group. That is, the computer group "FortiClient installed" was placed here as a target in the scope.
The Smart Computer Group "FortiClient installed
To ensure a clean separation between the update function and the pure installation, it is necessary to separate the computers for this purpose as well.
Computers that have already installed FortiClient will only see the update function in Self Service, which includes the process kill as the only difference in its policy in addition, so that a clean install over the old version works.
This group can be found in the menu bar on the left under "Smart Computer Groups".
The script that kills the Forti-Client process to be able to apply an update:
A simple two-line command that can be found in the scripts under "Settings" and then "Computer Management" and "Scripts" - named: "kill FortiClient".
Both commands terminate possible running processes of the VPN solution.
killall FortiClientAgent killall FortiClient
Summary or structure of the policy
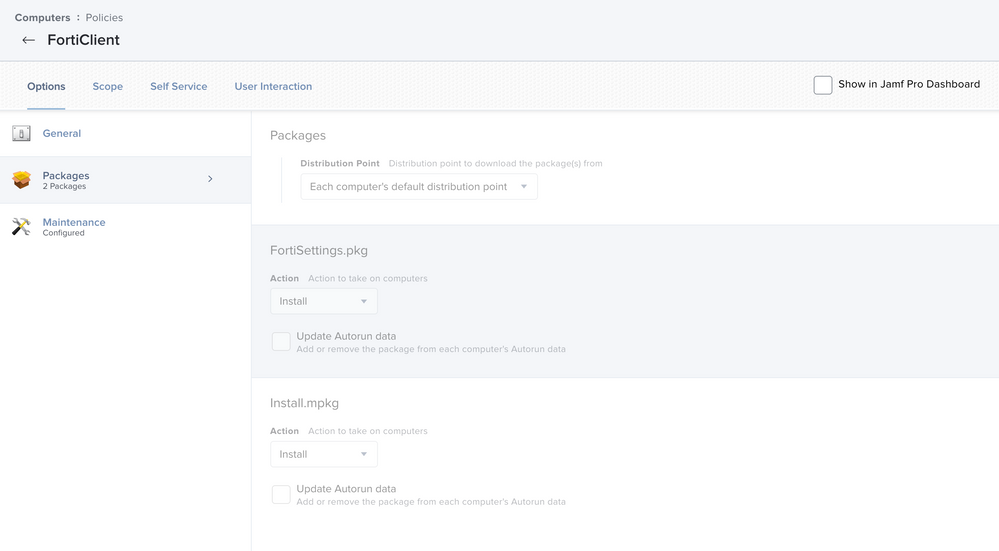
The following configurations are necessary to ensure both installation and update:
Package: FortiSettings.pkg - as described above necessary for the basic configurations Package: install.mpkg - as described above the pure installer for the client Maintenance: this setting ensures that an update inventory is run after the installation is complete. This way Jamf is informed that the FortiClient has been installed and the computer immediately gets automatically into the Smart Computer Group "FortiClient installed" - afterwards only the update version of the tool is visible in Jamf, which contains the already described process kill.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-04-2021 12:12 PM
@mickl089 That is a really well-written walkthrough. I especially like the use of smart groups. Thanks for the info!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-08-2021 09:39 AM
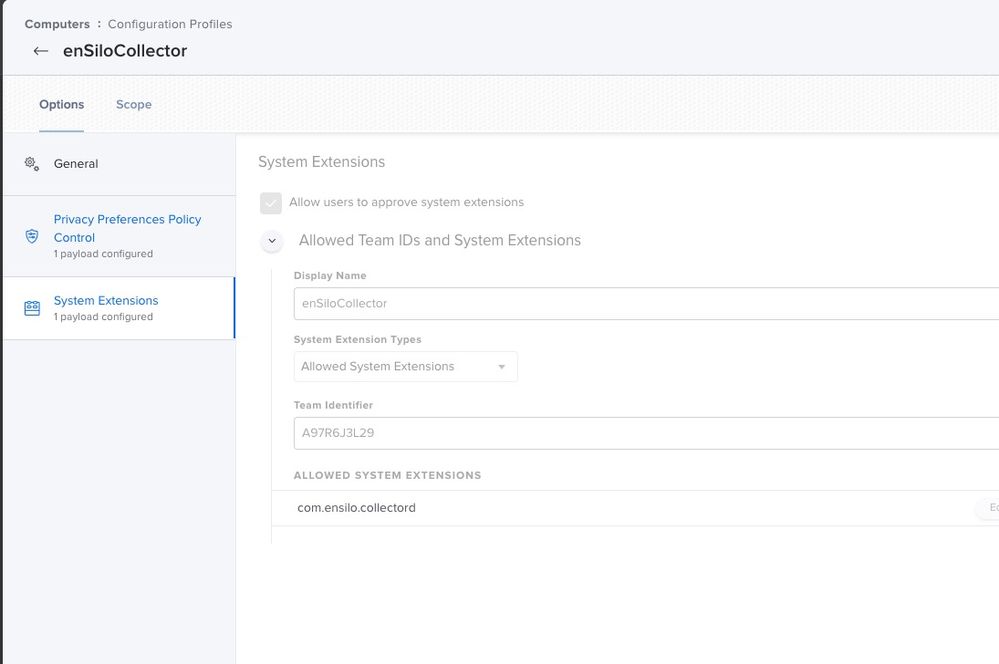
So until this morning, Forticlient didn't need any PPPC for our usage, but something "changed" (inquiring) and now fctservctl wants full disk access. Anyone have a PPPC profile they're using? I'd rather not play cat and mouse with this one...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-08-2021 11:31 PM
@rstasel which version do you use?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-09-2021 07:56 AM
@mickl089 we're on 6.2.x. Looks like "normal" is giving Full Disk access to FortiClient and fctservctl. But not sure that's it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-10-2021 12:43 AM
@rstasel this should also works for you, if you don´t already know this site:
https://docs.fortinet.com/document/forticlient/6.4.4/macos-release-notes/223986/special-notices
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-10-2021 01:51 PM
@mickl089 Thank you! I literally could not find this info... we don't "own" forticlient as a service tool, and on our site, we're literally only using it for VPN. So this is good, thank you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-07-2022 11:37 PM
Hate to bump an old post does this still hold true in v7.X.X and up?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-08-2022 07:04 AM
We haven’t rebuilt our package from 6.4.4 yet, but we’ve observed that 7.x.x requires a system extension and the addition of a few new PPPC items: Fctlsrv2 among them.
We’re deploying the VPN only client, I’ll see if I can find the release guide for 7.0.3, it had some detailed indications about the components that need to be enabled.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-08-2022 01:00 PM
We found a ton of stuff in the release notes and a section called "Special Notice macOS" we did all of those but are still trying to figure out how to do the DMG properly to install via Jamf.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-08-2022 01:05 PM - edited 03-08-2022 01:05 PM
Oh yeah, I see. If the install.mpkg is still available in the *.dmg that's what I plan to use, as per mickl089's process. It's what I did for version 6.4.4 and it worked like a dream.
https://community.jamf.com/t5/jamf-pro/deploying-forticlient/m-p/228591/highlight/true#M216822