- Jamf Nation Community
- Products
- Jamf Pro
- Re: Enabling SecureToken on management account ?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Enabling SecureToken on management account ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-19-2019 09:24 AM
Hey guys,
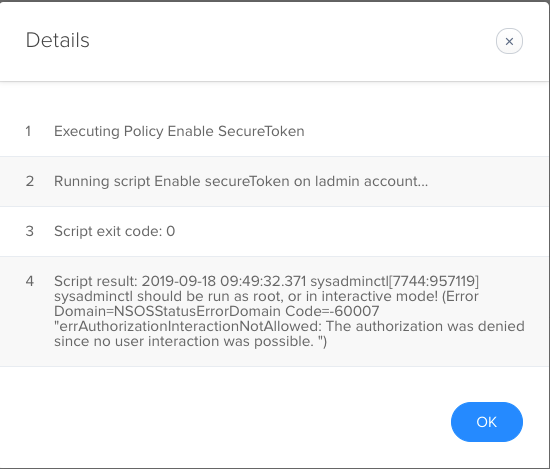
i'm completely new to Jamf and still trying to find my feet there, I have configured PreStage enrollment and it works fine but I want to enable SecreToken on the management account. During the setup assistant user creates an "admin" local user account for themselves and login so they get SecureToken enabled on their account so how can I enable it on the management account that got created using PreStage enrollment process ? I tried this
sysadminctl interactive -secureTokenOn "management account" -password "password"
but it returns this error in the screenshot
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-19-2019 11:44 AM
Following
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-20-2019 12:17 PM
You need two sets of credentials: one for a secure token admin on the system, and one for the account you are assigning a secure token to.
If only the user has a secure token in your workflow, you need their username and password to grant a token to another account.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-20-2019 01:38 PM
One callout... if you have your JAMF environment setup to randomly generate your management account password.
You wouldn't be able to enable SecureToken for the management account.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-27-2020 12:27 AM
@trippmcc the password of the management account is not generated randomly ! is there a way to enable secure token on that account ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-22-2021 04:18 AM
Unfortunately,
There is no way to automate this.. The 1st local account must be logged into physically before it gets the securetoken.
Pain in the ass really... I have set my prestage with locked admin username, then the IT support person will just login to that account. Then, when bootstraptoken came along, it grants securetokens to any new user mobile or local.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-16-2023 11:42 AM
My management account is set to random password so this doesn't help me, but you can add with a script in non-interactive mode:
/usr/sbin/sysadminctl -adminUser LocalUserWithSecureToken -adminPassword HasItAccountPassword -secureTokenOn LocalUserThatNeedsSecureToken -password NeedsItAccountPassword