Hi,
How do you force an Xprotect version update?
Trying:
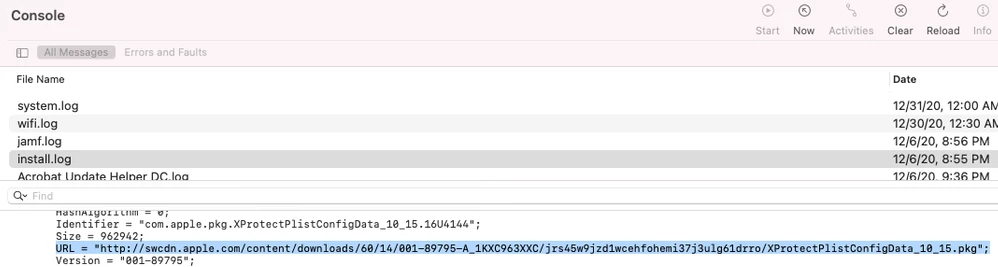
softwareupdate --background-criticaloutputted the following:
softwareupdate[92845]: Triggering background check with forced scan (critical and config-data updates only) ...
But running:
defaults read /Library/Apple/System/Library/CoreServices/XProtect.bundle/Contents/Info.plist CFBundleShortVersionStringshows an older version of XProtect
For our labs we updated to 10.15.7 using the Combo and Supplemental PKGs but the Xprotect version remained an old version.
We like to control the software update process so we have everything unchecked in Software Update
Not sure if that has something to do with Xprotect being unable to update even when running softwareupdate --background-critical from the Terminal.