It has been a while since I have looked at this, but reading from Apple's Secure Token documentation:
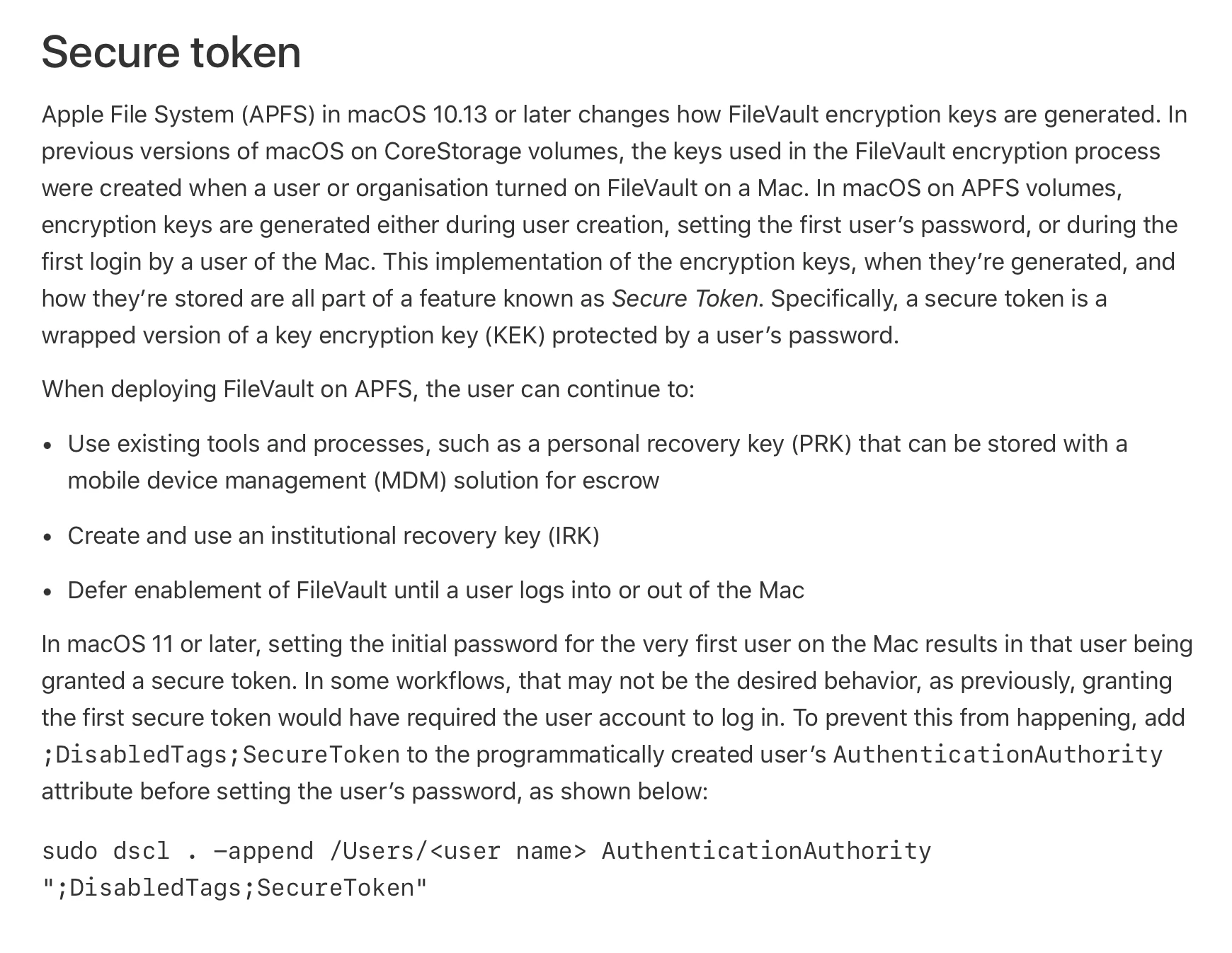
In macOS 11 or later, setting the initial password for the very first user on the Mac results in that user being granted a secure token. In some workflows, that may not be the desired behavior, as previously, granting the first secure token would have required the user account to log in. To prevent this from happening, add ;DisabledTags;SecureToken to the programmatically created user’s AuthenticationAuthority attribute before setting the user’s password, as shown below:
sudo dscl . -append /Users/<user name> AuthenticationAuthority ";DisabledTags;SecureToken"
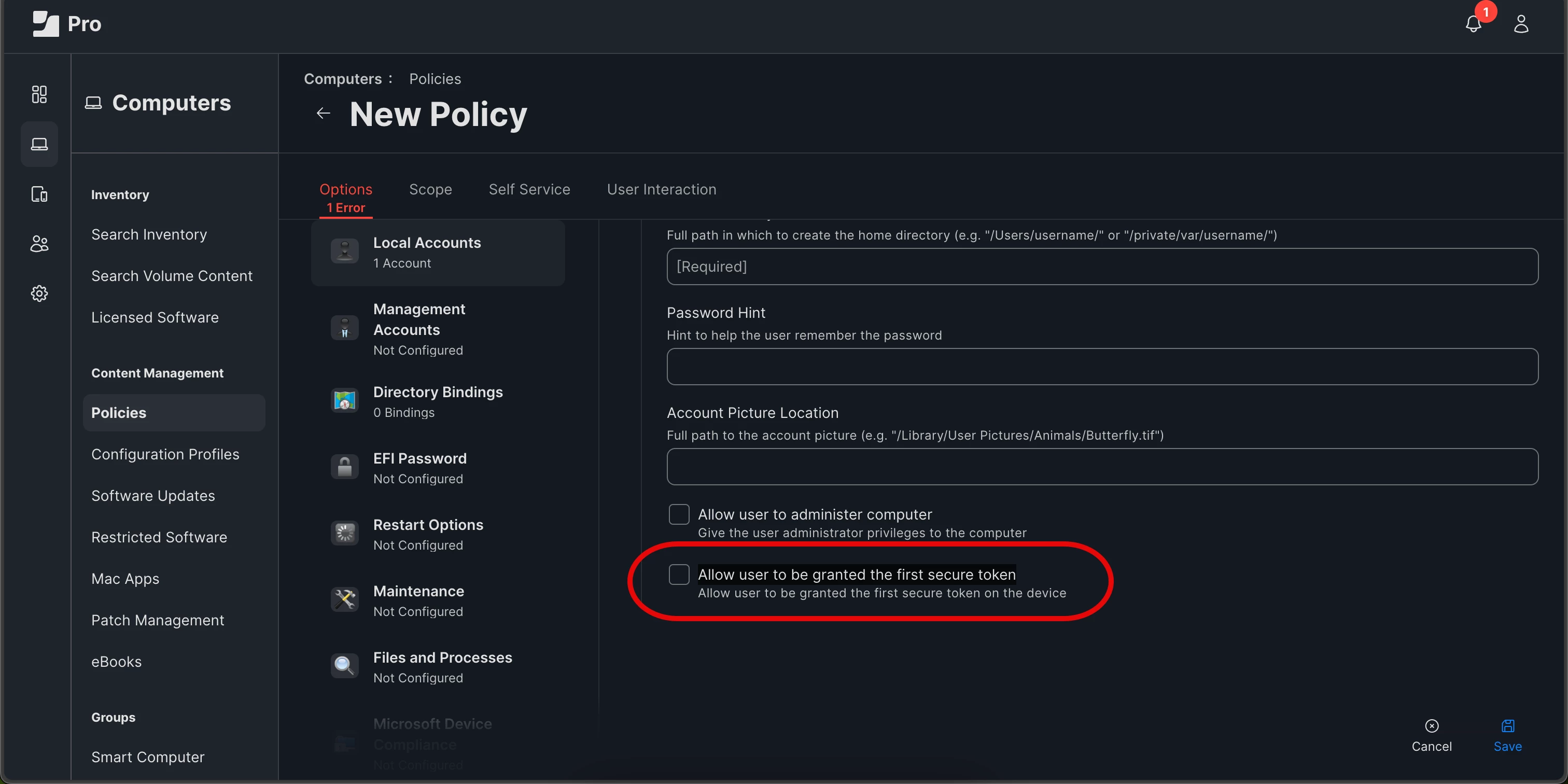
If I am reading this correctly, if you have a policy that creates the first user BEFORE another user is created, that first user will get a Secure Token, if you don't set the tag. In most cases, that is probably not what you want, so Jamf defaults to setting the tag when creating the user.
However, if, for some reason, you want that policy created user to get the Secure Token before anyone logs in, you can disable the Tags, which SHOULD give the first user an ST.
This sounds vaguely familiar, but I could be wrong.