Hello,
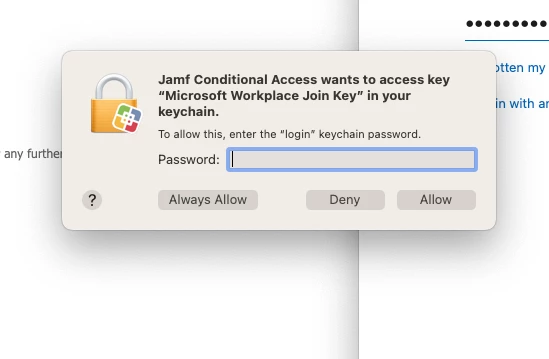
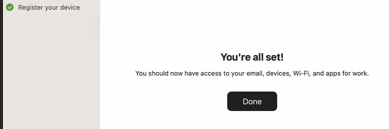
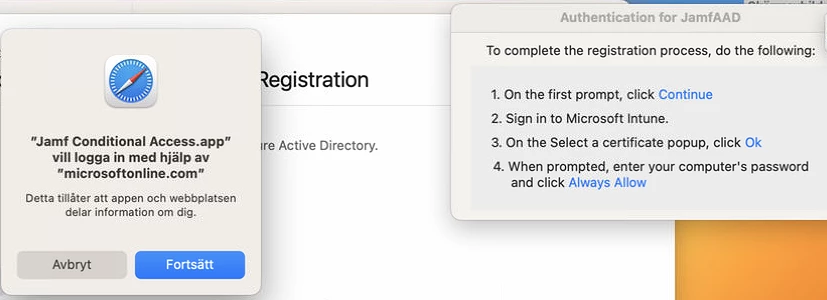
I have followed all the steps in this manual. https://learn.jamf.com/bundle/jamf-pro-documentation-current/page/Device_Compliance.html.
I install portal company from jamf self service.
Then I enroll device to intune.
In intune I see device with compliance state.
Every think look ok, but when I start use browser chrome or safari in aad logs I didn't see complinace state or device ID.
Do you have a same issue?
How to force browser to use intune certificate?