- Jamf Nation Community
- Products
- Jamf Pro
- Re: FileVault 2 - Generate new key after use
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-11-2015 08:29 AM
Hi Everyone,
First post to JAMFNation and fairly new to Casper - we only had our JumpStart in late May '15. Loving the way this community works. :)
On to business.... Our internal security policies require that when an encrypted laptop (Windows or OS X) have their recovery keys retrieved by an IT analyst, the key must change (generate a replacement) almost straight away. This is so that once the recovery key is used to unlock the laptop it can't be used again so it continues to be secure. This also allows us to track who retrieved the key every time a new one is generated.
I've had a look at the way the JSS manages the FileVault 2 keys. It doesn't appear to generate a new one or track who looked at it.
Is it therefore possible:
1. To have some sort of mechanism that generates a new key after someone looks at the JSS's entry?
2. Audit who looks at it?
Thanks!
Vinny
Solved! Go to Solution.
- Labels:
-
FileVault 2
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-12-2015 12:13 PM
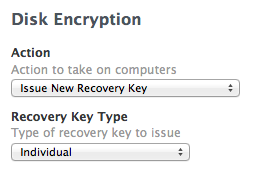
@gachowski Issuing a new Recovery key is not hard at all. Its a built in function now and is part of the JSS Disk Encryption payload in a policy.
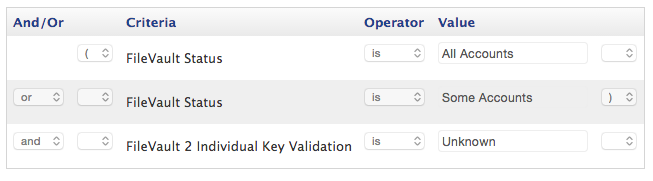
The trouble is actually knowing which Macs this would get scoped to. Right now I don't believe there is any way for the JSS to know that someone viewed the Recovery key, and to put that Mac into a Smart Group so the above action can run on it.
I think this would need to be made into a Feature Request since I don't think its possible to do this today, even with API scripting. The keys themselves are not accessible via the API, and I don't know if there's a way to see that a key was viewed in the JSS.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-12-2015 11:28 AM
You may want to make a feature request for API access to the event logs (if it's not already there) and possibly to add FV2 key access to those logs (again, if it's not already there). If you can get at it from the API, you may be able to script a way to detect a change in the last time the key was accessed, and trigger a policy with the "Issue New Recovery Key" payload.
Or just make a feature request for the whole thing you said above. :)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-12-2015 11:49 AM
I think its really an Apple issue and the base security required of any FDE system. There is really not easy to change Individual FDE.
C
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-12-2015 12:05 PM
The JSS most certainly does audit who accesses a FileVault recovery key. Contact JAMF Support for more information.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-12-2015 12:13 PM
@gachowski Issuing a new Recovery key is not hard at all. Its a built in function now and is part of the JSS Disk Encryption payload in a policy.
The trouble is actually knowing which Macs this would get scoped to. Right now I don't believe there is any way for the JSS to know that someone viewed the Recovery key, and to put that Mac into a Smart Group so the above action can run on it.
I think this would need to be made into a Feature Request since I don't think its possible to do this today, even with API scripting. The keys themselves are not accessible via the API, and I don't know if there's a way to see that a key was viewed in the JSS.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-15-2015 06:40 AM
Hi All,
Thanks for the responses. My skills aren't strong enough with API to mess with that yet so I'll drop a note to the JAMF team to see what they say. As you suggested, it might have to be a feature request more than anything.
I've definitely got the policy working for key re-direction though, where a smart group checks for "keys not known to the JSS".
I'll mark the thread as solved as its not an-built feature as of today.
Cheers again,
Vinny
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-22-2016 06:56 AM
Hi,
I noticed this discussion while trying to figure out myself how to automatically generate a new FileVault 2 key after it has been used.
There is an easy way to create an extended attribute that tells the status of the recovery key for any user.
This simple scrip will return the following values:
- Nokey: The Mac does not have a recovery key
- OK: The Mac has a recovery key
- USED: The Mac has a recovery key and is being used
#!/bin/bash HAS="$(fdesetup haspersonalrecoverykey)" USE="$(fdesetup usingrecoverykey)" if [ "$HAS" == "true" ]; then # echo "Has recovery key" if [ "$USE" == "true" ]; then # echo "Status: Recover key is used " RESULT="USED" else # echo "Status: recover key not in use" RESULT="OK" fi else # echo "Does not have recovery key" RESULT="Nokey" fi echo "<result>$RESULT</result>"
Please notice that value USED will remain like that as long as the user is logged in using the Recovery Key, but as soon as the user resets his password, logs out and then in using the new password, the value will revert back to OK.
Cheers,
Carlos