- Jamf Nation Community
- Products
- Jamf Pro
- Re: FileVault recovery key and McFee MNE import co...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-25-2016 02:10 PM
Hi all
Im trying to create a script that will first generate a new FV2 recovery key then import the new key to McAfee's ePO using one of McAfee's commands.
I've nicked a piece of @Sam.Fortuna reissueKey.sh script (thank you btw!)
I've tried a few ways but i'm not sure how to take the result of the previous command and pass the variable into the McAfee import command, usually i'd use something like recoverykey=$(command here) but that doesn't work in this scenario.
Can anyone advise how get the result of the changerecovey key command
fdesetup changerecovery -personal
so i can use it in the following command
/usr/local/mcafee/mne/bin/MNEMacTool - -import-key RECOVERYKEYHERE
the result of the command fdesetup changerecovery -personal comes out like this
New recovery key = 'TH15-1SSO-NOTM-YKEY-JW8J-63JH'
#!/bin/sh
## Get the logged in user's password via a prompt
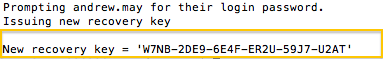
echo "Prompting ${userName} for their login password."
userPass="$(/usr/bin/osascript -e 'Tell application "System Events" to display dialog "Please enter your login password:" default answer "" with title "Login Password" with text buttons {"Ok"} default button 1 with hidden answer' -e 'text returned of result')"
echo "Issuing new recovery key"
if [[ $OS -ge 9 ]]; then
## This "expect" block will populate answers for the fdesetup prompts that normally occur while hiding them from output
expect -c "
log_user 0
spawn fdesetup changerecovery -personal
expect "Enter a password for '/', or the recovery key:"
send "{${userPass}}"
send
log_user 1
expect eof
"
echo "$New recovery key"
# Import recovery key to the ePO
/usr/local/mcafee/mne/bin/MNEMacTool - -import-key TH15-1SSO-NOTM-YKEY-JW8J-63JHSolved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-26-2016 01:03 PM
There are several issues with the script you posted, unless it was only a snippet of a larger script. You need a closing 'fi' in your if/then block for one thing, but maybe that's already there and you just didn't post the whole script.
Second, you aren't capturing the results of the 'expect' script into anything. It needs to be captured as a variable that you can use later.
I can't really test it, but try this-
if [[ $OS -ge 9 ]]; then
## This "expect" block will populate answers for the fdesetup prompts that normally occur while hiding them from output
result=$(expect -c "
log_user 0
spawn fdesetup changerecovery -personal
expect "Enter a password for '/', or the recovery key:"
send "$userPass
"
log_user 1
expect eof
" 2>/dev/null)
newkey=$(echo "$result" | tail -1 | awk -F"'" '{print $2}')
echo "$newkey"
# Import recovery key to the ePO
/usr/local/mcafee/mne/bin/MNEMacTool - -import-key "$newkey"
else
echo "Not the right OS version"
fi- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-27-2016 05:30 PM
@May , I believe I already showed how to get the recovery key by itself in my example above. Pipe it through tail -1 to get just the last line, and the use awk (or cut if you prefer) to get just the key portion. I haven't tested it while issuing a new key for real, but I believe that should work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-25-2016 10:12 PM
Sorry, I need to look into this a little more, but my understanding is that when you enable MNE from the ePO console it sends the command to the client to generate a new key and imports that to the ePO server. At least that has been my experience so far.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-26-2016 06:34 AM
Thanks @jason.bracy
This isn't for escrow of the initial recovery key but so we can re-generate a new key.
It's possible to issue the command directly from the Mac rather than the ePO by using the MNEMacTool binary,
what i'd like to acheive is to first generate a new key, then add the new key to the end of the following command, but alas my script fu is weak
/usr/local/mcafee/mne/bin/MNEMacTool - -import-key addnewkeyhere
once the new key has been accepted it generates a new one and escrows it to the ePO.
from McAfee document
MNE 2.1.0 and later With this release a new MNE CLI (Command-Line Interface) has been added that enables the import of the recovery key to the ePO database On the Mac client, open Terminal.app from the /Applications/Utilities folder. Navigate to: /usr/local/mcafee/mne/bin/MNEMacTool Use either of the following commands with sudo privileges: - -import-key -i Example: sudo /usr/local/mcafee/mne/bin/MNEMacTool - -import-key AXFZ-RXPC-N4OP-5WPR-UUL8-GXH6 NOTE: After entering the command the following message is displayed: The FileVault recovery key is imported to the McAfee ePO server successfully. NOTE: For security reasons, MNE 2.0 and later will change the FileVault key again and escrow the new recovery key to ePO.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-26-2016 12:38 PM
Sorry if I am misreading your script, but from what I can see you are missing 2 things:
1. You don't define "$New recovery key" (also variables can't have spaces)
2. The output of the script is "New recovery key = 'TH15-1SSO-NOTM-YKEY-JW8J-63JH'" you need to grep out the "New recovery key = " and the quotes around the key.
My script skills are probably not great, but I will look at modifying your script when I get back into the office (Currently snowed in).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-26-2016 01:03 PM
There are several issues with the script you posted, unless it was only a snippet of a larger script. You need a closing 'fi' in your if/then block for one thing, but maybe that's already there and you just didn't post the whole script.
Second, you aren't capturing the results of the 'expect' script into anything. It needs to be captured as a variable that you can use later.
I can't really test it, but try this-
if [[ $OS -ge 9 ]]; then
## This "expect" block will populate answers for the fdesetup prompts that normally occur while hiding them from output
result=$(expect -c "
log_user 0
spawn fdesetup changerecovery -personal
expect "Enter a password for '/', or the recovery key:"
send "$userPass
"
log_user 1
expect eof
" 2>/dev/null)
newkey=$(echo "$result" | tail -1 | awk -F"'" '{print $2}')
echo "$newkey"
# Import recovery key to the ePO
/usr/local/mcafee/mne/bin/MNEMacTool - -import-key "$newkey"
else
echo "Not the right OS version"
fi- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-27-2016 03:30 PM
Thanks @jason.bracy @mm2270
This is just a part of the script. For some reason i thought i wouldn't be able to use command substition on that block but it worked, thank you!
#!/bin/sh
if [[ $OS -ge 9 ]]; then
## This "expect" block will populate answers for the fdesetup prompts that normally occur while hiding them from output
NewRecoveryKey=$(expect -c "
log_user 0
spawn fdesetup changerecovery -personal
expect "Enter a password for '/', or the recovery key:"
send "{${userPass}}"
send
log_user 1
expect eof
" 2>/dev/null | cut -c 1-58,80- )
echo "$NewRecoveryKey"The thing i'm trying to figure now is that the result comes back in 2 lines and i need to remove everything else apart from the recovery key, i've tried with cut and sed but it doesn't seem to behave as expected and i'm not sure if it's because there is the blank line above, does cut treat a blank line as individial character positions ?
any idea how i could acheive this ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-27-2016 05:30 PM
@May , I believe I already showed how to get the recovery key by itself in my example above. Pipe it through tail -1 to get just the last line, and the use awk (or cut if you prefer) to get just the key portion. I haven't tested it while issuing a new key for real, but I believe that should work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-28-2016 02:11 PM
Thanks for all your help @mm2270 @Sam.Fortuna @jason.bracy It's working now, (ungracefully i'm sure!). Prompts for the password of any FileVault 2 enabled user, generates a new key then imports it to the McAfee ePO.
#!/bin/bash
#key generation and password prompt used from - https://github.com/JAMFSupport/FileVault2_Scripts/blob/master/reissueKey.sh
## Get the logged in user's name
userName=$(/usr/bin/stat -f%Su /dev/console)
encryptCheck=`fdesetup status`
statusCheck=$(echo "${encryptCheck}" | grep "FileVault is On.")
expectedStatus="FileVault is On."
if [ "${statusCheck}" != "${expectedStatus}" ]; then
echo "The encryption process has not completed."
echo "${encryptCheck}"
exit 0
else
echo "Filevault 2 is enabled"
fi
## Get the logged in user's password via a prompt and generate new recovery key
echo "Prompting ${userName} for their login password."
userPass="$(/usr/bin/osascript -e 'Tell application "System Events" to display dialog "Please enter a FileVault user password:" default answer "" with title "Login Password" with text buttons {"Ok"} default button 1 with hidden answer' -e 'text returned of result')"
## This "expect" block will populate answers for the fdesetup prompts that normally occur while hiding them from output
NewRecoveryKey=$(expect -c "
log_user 0
spawn fdesetup changerecovery -personal
expect "Enter a password for '/', or the recovery key:"
send "{${userPass}}"
send
log_user 1
expect eof
" 2>/dev/null | tr -d "
" | cut -d' -f2)
echo "$NewRecoveryKey"
if [[ $NewRecoveryKey == *"Unable to unlock FileVault"* ]]; then
heading="FileVault2 Recovery Key"
title="CLEAResult Self Service notification"
description="Password error - please run the Self Service policy again
and use the password of a FileVault enabled user"
jamfHelper="/Library/Application Support/JAMF/bin/jamfHelper.app/Contents/MacOS/jamfHelper"
"$jamfHelper" -windowPosition center -windowType hud -heading "$heading" -title "$title" -description "$description" &
exit 0
else
echo "New Recovery key generated"
fi
#Import recovery key to the ePO
echo "attempting key import to ePO"
import=$(/usr/local/mcafee/mne/bin/MNEMacTool -i "$NewRecoveryKey")
echo "$import"
# successful = The FileVault recovery key is imported to the McAfee ePO server successfully.
if [[ $import == *"imported to the McAfee ePO server successfully"* ]]; then
heading="FileVault2 Recovery Key"
title="Self Service notification"
description="New recovery key successfully escrowed to the McAfee ePO"
jamfHelper="/Library/Application Support/JAMF/bin/jamfHelper.app/Contents/MacOS/jamfHelper"
"$jamfHelper" -windowPosition center -windowType hud -heading "$heading" -title "$title" -description "$description" &
else
heading="FileVault2 Recovery Key"
title="Self Service notification"
description="Key import failed - please run Self Service policy again"
jamfHelper="/Library/Application Support/JAMF/bin/jamfHelper.app/Contents/MacOS/jamfHelper"
"$jamfHelper" -windowPosition center -windowType hud -heading "$heading" -title "$title" -description "$description" &
fi- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-29-2016 09:19 PM
Why have McAfee run FV2 rather than Casper? We have both EPO and JSS and are considering having JSS manage the key rather than McAfee.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-30-2016 10:56 AM
Ask yourself if you really want the additional responsibility of managing keys in Casper rather than your McAfee team manage them.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-01-2016 05:59 AM
@swhps Using McAfee and MNE to manage the keys is definitely more complicated than just using the JSS but this wasn't a choice that i'd made. But as @ryanstayloradobe points out, i'm happier now i've done all the work that i can leave the key management to the Security team.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-01-2016 06:35 AM
Thanks for the replies! I can get that it is better for that team to manage also.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-01-2016 04:21 PM
We are also in the process of migrating to MNE. To be honest I am really looking forward to getting the responsibility of enforcing encryption off of my plate.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-06-2016 10:21 AM
It's a no brainer to me, offload responsibility/accountability for FileVault 2 recovery keys.
If there is an entity on the Windows side currently responsible for escrowing Bitlocker keys, and their solution can escrow native FileVault 2 keys, it is most certainly worth exploring.
At some point you've got to decide if what you're doing is really your job...or if you're doing someone else's job for them. And not getting paid for it (subsidy). :)
I would gladly offload FileVault 2 escrow responsibility/accountability to the team who gets paid to do that. ;)
Don
https://donmontalvo.com
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-05-2018 08:00 AM
Is there a way to have JAMF escrow the key and then import that into the ePO? That would be the ideal solution for us.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-25-2019 09:52 AM
Hi,
Thanks for the script sollution!
In McAfee's ePO import recovery key on a client host is enabled for the user.
But in my case unfortunately I've get an error with importing key to ePo server.
"...
New Recovery key generated
attempting key import to ePO
Error: FileVault recovery key is invalid."