Hi all
Im trying to create a script that will first generate a new FV2 recovery key then import the new key to McAfee's ePO using one of McAfee's commands.
I've nicked a piece of @Sam.Fortuna reissueKey.sh script (thank you btw!)
I've tried a few ways but i'm not sure how to take the result of the previous command and pass the variable into the McAfee import command, usually i'd use something like recoverykey=$(command here) but that doesn't work in this scenario.
Can anyone advise how get the result of the changerecovey key command
fdesetup changerecovery -personal
so i can use it in the following command
/usr/local/mcafee/mne/bin/MNEMacTool - -import-key RECOVERYKEYHERE
the result of the command fdesetup changerecovery -personal comes out like this
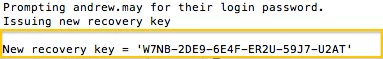
New recovery key = 'TH15-1SSO-NOTM-YKEY-JW8J-63JH'
#!/bin/sh
## Get the logged in user's password via a prompt
echo "Prompting ${userName} for their login password."
userPass="$(/usr/bin/osascript -e 'Tell application "System Events" to display dialog "Please enter your login password:" default answer "" with title "Login Password" with text buttons {"Ok"} default button 1 with hidden answer' -e 'text returned of result')"
echo "Issuing new recovery key"
if [[ $OS -ge 9 ]]; then
## This "expect" block will populate answers for the fdesetup prompts that normally occur while hiding them from output
expect -c "
log_user 0
spawn fdesetup changerecovery -personal
expect "Enter a password for '/', or the recovery key:"
send "{${userPass}}"
send
log_user 1
expect eof
"
echo "$New recovery key"
# Import recovery key to the ePO
/usr/local/mcafee/mne/bin/MNEMacTool - -import-key TH15-1SSO-NOTM-YKEY-JW8J-63JH